https://www.alojapan.com/1274772/in-rural-japan-railway-stations-and-empty-properties-repurposed-to-serve-tourists/ In rural Japan, railway stations and empty properties repurposed to serve tourists #Bustay #BustayJapan #ConvertedTrainStations #EnsenMarugoto #InnMyLife #Japan #JapanRailways #JapanTourism #JapanTravel #JapaneseUnmannedTrainStations #JrOmeLine #MarugotoHotel #Okutama #Ome #RuralJapan #RuralJapanRenovatedHouseStay #Satologue #Shizuoka #ShizuokaPrefecture #tenryu #TokyoAdventureLine #TrainStationHotel #travel #UgusuInformationCentre #UnstaffedTrainStationsInJapan
#ome
ジョン スメドレー×オーメ、“藍のグラデーション染め”ふんわりウールニット
https://www.fashion-press.net/news/133219?media=line
#fashionpress #ジョン_スメドレー #JOHN_SMEDLEY #オーメ #ŌME #ファッション #アイテム #ウール #ユニセックス #メリノウール #ワンエルディーケー中目黒 #1LDK_Nakameguro #ハウス_オブ_ロータス_玉川タカシマヤS_C #HOUSE_OF_LOTUS_Tamagawa_Takashimaya_SC #ユナイテッドアローズ_ウィメンズストア_麻布台ヒルズタワープラザ #UNITED_ARROWS_WOMEN_S_STORE_Azabudai_Hills_Tower_Plaza
🔬 We are proud to announce that @nfdi4bioimage will be represented at the 25th International Meeting of the European Light Microscopy Initiative with posters and talks on various topics.
We look forward to seeing you in Heidelberg in June and discussing with you topics like #FAIR spatial data and #NGFFs like #OME-Zarr.
If you didn't get a spot to attend #ELMI2025 onsite, you can still register to attend virtually until April 27.
👉 https://www.embl.org/about/info/course-and-conference-office/events/elmi2025/
Ever wondered if you could access large bioimaging data via a browser on your mobile? The #OME-NGFF specification of a cloud-ready file format for large N-dimensional arrays makes it possible! Watch this demonstration⏬ - loading a 221 GB dataset from the OME-NGFF challenge on a smartphone! 😍
🔜 Ya falta menos para la final nacional de la 61º edición de la Olimpiada Matemática Española #OME, que se celebrará del 27 al 29 de marzo en Gijón Todas las novedades y el desarrollo de esta gran competición se pueden seguir en la página web ⇨ ome2025.uniovi.es #olimpiadamatematica #matematicas
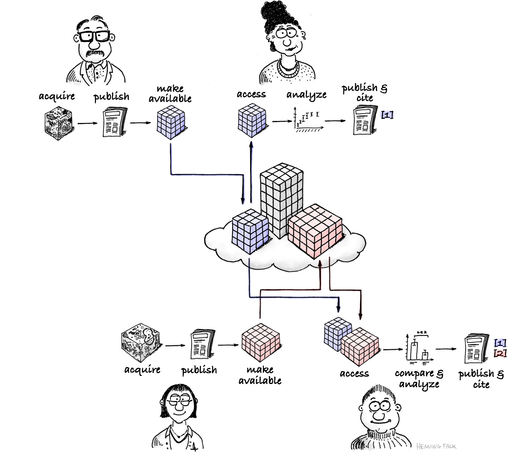
Repositories are essential for #FAIR data. Our invited speakers Frances Wong from
#OME #IDR & Aybüke Yoldaş from
BioImage Archive present recent developments at
@nfdi4bioimage All-Hands Meeting. We're excited to extend our collaborations ➡️FAIR #bioimaging @NFDI
I'm bamboozled by OMERO's APIs.
There seems to be an XML model, a Java (slice? blitz?) API that wraps the XML, a Python wrapper for that Java model (omero.model), an official high-level wrapper for that Python wrapper (omero.gateway), and a third party wrapper for that wrapper (ezomero). Then there's also a JSON API.
#EOSCSymposium2024
marks the build-up of the EOSC Federation ➡️#EOSCEUNode.
@eurobioimaging &
@nfdi4bioimage are happy to present work on
#OME-Zarr
for image data management &
#foundingGIDE's
efforts to harmonize metadata & ontologies in imaging repositories around the globe. Come meet us at the poster.
@ratamero Thanks for the write up. Good to hear what's going on in the world of #OME.
I still smile when my #ParisOfTheNorth T-shirt comes out of the drawer.
Waarom de rijke ome Piet minder straf krijgt dan de buurjongen
Ohai lieve studenten! Vandaag ga ik jullie vertellen over iets wat best wel oneerlijk is. Het gaat over waarom de rijke ome Piet minder straf krijgt dan de buurjongen. 😔
Wat is er aan de hand?
J...
🌞 Leer verder: https://leeralles.nl/waarom-de-rijke-ome-piet-minder-straf-krijgt-dan-de-buurjongen/?feed_id=1677
#BUURJONGEN #DAN #KRIJGT #MINDER #OME #PIET #RIJKE #STRAF #WAAROM
क्या है ओटिटिस मीडिया विद इफ्यूजन बीमारी? जो छीन सकती हैं सुनने की शक्ति
#OtitisMediaWithEffusion #WhatIsOtitisMediaWithEffusion #CausesOfOtitisMediaWithEffusion #OtitisMediaWithEffusionDisease #OME #WorldHearingDay #EarDiseases #EarProblems
https://newschunks.in/what-is-the-otitis-media-with-effusion/
I posted an RFC for OME-Zarr to adopt Zarr v3. I am currently looking for endorsers of the proposal. If you want to see OME-Zarr use the new Zarr version and sharding, please let me know and I'll add you to the list of endorsers.
https://github.com/ome/ngff/pull/227
#OME-Zarr @ome @zarr
#Moshpit in die Playlist! #einfachyu #music #Musik #spotify #Indie #pop #rap #deutsch #deutschemusik #germanartist #Fckafd #FckNzs #alligatoah #newcomer #trailerpark #kaffkiez #kiz #deutschrap #deutschindie #deutschpop #newmusic #newmusicfriday #singing #gesang #lustig #comedy #politik #ome #ometv #omegle
We are delighted to announce that together with @ome and @CRGenomica Training Team, we are running the OMERO workshop in a hybrid mode from 7-8 November 2023. Registrations are now open. More info 👇
https://www.crg.eu/en/event/coursescrg-omero-workshop
Reboosts appreciated.
#Cryptofail can happen for larger organizations, too: #Microsoft #Office365 email message #encryption (#OME) uses AES cipher in Electronic Code Book (#ECB) mode of operation for protecting the OME encrypted messages.
The ECB mode encrypts plaintext blocks independently, without randomization; therefore, the inspection of any two ciphertext blocks reveals whether or not the corresponding plaintext blocks are equal. What this means is that repeating parts of the message get encrypted to identical values revealing structure of the messages. It also will allow creating “fingerprints” of messages, where the relationship of repeating patterns can be used to infer similarity of different messages.
To make matters worse, in addition of keeping the encrypted message in the email server itself, OME by default also sends the encrypted message as an attachment to the recipient. While email typically does best-effort TLS encryption, in practice email transmission cannot really be considered secure. In practice this means that the poorly encrypted messages can be analyzed by anyone who ever managed to intercept the email message or happens to run into any of the OME encrypted messages at a later date. This allows actors who either have large collection of email traffic or who can access the email messages to analyze messages after the fact.
When I approached Microsoft about this flaw, they awarded me $5000 bug #bounty and then proceeded to do nothing. As far as I know the flaw is still present in Office 365 today. I have no clue why Microsoft refuses to fix this flaw, but I presume the reason is that it would break backwards compatibility.
The included sample images and the corresponding “encrypted” version of it were procured by sending an OME protected message with Outlook and then extracting the image from the RPMSG attachment.
I set my Fiji to dark mode and now I have regrets.
Honored to be 1 of 40 recipients of a 2-yr #cziscience #EOSS5 grant to continue work on #OMENGFF 🎉
#OME #Zarr @GerBI and #NFDI4BIOIMAGE are dedicated to the development of scalable data repositories for #bioimaging