Wrapped up an incredible time teaching #PatchDiffingInTheDark in Austin, TX with
@_ringzer0
! The city didn’t disappoint—amazing food, friendly people, and my first autonomous vehicle ride!🤖 🚗✨ #waymo
#patchdiffinginthedark
#EverydayGhidra virtual course with
@_ringzer0
just wrapped up! 😅 Huge shoutout to my stellar students 🤓 who crushed a jam-packed CTF. Next stop: Austin, TX for my in-person #PatchDiffingInTheDark course next week. See you at #Bootstrap25 Conference next weekend! 🤠🎯
One more this week!
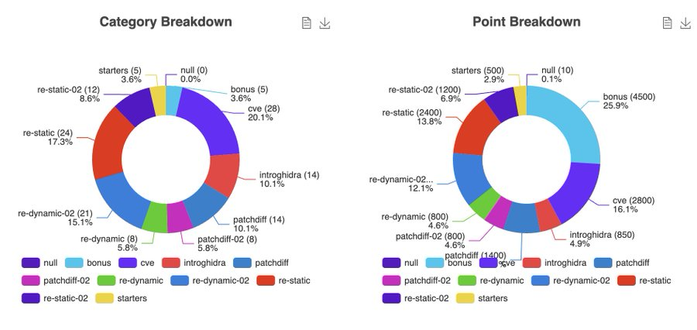
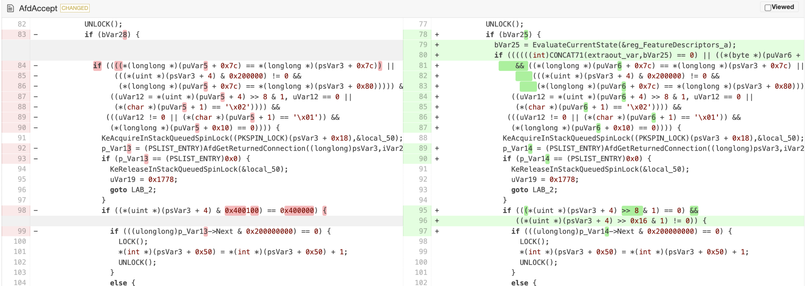
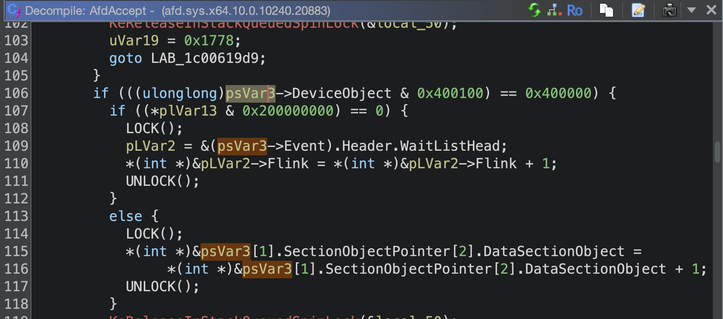
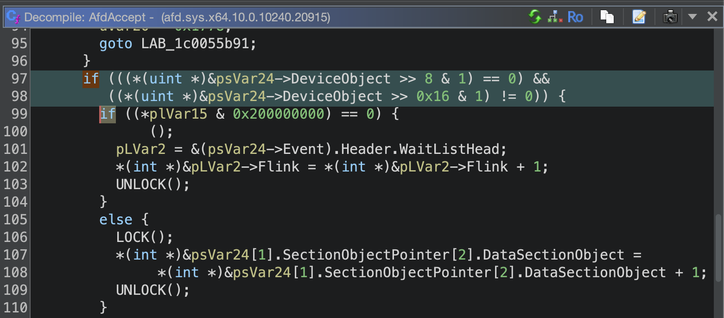
#CVE-2025-21418 2025-Feb Windows Ancillary Function Driver for WinSock 7.8 EoP Heap-based Buffer Overflow
This time in AfdAccept... 🧐
https://gist.github.com/clearbluejar/9c33282f3c579cbc00fa80791a0cb77e
Side by side: https://diffpreview.github.io/?9c33282f3c579cbc00fa80791a0cb77e 👀
Patch diffing when you have no blog post, no Github poc, only binaries! #patchdiffinginthedark
Let's try CVE-2023-36713 with #ghidriff:
An information disclosure for CLFS.sys, not too many functions changed. 🤔
https://gist.github.com/clearbluejar/0f9dc5da3e7d668c06c5022d29e7b55d
There seem to be some refcount changes to memset and memcpy...
memset refcount++ 🧐
https://gist.github.com/clearbluejar/0f9dc5da3e7d668c06c5022d29e7b55d#memset
memcpy refcount++ 🧐
https://gist.github.com/clearbluejar/0f9dc5da3e7d668c06c5022d29e7b55d#memcpy
Looking at the modified function with new calls to memcpy and memset.
https://gist.github.com/clearbluejar/0f9dc5da3e7d668c06c5022d29e7b55d#cclfsbasefilepersistedextendmetadatablockdescriptor-diff
Seems to be an area that is now calling memset on some newly allocated memory (link with a side-by-side view): https://diffpreview.github.io/?0f9dc5da3e7d668c06c5022d29e7b55d#d2h-565510:~:text=_Size%20%3D%20(CClfsContainer%20
We patch diff in the dark to step into the light. 💪
Kudos to
@tacbliw
, who is credited with CVE-2023-36713