🏆 Throwback to #Pwn2Own Toronto 2022: "Routers are just Linux boxes with antennas." So we treated one like it.
At #Pwn2Own 2022, we turned a Netgear RAX30 into a stepping stone for a full LAN pivot. Story: https://neodyme.io/en/blog/pwn2own-2022_router_rce/
#pwn2own
Irgendwie verstehe ich das Problem nicht: Wieso wird etwas auf einen Lautsprecher KOPIERT? 🤔 Es wird doch "nur" gestreamed :mastoshrug:
#Sonos-Lautsprecher: Weitere #Pwn2Own-Lücke gestopft | Security https://www.heise.de/news/Sonos-Lautsprecher-Weitere-Pwn2Own-Luecke-gestopft-10423249.html #Patchday
Hackers verdienen €435.000 door exploits in SharePoint en VMware bij Pwn2Own 2025! Cybersecurity blijft cruciaal. #Cybersecurity #Pwn2Own
https://itinsights.nl/cybersecurity/hackers-kraken-sharepoint-en-vmware-e435-000-buit/
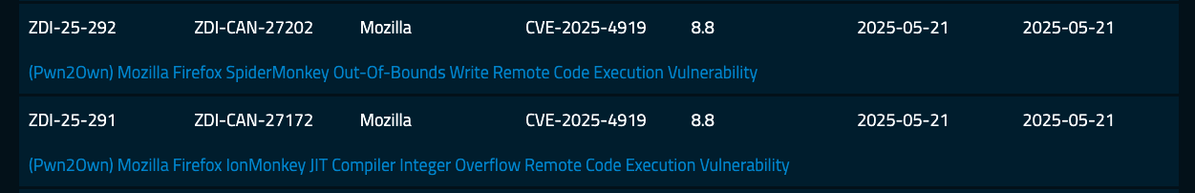
Demonstrating CVE-2025-4919: Now that it's patched, we can show you how Manfred Paul used this code execution bug in the renderer of #Mozilla Firefox to win $50,000. https://youtu.be/TG029NAGKs0 #Pwn2Own #P2OBerlin
We now have evidence that the strict Content-Security-Policy we added to the #Firefox fronted for hardening purposes prevent a Pwn2Own participant from escaping the sandbox! Definitely validates our approach.
https://blog.mozilla.org/security/2025/05/17/firefox-security-response-to-pwn2own-2025/
P.S: Nice work from everyone for being the fastest to ship a fix for the #Pwn2Own findings again.
In another video highlight from day three of #Pwn2Own Berlin, Dung and Nguyen of STARLabs take on Oracle VirtualBox - and they add on a Windows kernel LPE to completely take over the system. https://youtube.com/shorts/vLZLAVjCaIY
In another video highlight from day three of #Pwn2Own Berlin, Nir Ohfeld & Shir Tamari of Wiz Research target NVIDIA Container Toolkit. They also talk about how long they researched the bug they used. https://youtube.com/shorts/iapJlDWMP18
In a video highlight from day three of #Pwn2Own Berlin, Manfred Paul takes on Mozilla Firefox (and his own nerves). https://youtube.com/shorts/Xe9ROvpsqwU
In another video highlight from day two of #Pwn2Own Berlin, Viettel Cyber Security used an OOB Write for their Guest-to-Host escape on Oracle VirtualBox on their second attempt. https://youtube.com/shorts/cczvmsbAeq0
In another video highlight from day two of #Pwn2Own Berlin, Gerrard Tai of STAR Labs SG Pte. Ltd takes on Red Heat Linux and explains why his first attempt failed. https://youtube.com/shorts/vBXACPP9D-0
In another video highlight from day two of #Pwn2Own Berlin, Edouard Bochin and Tao Yan from Palo Alto Networks successfully target Mozilla Firefox. https://youtube.com/shorts/nu6D9Fs3otM
In a video highlight from day two of #Pwn2Own Berlin, Mohand Acherir & Patrick Ventuzelo of FuzzingLabs exploit the #NVIDIA Triton Inference server https://youtube.com/shorts/Xuol5l1GupA
In a video highlight from Day One of #Pwn2Own Berlin, Team Viettel targets the #NVIDIA Triton Inference server. https://youtube.com/shorts/dlPjBPr1E5o #P2OBerlin
At #Pwn2Own Ireland 2024, we successfully targeted the SOHO Smashup category. 🖨️
Starting with a QNAP QHora-322 NAS, we pivoted to the Canon imageCLASS MF656Cdw - and ended with shellcode execution after MMU reconfiguration on the RTOS.
Read the full vulnerability deep dive here 👉 https://neodyme.io/en/blog/pwn2own-2024_canon_rce/
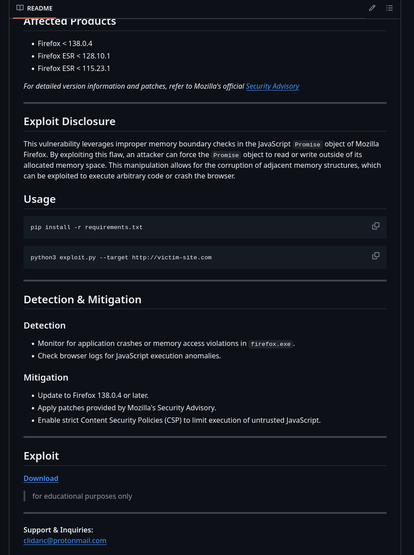
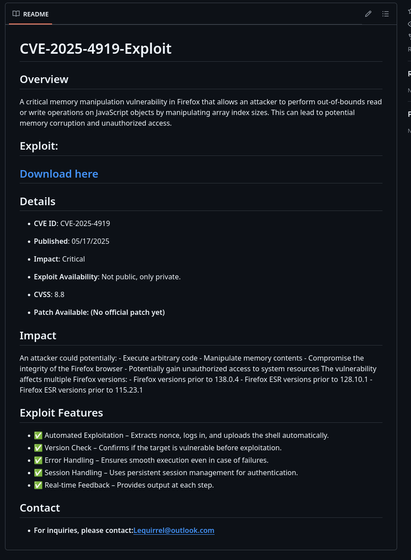
And another: CVE-2025-4918 (associated with the other Firefox 0day exploited at Pwn2Own) also has a new exploit repo created today (5/21/2025) with a single README.md containing an obfuscated tiny URL (when moused over) link with text "Download".
Please be careful looking for the Pwn2Own Firefox 0day exploits on GitHub. It may be malware.
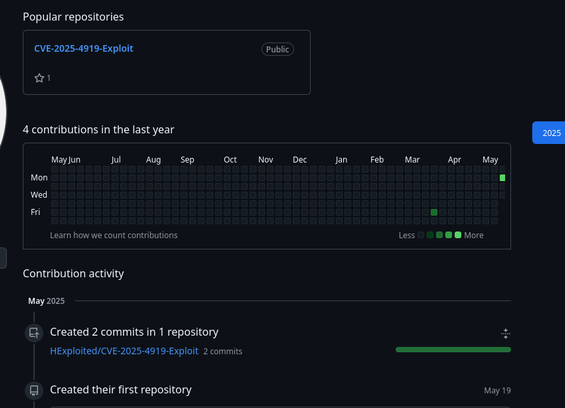
Just ran across a GitHub repo advertising an exploit associated with CVE-2025-4919 in a recently created account (5/19/2025):
https://github.com/HExploited/CVE-2025-4919-Exploit
The repo contains a single README.md file with an obfuscated shortened URL link (when moused over) with text "Download here" to the alleged exploit.
Please don't click the link.
How China Is Building an Army of Hackers. With commentary from ZDI's Dustin Childs and footage from #Pwn2Own Automotive https://youtu.be/8kpnSb4yGR0?si=JxoohyErJkcRXZD5 via @YouTube
🚨 Firefox just patched 2 critical zero-days exploited at #Pwn2Own Berlin! 🦊💻 Hackers earned $100K for finding flaws that could expose sensitive data or enable code execution. Users are urged to update ASAP for protection! 🔒 Read more: https://thehackernews.com/2025/05/firefox-patches-2-zero-days-exploited.html #CyberSecurity #ZeroDay #Firefox #PatchNow #newz
#Firefox :firefox: : #Mozilla schließt Sicherheitslücken aus #Pwn2Own-Hacker-Wettbewerb | Security https://www.heise.de/news/Firefox-Mozilla-schliesst-Sicherheitsluecken-aus-Pwn2Own-Hacker-Wettbewerb-10389266.html #Patchday #Browser #Webbrowser