@orangecon Sounds like a fun and useful training. I might just consider it
🚨 Welcome to BaseFortify, our #ThreatIntelligence, #Infosec & #CVE app that discovers #Vulnerabilities for your infrastructure and enables easy mitigation
🔗 Register for free @ https://basefortify.eu/register or follow us on LinkedIn @ https://linkedin.com/showcase/basefortify/
#Cybersecurity #SysAdmin
CW: Security Advisory
🔌 **EV Charger Vulnerabilities**
We’ve identified four CVEs (2025-5740 through 5743) in a major manufacturer’s EOL EV charging station. No firmware updates are planned, but all issues require authentication—so enforcing strong, unique passwords is your first line of defense.
📜 **Broader Impact**
This case shows why security updates shouldn’t end when hardware EOLs. The upcoming EU Cyber Resilience Act will require manufacturers to provide at least five years of security support—or longer if products remain in use.
🔗 **Read our report:** https://basefortify.eu/cve_reports/2025/06/cve-2025-5740.html
🔗 **Manufacturer advisory:** https://lnkd.in/e_qNR2mF
🔗 **Full DIVD details:** https://lnkd.in/ed6TkSaX
CW: BaseFortify.eu Bumper Ad
🚨 Stay Ahead of Cyber Threats! 🚨
Watch our 15 s video → https://youtu.be/N8CBu4hl-C0
In just 15 seconds:
• Agent-less vulnerability monitoring
• AI-driven risk scoring + MITRE ATT&CK context
• Guided remediation & customizable email alerts
• Unified console & REST API integrations
Start your free plan: https://BaseFortify.eu
#VulnerabilityManagement #Infosec #ThreatIntelligence #Cybersecurity
CW: Security Vulnerability Disclosure
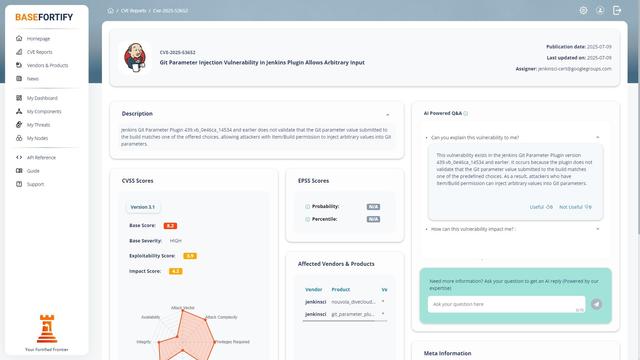
📢 **New CVE**: CVE-2025-53652 – Git Parameter Injection Vulnerability in Jenkins Plugin
🗓️ Published: 2025-07-09 | Last updated: 2025-07-09
✉️ Assigner: jenkinsci-cert@googlegroups.com
🔍 **Description**
Jenkins Git Parameter Plugin 439.vb_0e46ca_14534 and earlier does **not** validate that a submitted Git parameter matches one of the offered choices, allowing attackers with Item/Build permission to inject arbitrary input into builds.
⚖️ **CVSS v3.1**
• Base Score: **8.2** (HIGH)
• Exploitability: 3.9
• Impact: 4.2
🚨 **CWE-20** (Improper Input Validation) | KEV: Yes
⚙️ **Affected**
• `jenkinsci/nouvola_divecloud_plugin` (*)
• `jenkinsci/git_parameter_plugin` (*)
🔗 **Resources**
• NVD: https://nvd.nist.gov/vuln/detail/CVE-2025-53652
• Advisory: https://jenkins.io/security/advisory/2025-07-09/
• Full report: https://basefortify.eu/cve_reports/2025/07/cve-2025-53652.html
❓ **AI Q&A**
Ask me: “How can this vulnerability impact me?” or any other question below! 👇
#Jenkins #CVE202553652 #infosec #cybersecurity #DevSecOps
–––
[Image: Jenkins logo] [Image: Report screenshot]
ICYMI: Microsoft’s July security updates dropped with 132 fixes across a wide range of products, including 14 rated critical. Find more details here: https://blog.talosintelligence.com/microsoft-patch-tuesday-july-2025/
🛡️ Stay ahead of zero-days with BaseFortify.eu: real-time alerts, tailored playbooks & continuous monitoring. Turn Patch Tuesday into proactive defense—register now!
🚨 New article live! Microsoft’s July #PatchTuesday fixes a critical #Pwn2Own-demoed SharePoint RCE, wormable Windows flaws & Office Preview Pane exploits.
👉Dive in now and read our in-depth article: https://basefortify.eu/posts/2025/07/microsoft_patch_tuesday_fixes_pwn2own-found_sharepoint_rce.html 🔒
“It is vital now that vulnerability databases collaborate and work together, not in spite of geopolitical uncertainty, but because of it”: my latest blog post for OSI on our contribution to the public consultation on the mandate of ENISA.
By following, you’ll unlock:
• 🎬 Quick video breakdowns of new CVEs
• 📊 Infographics on emerging vulnerability trends
• 🔔 Instant alerts on our latest annotated reports
• 👀 Sneak peeks at upcoming BaseFortify features
Power up your security today! #ThreatIntel #Infosec 💪
🎉🚀 Hey #InfoSec community! Get crystal-clear CVE deep-dives and vulnerability insights from BaseFortify. Follow us for exclusive updates and content!
▶️ YouTube: https://www.youtube.com/@BaseFortify
📸 Instagram: https://www.instagram.com/basefortify/
💼 LinkedIn: https://www.linkedin.com/showcase/basefortify/ #CyberSecurity
👉Discover AI-powered analysis, step-by-step remediation & proactive threat hunting on BaseFortify.eu.
Register free today: https://basefortify.eu/register #infosec 🚀
💥Annotated reports:
⭐ 2019-5418 (path traversal) → https://basefortify.eu/cve_reports/2019/03/cve-2019-5418.html
⭐ 2014-3931 (buffer overflow) → https://basefortify.eu/cve_reports/2017/03/cve-2014-3931.html
⭐ 2016-10033 (cmd injection) → https://basefortify.eu/cve_reports/2016/12/cve-2016-10033.html
🚨 CISA’s KEV catalog updated July 7, 2025 with 4 legacy CVEs.📢
📄First up: CVE-2019-9621 (SSRF in Zimbra) → https://basefortify.eu/cve_reports/2019/04/cve-2019-9621.html Security teams: review and patch now!
🚨China-linked group Houken hit French organizations using zero-days
All #Invanti based #exploits and serious too. It looks as though somebody forgot to patch. I wonder why only French institutions are #Hacked?
👉Read our annotated reports at: https://basefortify.eu/cve_reports/2024/09/cve-2024-8190.html
🚀Or register for at https://basefortify.eu/register and protect your infrastructure
🚨 CVE-2025-41672 Critical JWT forgery in #WAGODeviceSphere (CVSS 10.0)! Default certs let attackers mint tokens & take full remote control of your devices. Upgrade to v1.0.1 now & replace default keys 🔐
📥 https://basefortify.eu/cve_reports/2025/07/cve-2025-41672.html
BaseFortify.eu 🚀 Your agent-less vulnerability & risk management solution is here!
Watch our new 15-second bumper to see how AI-driven insights keep you one step ahead of cyber threats.
@8bitsecurity Marveling at the “EchoLeak” RAG exploit—honestly, we saw this coming 😉 #AIsecurity #RAG #ZeroClick
🚀 Fortify your digital assets with BaseFortify.eu! 🔒 AI-driven CTI: automated vulnerability management & threat intel, attack surface mapping, enriched CVE reports & news. 🔗 REST API & Base27 ISMS integration. 👉 Register free: https://basefortify.eu/register #CyberSecurity
🛡️🚀 Don’t miss out on real-time alerts, expert CVE reports & community-driven A.I. guidance—register now for personalized feeds and priority support