#zeroclick #internet
https://www.youtube.com/watch?v=9lEBWurEAi0
#ZeroClick
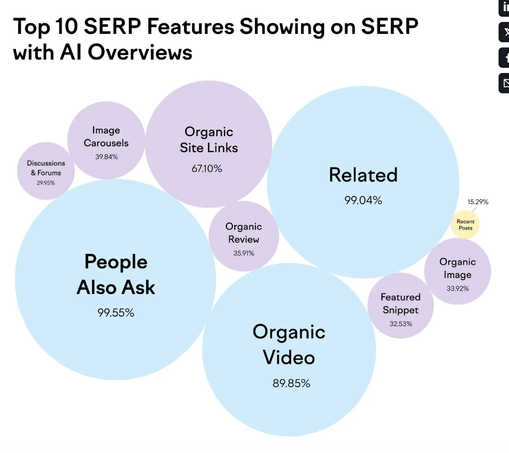
🚨 Over 10M keywords analyzed by @semrush — how AI Overviews are reshaping SEO in 2025:
➡️ 13.14% of queries now trigger AI
➡️ 88.1% are informational
➡️ Most affected: Health, Science, Society
📉 It’s not just about ranking anymore
📈 It’s about being the answer
🔗 Full study:
https://www.semrush.com/blog/semrush-ai-overviews-study/
#SEO #AI #Google #Search #AEO #GEO #DigitalMarketing #ContentStrategy #ZeroClick
🚨 Security warning for Apple users: Several zero-click remote code execution flaws discovered in AirPlay can let attackers spread malware over local networks—especially risky on public Wi-Fi.
To reduce risk:
• Update your devices to the newest OS versions ASAP (iOS 18.4+, macOS Sonoma 14.7.5+)
• Disable “Anyone on the same network” setting in AirPlay if possible
• Use VPNs when on public Wi-Fi networks
#Cybersecurity #AppleAirPlay #ZeroClick #InfoSec #Privacy
https://thehackernews.com/2025/05/wormable-airplay-flaws-enable-zero.html
🚨 One malicious font file could compromise your entire device and you’d never know
Google just patched CVE-2025-27363 in its May 2025 Android security update. It’s a critical vulnerability already being exploited in the wild. The flaw lives inside Android’s font rendering library and allows attackers to execute code without any user interaction or privileges. Just opening a malicious font file is enough.
For high-worth individuals - executives, journalists, public figures - this is the nightmare scenario. No phishing. No tapping links. Just passive exposure.
It can lead to stealth surveillance, credential theft, and full device compromise. And when chained with other exploits, it can leak everything from encrypted messages to authentication tokens.
We’ve seen how mobile devices have become the easiest entry point for attackers targeting influential people. Zero-click exploits like this make it clear: security must be proactive, not reactive.
If you haven’t updated your Android device yet, do it now.
And if you’re in a high-risk environment, take a long, hard look at your mobile defense strategy.
Search Engine Journal: Google’s Walled Garden: Users Make 10 Clicks Before Leaving. “New data shows Google keeps users on its site longer. Visitors now make 10 clicks on Google’s site before leaving for another website. This finding comes from a 13-month study comparing Google and ChatGPT traffic patterns.”
Apple is still feeding unverified media files directly into decoders.
Why hasn’t this been fixed systemically?
Here’s a 2-layer isolation model that would eliminate entire zero-click classes — no decoder rewrites needed:
https://jam2we5b3a.medium.com/this-is-the-future-apple-should-already-be-shipping-054c69d78e50
#infosec #zeroclick #sandboxing #cybersecurity #apple #failsecure
https://www.youtube.com/watch?v=AZ0WM6U48lI
Wormable ZeroClick RCE für das Airplay Protokoll. Jedes Airplay kompatible Gerät ist möglicherweise eine potentielle Gefahr für noch nicht gepatchte Apple Geräte in der Nähe. Viele AirPlay kompatible werden designtechnisch nie ein Update sehen. Die Mischung Wormable, ZeroClick und RCE hört sich nicht gut an. #apple #appleairplay #zeroClick #RCE
📡 2.35 Billion Devices at Risk — Apple’s AirPlay Hit by Zero-Click RCE Flaws
A new set of 23 vulnerabilities, collectively named AirBorne, just exposed Apple’s AirPlay protocol to zero-click remote code execution (RCE) attacks — and it’s a bigger deal than most realize.
According to researchers at Oligo Security:
- Two flaws (CVE-2025-24252 & CVE-2025-24132) are wormable — they can spread malware between devices automatically.
- Another flaw (CVE-2025-24206) bypasses the user interaction requirement, making “Accept” prompts meaningless in certain conditions.
Here’s why this is serious:
- These bugs impact not just iPhones and Macs — but also third-party TVs, speakers, and CarPlay systems that use the AirPlay SDK.
- Attacks only require the target to be on the same network. No clicks needed.
- Compromised devices can be used to infiltrate others on the network — from personal devices to corporate endpoints.
Apple has issued urgent patches across:
- iOS 18.4, iPadOS 18.4, macOS Ventura/Sonoma/Sequoia, visionOS 2.4
- AirPlay Audio & Video SDKs
- CarPlay Communication Plug-in
If you’re using AirPlay at home or at work, update everything now.
Oligo warns that without fast patching, these flaws could be weaponized for:
- Espionage
- Supply chain attacks
- Ransomware delivery
AirPlay is a core feature across 2.35 billion Apple devices — and its quiet ubiquity is exactly what makes this threat so dangerous.
At @Efani, we urge all privacy-conscious users and enterprises to treat zero-click vulnerabilities with high priority. Because you don’t have to do anything to get hacked anymore.
🚨 Security alert! Oligo Security uncovers "AirBorne" flaws in Apple’s AirPlay, exposing iPhones, Macs, Apple TV & CarPlay to zero-click RCE attacks! 🛡️ Wormable exploits, data leaks & more-patch now if you haven’t updated! 🔗 Read more: https://cyberinsider.com/airborne-flaws-expose-apple-devices-to-zero-click-rce-attacks/ #Apple #Cybersecurity #ZeroClick #AirPlay #newz
Apple is still letting unverified media files reach decoders — keeping an entire exploit surface alive.
This 2-layer validator model blocks malformed media before decoding ever begins. No decoder rewrites required. Apple could ship it today.
https://medium.com/@jamweba/this-is-the-future-apple-should-already-be-shipping-054c69d78e50
#infosec #Apple #sandboxing #RustLang #cybersecurity #zeroclick
#Business #Findings
AI overviews reduce clicks by 34.5% · Google’s AI answers send you fewer visitors https://ilo.im/163dez
_____
#Google #SearchEngine #AnswerEngine #AI #SEO #CTR #ZeroClick #Website #Blog #Marketing
wonder if any, or how many, of the #Hegseth chat group also had #WhatsApp with #Paragon #zeroclick?
meanwhile:
WhatsApp patched zero-click flaw exploited in Paragon spyware attacks
Blasting Past Webp - An analysis of the NSO BLASTPASS iMessage exploit
CC: Ian Beer
https://googleprojectzero.blogspot.com/2025/03/blasting-past-webp.html
Oh look, another thrilling tale of zero-click, zero-day, zero-relevance security exploits 🤖🔍. In a shocking turn of events, a secret vulnerability was discovered in a messaging app nobody uses anymore 📱💥. Meanwhile, somewhere in DC, someone is brushing off their old Nokia with a smirk 😏📞.
https://googleprojectzero.blogspot.com/2025/03/blasting-past-webp.html #zeroClick #zeroDay #messagingApp #securityExploits #oldNokia #techHumor #HackerNews #ngated
another image from the threaded link:
Figure 6: Our understanding of #Paragon #WhatsApp #zeroclick attack.
Someone on the algorithmic social media platforms was saying it's a "brave move" to post #zeroclick content that has no links.
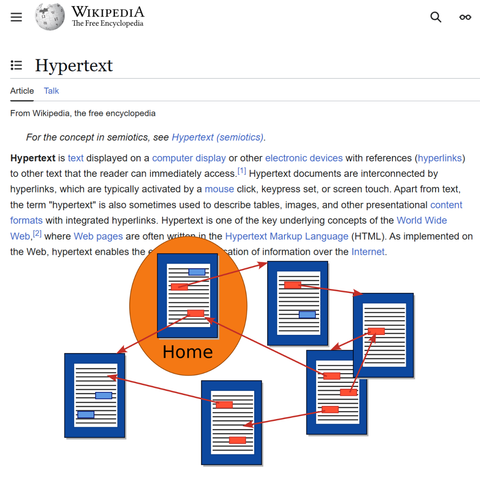
I had to reply with a picture of the #Hypertext Wikipedia article, to demonstrate how these walled gardens have destroyed the fundamental idea behind the web - while still using HTML to render the content of their own service.
There's nothing "social" about a service that downranks user posts with links. We should have a different name for it than "social media".
Meta-owned WhatsApp said it disrupted a campaign that involved the use of #spyware to target journalists and civil society members☝️🤖 #zeroclick
https://thehackernews.com/2025/02/meta-confirms-zero-click-whatsapp.html
The spyware allegedly came from an #israeli company called #paragon Solutions and targeted select users in over two dozen #countries, WhatsApp says.
https://www.pcmag.com/news/spyware-vendor-allegedly-targeted-90-whatsapp-users-with-zero-click-attack
#journalist #ICE #usa #facebook #meta #privacy #surveillance #data #pdf #malware #trojan #zeroclick #IM
Security Week 2503: атака zero-click на смартфоны Samsung
В конце прошлого года компания Samsung закрыла уязвимость, теоретически открывающую возможность проведения атаки на смартфоны компании без ведома пользователя. Недостаточный уровень контроля за входящим контентом в штатном мессенджере мог привести к переполнению буфера. Уязвимость была обнаружена экспертом из команды Google Project Zero Натали Сильванович. Хотя возможность эксплуатации проблемы не была до конца исследована, данный кейс представляет отдельный интерес благодаря двум трем особенностям. Во-первых, баг актуален при передаче сообщений по протоколу Rich Communication Services . Это универсальный протокол, созданный в попытке приблизить функциональность «простых SMS» к возможностям популярных сетевых мессенджеров. Он позволяет пересылать изображения, видеоролики и звук и поддерживается множеством сотовых операторов. Главное, что на большом числе смартфонов (конкретно были протестированы Samsung Galaxy S23 и S24) протокол включен по умолчанию, о чем владелец устройства может даже и не знать.