🚨 RCE Vulnerability in Node.js CI Pipeline Exposed Millions to Potential Supply Chain Attack
Security researchers have uncovered a serious flaw in the Node.js CI/CD architecture — one that allowed attackers to hijack internal Jenkins agents and execute arbitrary code.
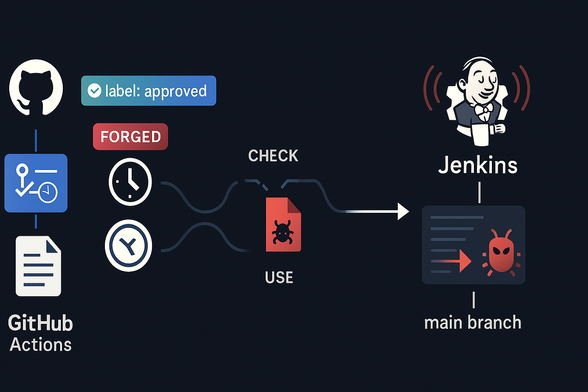
The core issue? A Time-of-Check-Time-of-Use (TOCTOU) vulnerability in the communication between GitHub Actions and Jenkins pipelines. By forging a commit timestamp that predates a maintainer’s approval, attackers could smuggle malicious code past security checks and straight into Jenkins execution.
Here’s what made this attack so dangerous:
- It bypassed the `checkCommitsAfterReviewOrLabel()` function.
- It enabled attackers to compromise Jenkins infrastructure.
- It even risked injecting malware into the Node.js main branch — impacting the entire ecosystem.
Praetorian reported the flaw on March 21. The Node.js team responded fast:
- Restricted access to Jenkins CI.
- Rebuilt 24 potentially compromised machines.
- Switched from timestamp checks to SHA-based validation.
- Audited 140+ Jenkins jobs and patched the commit-queue workflow.
This is a wake-up call for every company using multi-platform CI/CD pipelines:
- Integration between platforms creates invisible attack surfaces.
- Automated approvals and cross-platform handoffs must be treated as critical security boundaries.
Credit to the Node.js team for their transparency and swift mitigation — but the lesson is clear:
If you're not securing the spaces between your DevOps tools, you're leaving the door wide open.
#SupplyChainSecurity #NodeJS #DevSecOps