We are migrating this account to our self-hosted Mastodon server @ disobey.net!
U.S. 501(c)(3) human rights nonprofit and transit ISP supporting internet privacy infrastructure since 2017. 100% volunteer run, 100% donation based.
Tor bridges: https://emeraldonion.org/bridges
Signal proxy: https://signal.tube/#ghostprotocol.net
XMTP relay: https://xmtp.disobey.net
Happy Families: new certificates for faster and easier relay management. Read about how it works and what you can do to speed up the transition.
📢 CDT Europe, as part of the steering committee of the Global Encryption Coalition, joined 88 other civil society organisations, companies, and cybersecurity experts in a letter to the European Commission, raising serious concerns about the future of #encryption in Europe.
🔒 Strong encryption is not a barrier to security, it is a fundamental pillar of it. We need to defend it, not undermine it.
relayor v25.0.0 is released.
This release adds support for the MyFamily successor "happy families"
and improves the prometheus integration feature.
https://github.com/nusenu/ansible-relayor/releases/tag/v25.0.0
Emerald Onion is now hosting an #XMTP node at https://xmtp.disobey.net
You can read more about it here:
- https://xmtp.org
- https://docs.xmtp.org
- https://xmtp.chat
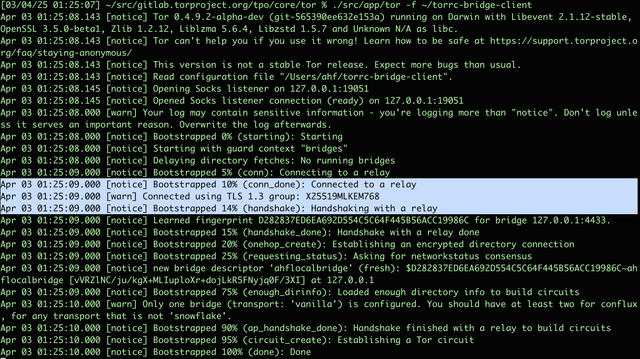
Trying out the Post-Quantum TLS feature (called ML-KEM) in #OpenSSL 3.5-beta1 and #Tor was a success! 🥳
The experiment is using the same setup as we did with #BoringSSL back when they enabled the Kyber768/x25519 TLS 1.3 group: we use a Tor binary, compiled against a PQC-enabled lib(ssl|crypto), to run a Bridge Server locally and connect a local Bridge Client to the server.
The branch used for this experiment is available from https://gitlab.torproject.org/ahf/tor/-/commits/ahf/openssl-3.5-pqc-experiments
Today a long awaited new method to declare tor relay families got merged into tor, the so called "happy families" proposal.
This will make it a lot simpler for relay operators to add relays to an existing family because already running relays do not require any reconfiguration.
The new design also significantly reduces the size of microdescriptors. The old MyFamily design makes up over 80% of microdescriptors.
The new and old design will coexist for a while.
https://gitlab.torproject.org/tpo/core/tor/-/merge_requests/857
goodbye Seattle 😢
We're committed to supporting marginalized and underserved populations by funding work that promotes community-centered connectivity and makes access affordable and resilient.
We are calling on other organizations who see the value in connection and the positive impact that an Internet for everyone brings to join us!
Learn more about our Connectivity Co-funding Initiative:
https://www.internetsociety.org/issues/access/connectivity-co-funding-initiative/
We have news! Sort of sad, but also exciting!
The bad: We can't afford to stay in the Westin datacenter in downtown Seattle. The co-location and transit costs are too high.
The good: We're moving our Seattle infra to California where we have a full rack. We're also deploying a new POP in Amsterdam!
Our exit relays have been in a degraded state for a few months now, and as of this evening they are offline. disobey.net and that WebTunnel bridge is also offline, but it will be back online later this week.
The only Tor infra that we have online right now is our obfs4 private bridge. Our Signal proxy is also still online.
We will not be deploying Tor relays in Europe since the concentration there is too high. Our new exit relays will be hosted near San Francisco.
Two of our three volunteer directors live in Europe now, so we just didn't have the capacity to manage our Seattle infra. And we have plans to deploy better remote management going forward!
Stay tuned for more updates in the coming months!
Veilid Node update!
Veilid v0.4.3 is now available!
✅ Debian packages updated
✅ RPM packages updated
✅ Pypi updated
✅ Rust Crates updated
**Combined Changelogs for v0.4.3 and v0.4.2**
**Changed in Veilid 0.4.3**
This release exists without changes to the Veilid codebase in order to test fixes to the CICD release pipeline.
- CICD
- Fixed broken RPM packaging
**Changed in Veilid 0.4.2**
veilid-core:
- (neequ57) Merged !330 - geolocation feature (off by default) to allow excluding/denylisting route nodes based on geography
- (evelyn) Merged !267 - adding the ability to create dht records with a specified owner key (rust only currently)
- (rivka segan) Merged !335 - fix logic error that used wss when not tls
- New startup/shutdown initialization and component system
- Logs are tagged with the program_name+namespace they are collected in
- No more per-facility log macros, one unified `veilid_log!()` macro for all events
- Switch between subnodes in veilid-cli switches which logs you're viewing
- All global logs and subnode 0 go to console, all other subnodes are accessible via veilid-cli
- Major refactor to add VeilidComponentRegistry as the 'owner' of all components
- Access to components now uses scoped guards for lifetime management rather than loose Arc clones
- VeilidComponent trait makes adding common per-component functions easier
- Unified initialize, post-initialize, pre-terminate, and terminate phase harness
- AsyncCryptoSystemGuard added to make heavy operations happier in async environments
- UDP hole punch needed TTL setting to keep routers from incorrectly making conntracks
- Public address detection was getting stuck in a lock contention, regression from refactor
- PeerInfo caching to eliminate some repeated cloning
- NodeContactMethod cache improvements
- Symmetric NAT and NetworkClass::OutboundOnly were broken. When routing domain address types are known, but there is no dialinfo, that should be OutboundOnly and not Invalid. It's valid to have no dialinfo. Added network class 'confirmation'.
veilid-tools:
- replaced deprecated serde_yaml crate with maintained serde_yaml_ng crate
- Start of VirtualRouter network virtualization
- standalone virtual router binary in veilid-tools (`cargo run --bin virtual_router`)
- IAC-style configuration system for repeatable virtualized network generation
veilid-flutter:
- (kimmy.zip) Merged !343 - Fixes for Windows Flutter build
- Android NDK version requirement is now 27.0.12077973
- Android Gradle version is now 8.10.2, with a minimum of 8.8.0
- Android Java version is now 17
- rust-android-gradle upgraded to 0.9.6
- Kotlin version is now 1.9.25
- API added for create_dht_record with 'owner'
- Breaking change: https://gitlab.com/veilid/veilid/-/merge_requests/353
veilid-cli:
- You can now switch between subnodes easily with the 'connect <N>' command where N is the subnode id
veilid-server:
- You can now run multiple subnodes concurrently in the same process with `--subnode_count=N`
- Up to 256 concurrent each of TCP and WebSocket connections now, up from 32
- Turn off detect_address_changes and upnp by default
veilid-wasm:
- (bgrift) Merged !352 - WASM supports owner on createDhtRecord, also added the getDhtRecordKey function
- Breaking change: https://gitlab.com/veilid/veilid/-/merge_requests/352
- Fixes for heavy sync crypto code, optimizations in debug mode, wasm tests went from 731 seconds to 112 seconds
veilid-python:
- API added for create_dht_record with 'owner'
- Breaking change: https://gitlab.com/veilid/veilid/-/merge_requests/353
- api_connector() now attempts IPC connection to veilid-server before trying port 5959 tcp
- dependencies corrected for pypi package
CICD:
- Updated build machines
- OS Updates
- Rust to 1.81
- Python to 3.12
- Earthly to 0.8.15
general:
- Fix rust-version into workspace cargo.toml
- Earthfile update to 0.8
- Earthfile cache efficiency fixes
Today we are releasing Cwtch 1.15.5!
Cwtch is a privacy-only p2p messenger based on @torproject v3 onion services.
This release is a small bugfixes update, with an upgraded bundled Tor, and a fix that prevented Cwtch 1.15.0+ from running out-of-the box on some linux systems
We also now have an experimental apt repository for Debian based systems!
Changelog/Download: https://docs.cwtch.im/
Please consider donating to @openprivacy so we can continue our mission to build better systems.
Following up on the recent news about the U.K. government attempting to force Apple to backdoor its cloud encryption, Alex Stamos and I wrote this op-ed in the WSJ. https://www.wsj.com/opinion/u-k-kicks-apples-door-open-for-china-encryption-data-protection-deb4bc2b?st=uG1z3q&reflink=article_copyURL_share
Supporting Briar on @Liberapay now also supports @sebfloss making new Desktop releases: https://liberapay.com/Briar/
#OpenSSL 3.4.1, 3.3.3, 3.2.4, 3.1.8, and 3.0.16 are out now to fix RFC7250 handshakes with unauthenticated servers, timing side-channel in ECDSA signature computation, and possible OOB memory access with invalid low-level GF(2^m) elliptic curve parameters https://github.com/openssl/openssl/releases/tag/openssl-3.4.1 + https://github.com/openssl/openssl/releases/tag/openssl-3.3.3
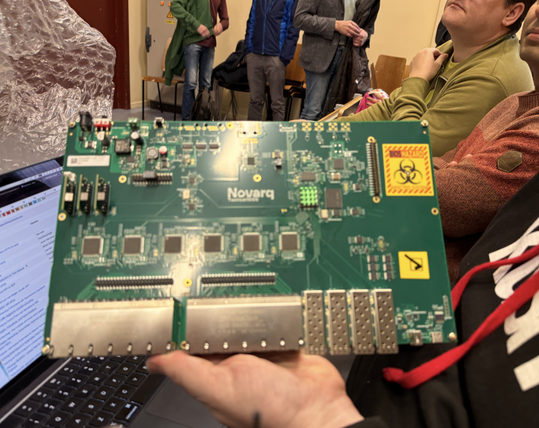
A few years ago, I met Luka who was on a mission to create a fully open source switch with switchdev.
Today, he was at #fosdem and I caught up with him. Here's his beautiful work:
See https://novarq.com/ for more info and stay tuned as they move from working prototype to the production line.
We are decommissioning our obfs4 bridges in Seattle and replacing it with one in California.
This new obfs4 bridge is a private bridge, meaning users must know of its existence in order to use it. Our former obfs4 bridges were "public" and could be fetched from Tor Project.
Please feel free to use and share it with anyone who would like to have a secure first hop onto the Tor network.
https://emeraldonion.org/bridges/
The old Seattle obfs4 bridges will remain online until the end of February.
Just a friendly reminder that @torproject needs more volunteers to run #WebTunnel bridges.
If you're a #fediverse admin, you can safely run a WebTunnel bridge behind your Nginx web server in order to help people access the open internet.
Recently we upgraded our #Tor #obfs4 bridge relay from Ubuntu 22.04 to 24.04. Unfortunately we missed a permissions issue with obfs4 that changed with the upgrade. This kept Tor in a restart loop and prevented anyone from using the bridges. This has been corrected.
This were the errors:
[warn] Server managed proxy encountered a method error. (obfs4 listen tcp 23.129.64.90:443: bind: permission denied)
[warn] Managed proxy '/usr/bin/obfs4proxy' was spawned successfully, but it didn't launch any pluggable transport listeners!
We also have a #WebTunnel bridge that was not affected since it's on the disobey.net server.
VICTORY! After over a decade, a federal court has declared that warrantless backdoor searches of US person’s communications collected under Section 702 of FISA is unconstitutional. https://www.eff.org/deeplinks/2025/01/victory-federal-court-finally-rules-backdoor-searches-702-data-unconstitutional