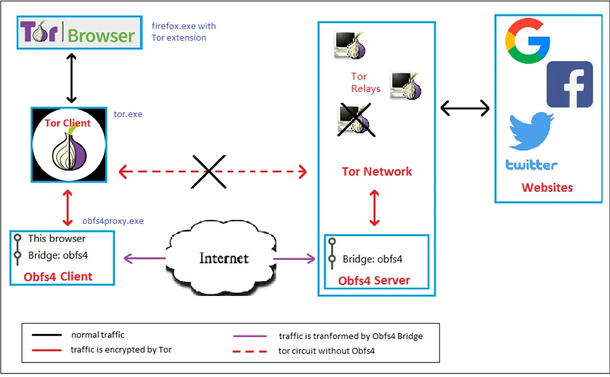
@nono2357 I'm running an #obfs4 proxy on a VPS & followed this. It's amazing how many attempted logins get blocked with #fail2ban. SSH Key Authentication is also amazing.
#obfs4
Request obfs4 bridges via email.
Use moat for automatic retrieval.
Verify fingerprints before connecting.
#Tor #Bridges #Obfs4 #Censorship
We've been hard at work the past few months!
1. Leaving the Westin datacenter in downtown Seattle and moving on from expensive co-location
2. Moving our gear to Fremont, California
3. Bringing on board a few new Advisory Board members, including @whil who has been an incredible help deploying our #Proxmox infrastructure, and @alexhaydock who has been instrumental in deploying our new #Ansible infra, new recursive #DNS resolution infra, and new #Tor exit relays in California! See: https://infosec.exchange/@alexhaydock/114687688286984967 with more updates to follow
4. Installing new co-location with some older low-power systems in Amsterdam for our self-hosted #ActivityPub infra @ https://disobey.net, where we just moved our #Mastodon profile to!
5. Deploying a new #XMTP node @ https://xmtp.disobey.net, and testing a new #DeltaChat relay!
6. Deploying some new #obfs4 private bridges for use in a country who's conducting heavy internet surveillance and censorship, blocking access to @torproject
and today is our birthday!!! we're 8 years old today ^_^ stay tuned for more updates to come!
I am running a #TorProject #obfs4 relay on a #Debian VPS.
So I decided to abandon hosting an #obfs4 bridge on my home network & am investing in a VPS service for $11.00 USD a year.
Rebuilt #obfs4 bridge is now back online!
@tails_live @tails @torproject plus support for meek, snowflake, webtunnel and non-#obfs4 #Bridges seems missing in #Tails.
- It would also help if #BridgeDB allowed to actually select #IPv4 and not just #IPv6 and select ports (i.e. 80 & 443) on top of that.
Cuz to this day I've to yet see an IPv4-#webtunnel #bridge…
So I had been running my #OBFS4 Relay behind my Bell Fiber modem w/o issue & decided to move it behind my #UniFi UXG Lite gateway.
I set the server (running Debian) to DHCP & created the port forwarding rules on the UXG. It looked OK but I started to get the "Your server has not managed to confirm reachability for its ORPort(s) at xxx.xxx.xxx.xxx:ZZZZ.
I troubleshot the issue with my buddy Julien & we found the issue was with Home Hub 4000 (HH4K) and the Advanced DMZ. Even though the UXG was showing a public IP on the WAN Port and the HH4K was showing that the port the UXG is plugged into is configured for Advanced DMZ, traffic was not being passed back & forth.
I disabled the HH4K DMZ & reserved a DHCP IP for the UXG & created a port forwarding rule for the TOR ports on the HH4K to the UXG. Then on the UXG, I created port forwarding rules from the WAN IP, which is now an internal IP, to the Relay server.
After a reboot, things came back online.
In the last 24h we created 80 GB traffic.
Flaky: 9 GB, Obsy: 71 GB
Have a nice evening with free access to the internet.
Obsy and Flaky
In the last 24h we created 81 GB traffic.
Flaky: 10 GB, Obsy: 71 GB
Have a nice evening with free access to the internet.
Obsy and Flaky
@torproject same with #obfs4 bridges: there is no option to say like ports=80,443 or similar, which makes it cumbersome to get said bridges.
- And yes, for people stuck on #publicWiFi and shitty #MVNO|s this is most likely the only way they can get any #Tor connection work through #CGNAT and #firewall|s, as most do #BlockTor and it's associated #ports alongside common #proxy ports like 8000-9999 and anything they can't #MITM that isn't #HTTPS or #IMAP!
And trying to get places to #DontBlockTor that criminalize the use of #Tor is foolish at best.
#WhatsMissing: A tool to check if #TorBridges are still available/online/reachable that one can use either #standalone (with #TorBrowser and/or #Tor Expert Bundle) or on @tails_live / @tails / #Tails.
- Cuz I do run into issues and kinda want to sort #Bridges by availability so I don't waste time on a #TorBridge that is down and also thin-out the list of bridges that ain't online anymore.
Whilst I do acknowledge that @torproject do disrecommend having a huge list of Tor Bridges on hand, I do regularly need them for contacts who are behind a #GreatFirewall and can't #SSH-Tunnel out of it.
- Sadly #BridgeDB doesn't offer good #filtering options so one can't just query types effectively like "I need #webtunnel on #IPv4" or "I can only use Ports 80 & 443 on #IPv6" which may work.
Espechally being able to filter for #IPv4only and not just #IPv6only is something I miss, alongside the filter for #PluggableTransports type as @guardianproject #Orbot seems to only handle #obfs4 and not webtunnel or #meek at all...
- I'm pretty certain that merely pinging a bridge at it's port isn't working as a shure-fire way to check for it's availability.
Лучшие бесплатные VPN для ПК и смартфона 2025 (которые работают)
В последние несколько лет на территории РФ ужесточилась фильтрация интернет-трафика средствами ТСПУ. Сотни сайтов и интернет-сервисов внесены в чёрные списки и заблокированы. Получить доступ к ним можно только через VPN. Однако самые популярные VPN тоже подверглись блокировке. Ограничения можно обойти через канал на собственном зарубежном сервере, купив там самый дешёвый хостинг за пару долларов или уже готовый VPS с установленным VPN (такие объявления есть на Авито ). Если своего сервера нет, то остаётся только прибегнуть к услугам сторонних VPN-сервисов, которые ещё не заблокированы. Лучшие бесплатные VPN из выживших перечислены ниже. Примечание . Эту статью Хабр наверняка заблокирует для пользователей из РФ, в исполнение запрета Роскомнадзора на информацию об обходе блокировок, так что лучше сразу после публикации сохранить её.
https://habr.com/ru/articles/881878/
#бесплатный_VPN #Opera #СОРМ #ТСПУ #Роскоминадзор #РКН #цензура #фильтрация_трафика #IPSec #L2TP #IKEv2 #OpenVPN #WireGuard #ДЦОА #RDPru #обход_блокировок #Psiphon #RedShield #TurboVPN #VPN_Proxy_Master #AdGuard_VPN #AntiZapret #Hola #NordVPN #Shadowsocks #обфускаторы #WARP #Amnezia_VPN #AmneziaWG #Karing #NekoRay #прокси #Exclave #obfs4 #meek #meekazure #Snowflake #WebTunnel #Tor #АнтиЗапрет
@wmd @miqokin I've yet to find a nation that criminalizes @torproject but not #VPN|s that facilitate the same...
- Also commercial VPN providers are relatively easy to detect, filter & block unless they support #SSH-Tunneling.
Whereas #Tor has multiple ways to circumvent #InternetCensorship, includibg multiple #proxy & 9bfuscation systems like #obfs4, #meek, #webtunnel and regular #TorBridges on included, public query-able amd private lists...
Recently we upgraded our #Tor #obfs4 bridge relay from Ubuntu 22.04 to 24.04. Unfortunately we missed a permissions issue with obfs4 that changed with the upgrade. This kept Tor in a restart loop and prevented anyone from using the bridges. This has been corrected.
This were the errors:
[warn] Server managed proxy encountered a method error. (obfs4 listen tcp 23.129.64.90:443: bind: permission denied)
[warn] Managed proxy '/usr/bin/obfs4proxy' was spawned successfully, but it didn't launch any pluggable transport listeners!
We also have a #WebTunnel bridge that was not affected since it's on the disobey.net server.
One thing that @torproject is missing is a way to check availability and reachability of #Bridges with a simple tool.
- This is kinda vital as I do occasionally setup private #bridges and also want to enshure the private #TorBridges list I have is up to date.
Manually adding/removing one #bridge after the other in #TorBrowser and see if those connect is a relatively inefficient process and merely pinging them isn't viable either, espechally on #meek, #obfs4 and #snowflake type bridges.
- Now to make the obvious clear: I'd NEVER publicly list any #TorBridge on my lists.d repo obviously, because that would only harm #Tor...
I'm not even asking for like a fancy tool that is as clean as @micahflee 's #OnionShare but merely a #CLI thing (if necessary I'd build some #bash script) to automatically attempt to connect to said bridge and either spit out an ok or error.
- Something one can just feed with a text file and that'll spit out a different file with ok/working bridges and/or discards the non-working ones from the list.
And yes, this tool is kinda crucial as I want to quickly sift through a load of bridges that work on restricted ports (22, 80, 443) and thus can bypass the #GreatFirewall and #Roskomnadzor filtering...
- So people fleeing can at least safely communicate.
If anyone at #TorProject needs more details, I'll gladly exchange them in a secure manner.
- I also applied for a #gitlab account so I can help improve #documentation (ideally with some nice step-by-step screenshots so even "#TechIlliterates" can i.e. add a #bridge)...
📬 WebTunnel-Brücken: Tor braucht eure Hilfe gegen Internet-Zensur
#Internet #Netzpolitik #digitaleFreiheit #obfs4 #TORNetzwerk #TorProjekt #WebTunnelBrücken #ZensurimInternet https://sc.tarnkappe.info/b67906
So I am running a #Tor "farm" at home. It had consisted of 2 older #Wyse Terminals running #Ubuntu Server Minimized. One server was a #obfs4 bridge and the other was a #Snowflake proxy server.
I decided to port these machines to VMs running Ubuntu 24.04 & ran into some issues. On a whim, I decided to spin up a #Debian VM for the #obfs4 bridge last night, fully expecting to wake up to an issue this morning. I was wrong. The bridge is online & appears to be working. It was always a fight with Ubuntu, not the case with Debian.
So I spun up another Debian VM for the Snowflake proxy & it now also online and working 100%.
All hail Debian???
My physical #tor #obfs4 Bridge and #snowflake Proxy Servers have been retired and replaced by two VMs running on a #ubuntu Server.