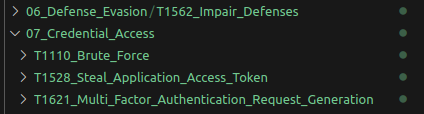
BlueTeam tip: Vulnerable Drivers Block Rules
https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules
#infosec #blueteam #cybersecurity
Blueteam|Detection Engineering|Threat Hunting|KQL
NIST ML Security Publication
https://nvlpubs.nist.gov/nistpubs/ai/NIST.AI.100-2e2023.ipd.pdf
#infosec #blueteam #machinelearning #ai
10 immutable laws of cybersecurity:
https://learn.microsoft.com/en-us/security/zero-trust/ten-laws-of-security
#infosec #blueteam
Added fresh threat hunting ideas to my github repo. Check it: https://github:.com/xFFninja/happy_threat_hunting
#threathunting #cloudsecurity #blueteam #infosec #KQL
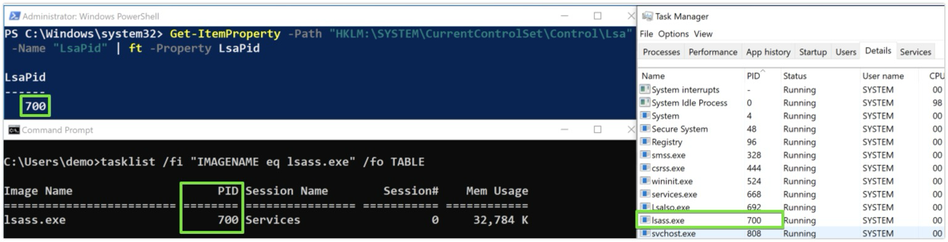
Get current PID of lsass.exe from registry
Get-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\Lsa” -Name “LsaPid” | ft -Property LsaPid
Can be handy for usage with different credential dumping tools wich can accept lsass.exe’s PID as an argument (e.g. PPLdump, comsvcs.dll, nanodump, etc.)
#redteam #infosec #blueteam #threathunting
Threat Hunting hint: On Windows boxes search for process creation events with System process names run outside (%SYSTEM%) folder (e.g. smss.exe, wininit.exe, winlogon.exe, etc)
#infosec #threathunting #blueteam #dfir #malware
Whitepaper on Linux Container Hardening:
https://research.nccgroup.com/wp-content/uploads/episerver-images/assets/ad04beb697a64e3ea20579e5bf604b4e/ad04beb697a64e3ea20579e5bf604b4e.pdf
#infosec #blueteam
List of file extentions which can be used by TAs as malicious:
https://www.file-extensions.org/filetype/extension/name/dangerous-malicious-files
#infosec #malware #blueteam #threathunting
Good starting point for email attachment blocklist
https://www.file-extensions.org/filetype/extension/name/email-attachment-blocked-files
#malware #phishing #infosec
https://start.me/p/wMrA5z/cyber-threat-intelligence
- awesome resource to track cyber threat reports in one place
#cybersecurity #infosec #blueteam
If you are familiar with #lolbins then this definitely will be interesting for you
#LOLDrivers is the list of Windows drivers used by adversaries to bypass security mechanisms. Great resource to develop new detections in your environment
https://www.loldrivers.io/
#infosec #dfir #threathunting #blueteam
Linux folders explained.
#linux
You can activate Windows 'Run' dialog (win+R) using the following command:
rundll32.exe shell32.dll,#61
#blueteam
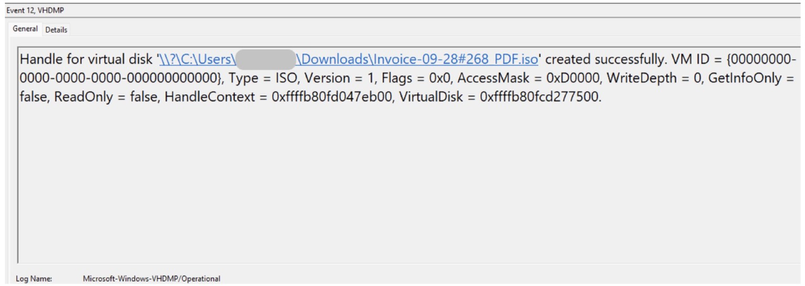
Hunt for malicious ISO files tip: Enable Microsoft-Windows-VHDMP/Operational logs and search for Event 12
#infosec #blueteam #threathunting #DFIR #malware
Tweets with limited visibility are visible:ablobcool: #infosec
How to launch cmd/PS from paint:
https://tzusec.com/how-to-launch-command-prompt-and-powershell-from-ms-paint/
#infosec #blueteam #redteam
A word on decomissioning old signatures.
Full report here: https://quadrantsec.com/resource/technical-analysis/black-basta-malware-overview
#infosec #malware #blueteam #threathunting