arXiV Of Our Own
RE, game modding, fighting games, programming languages, math, and everything in-between
A year ago, I saw someone open a book lamp in a bar. It was a pretty expensive product. Since I combine electronics and paper crafting, I had to DIY it and develop an easy-to-use circuit template and instructions for it. This educational project is perfect for libraries. Please #retoot :-)
Template and instructions are available on my website: https://www.voltpaperscissors.com/diybooklamp.
Feel free to ask any questions.
#papercircuit #papercraft #diy #MINT #STEM
Ola Bini's unjust and politically motivated prosecution must end. Ecuadorean judicial authorities should affirm his innocence and reject prosecutors' insinuation that using Tor is indication of suspicious criminal activity. https://www.eff.org/deeplinks/2025/04/six-years-dangerous-misconceptions-targeting-ola-bini-and-digital-rights-ecuador
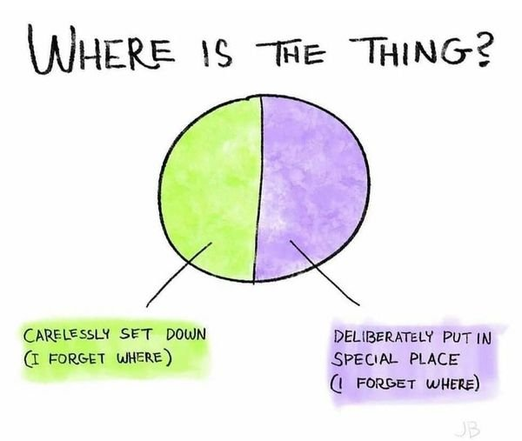
@thermia@sk.girlthi.ng I wasted a bunch of time on this and I don't know if it'll make sense to non-Americans (but it's really funny to me)
Wonderful news to share: @compiler_explorer has received a $10K grant from NVIDIA's FOSS Fund!
After years of collaboration with their engineers to support GPU compilation, this funding will help us maintain the AWS GPU instances that make CUDA experimentation accessible to all.
A huge thank you to NVIDIA for supporting open source tools that benefit the entire developer community! #NVIDIAGrant #OpenSource
@lesley if you mean self-hosting, I think a good place to get started is the r/selfhosted wiki (https://wiki.r-selfhosted.com/). If you have questions, I'd also be more than happy to help!
Hah! And add to the list of Things I've Learned, the JWST is running basically the same processor as the original Nintendo Wii, at 118MHz, with 44MB of RAM.
I'm not sure you could run a modern Logitek mouse driver with that little memory or on a processor running that slowly.
https://blog.infected.systems/posts/2025-04-21-this-blog-is-hosted-on-a-nintendo-wii/
Original source may be here, which I can't retoot from tech.lgbt https://yourwalls.today/notice/AtFsre8I8V2plS9rzE
linkspam!
Linking directly to text fragments in web pages.
https://alfy.blog/2024/10/19/linking-directly-to-web-page-content.html
saved 2024-10-24 https://dotat.at/:/LH27G.html
nix configs are like a home. you guys need to treat them better smh
top surgery (you can now see your processes running)
I boosted several posts about this already, but since people keep asking if I've seen it....
MITRE has announced that its funding for the Common Vulnerabilities and Exposures (CVE) program and related programs, including the Common Weakness Enumeration Program, will expire on April 16. The CVE database is critical for anyone doing vulnerability management or security research, and for a whole lot of other uses. There isn't really anyone else left who does this, and it's typically been work that is paid for and supported by the US government, which is a major consumer of this information, btw.
I reached out to MITRE, and they confirmed it is for real. Here is the contract, which is through the Department of Homeland Security, and has been renewed annually on the 16th or 17th of April.
https://www.usaspending.gov/award/CONT_AWD_70RCSJ23FR0000015_7001_70RSAT20D00000001_7001
MITRE's CVE database is likely going offline tomorrow. They have told me that for now, historical CVE records will be available at GitHub, https://github.com/CVEProject
Yosry Barsoum, vice president and director at MITRE's Center for Securing the Homeland, said:
“On Wednesday, April 16, 2025, funding for MITRE to develop, operate, and modernize the Common Vulnerabilities and Exposures (CVE®) Program and related programs, such as the Common Weakness Enumeration (CWE™) Program, will expire. The government continues to make considerable efforts to support MITRE’s role in the program and MITRE remains committed to CVE as a global resource.”
@Anthidote @oleksandr the other day i liked a picture somebody's boobs from the project account
This just showed up on Debian Security:
Package: atop
CVE ID: CVE-2025-31160
It was discovered that Atop, a monitor tool for system resources and process activity, always tried to connect to the port of atopgpud (an additional daemon gathering GPU statistics not shipped in Debian) while performing insufficient sanitising of the data read from this port.
With this update, additional validation is added and by default atop no ...
https://lists.debian.org/debian-security-announce/2025/msg00054.html