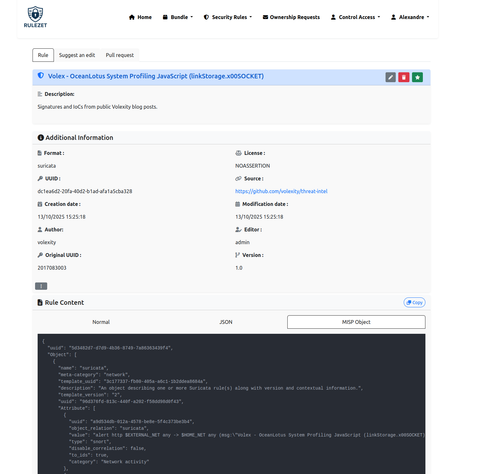
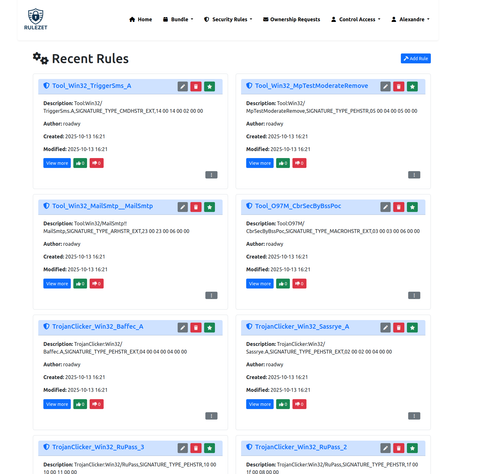
One year, I had a chat with the fine people @suricata during the @cert_eu conference, and they were wondering why we didn't create an open source website for all the different rules (YARA, Suricata, and many others) — a place to allow comments, reviews, bundling, and integration with @misp.
We’ve just released the first beta version of the rulezet.org service! 🎉
The platform is open and publicly available and the entire back-end is fully open source.
It’s still in beta, so feedback is very welcome!
#cti #yara #threatintelligence #osint #dfir #cybersecurity #suricata