🇬🇧✨ What if persistence didn’t need malware—or even a running process?
At #leHACK 2025, M101 explores unconventional backdoor techniques on Windows & Linux using only native OS features.
Forget payloads. Think logic, trust abuse, stealth primitives.
Based on red team ops & real-world research.
🗓️ 28 June
🕐 4:30pm
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Essential for red teamers and defenders alike.
#redteam #persistence #leHACK
🗓️ #leHACK 2025 // June 27-29, 2025
🎟️Tickets : https://www.billetweb.fr/lehack-2025-the-singularity
📍 https://www.cite-sciences.fr
🇫🇷✨ Et si la persistance n’avait besoin ni de malware, ni de shell, ni de process actif ?
Au #leHACK 2025, M101 présente des backdoors sur Windows & Linux qui s’appuient uniquement sur les fonctionnalités natives du système.
Pas de charge utile, juste de l’abus logique et furtif.
🗓️ 28 juin
🕐 16h30
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Dernières places : https://billetweb.fr/lehack-2025-the-singularity
Un talk à ne pas rater pour attaquants et défenseurs.
#redteam #persistence #leHACK
🇬🇧✨ Ever wondered what’s inside a €12 smartwatch?
At #leHACK 2025, Virtualabs & Xilokar break down the Homday Xpert to reveal firmware secrets, obscure SoCs, and a BLE vulnerability combo that no one saw coming.
From teardown to exploitation, this talk is a masterclass in cheap hardware hacking.
🗓️ 28 June
🕐 3:30pm
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Come for the wires, stay for the surprises.
#BLEhacking #reverseengineering #leHACK
🇫🇷✨ Que cache une montre connectée à 12 € ?
Au leHACK 2025, Virtualabs & Xilokar démontent la Homday Xpert pour en extraire le firmware, analyser ses composants JieLi et exploiter une faille BLE improbable mais réelle.
Du hardware hacking à petit prix, version expert.
🗓️ 28 juin
🕐 15h30
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Dernières places : https://billetweb.fr/lehack-2025-the-singularity
3 fils, une montre… et des surprises.
#BLEhacking #reverseengineering #leHACK
🇬🇧 ✨ Misconfigurations that make pentesters smile — and defenders cry.
At #leHACK 2025, Nicolas Aunay walks you through the worst AD security fails he’s seen: plaintext passwords, NTLM relays, rogue delegations, and more…
Bonus: real-world demo of a full Domain Admin takeover in minutes — and a 10-minute physical intrusion challenge 🧨
🗓️ 27 june
🕐 4:30pm
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Come laugh. And fix your AD.
#ActiveDirectory #redteam #leHACK
🇫🇷 ✨ Les pires fails d’Active Directory enfin compilés.
Nicolas Aunay vous présente son “Hall of Shame” des erreurs de config les plus catastrophiques : mots de passe en clair, NTLMv1, délégations absurdes, comptes à privilèges oubliés…
Démo à l’appui : une élévation en Domain Admin en quelques minutes et un challenge d’intrusion physique express 🧨
🗓️ 27 juin
🕐 16h30
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Dernières places : https://billetweb.fr/lehack-2025-the-singularity *
Venez rire… puis corriger vos GPOs.
#AD #leHACK
🇬🇧✨ Bug bounty on mobile: what really works?
At #leHACK 2025, Laszlo RADNAI shares lessons learned from years of hacking mobile apps & products through VRPs. Learn how to choose the right targets and avoid common pitfalls!
🗓️ 28 June
🕐 2:45pm
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Don’t miss it!
#bugbounty #mobilesecurity #leHACK
🇫🇷✨ Bug bounty mobile : comment maximiser ses résultats ?
Pendant #leHACK 2025, Laszlo RADNAI partage son retour d’expérience sur les VRP mobiles : choix des cibles, erreurs à éviter, exemples Android… Un talk incontournable !
🗓️ 28 juin
🕐 14h45
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Dernières places : https://billetweb.fr/lehack-2025-the-singularity
À ne pas manquer !
#bugbounty #sécuritémobile #leHACK
🇬🇧✨ Debugging embedded systems when all else fails?
Join Vincent LOPES at #leHACK 2025 for a masterclass in unconventional debugging: from exploiting locked ports to building custom debuggers inside firmware. Perfect for hardware hackers & reverse engineers!
🗓️ 27 June
🕐 3:45pm
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Don’t miss it!
#embedded #cybersecurity #leHACK
🇬🇧✨ Ever wanted to hack a game—or protect yours?
Join Lucas PARSY at #leHACK 2025 for a deep dive into video game hacking: memory editing, Cheat Engine, binary protection methods and their limits. Perfect for curious gamers & devs!
🗓️ 28 June
🕐 2:00pm
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Don’t miss it!
#gamehacking #cybersecurity #leHACK
🇬🇧✨ Ready to unlock quantum computing? Join Robin DESCHAMPS at #leHACK 2025 for a beginner-friendly guide to quantum principles, PQC, QKD, and their impact on cybersecurity. Learn how quantum will reshape security!
🗓️ 27 June
🕐 2:45pm
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Don’t miss it!
#quantum #cybersecurity #leHACK
🇬🇧✨ What if botnets weren’t just about compromised PCs?
At #leHACK 2025, 'Eunous' reveals how a homemade ESP32 botnet can exfiltrate data, perform surveillance, and even triangulate Bluetooth signals. Discover why you should never trust your microcontrollers!
🗓️ 28 June
🕐 11:45am
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Don’t miss it!
#IoTSecurity #cybersecurity #leHACK
------------
🇬🇧✨ Could your browser’s cache be used to smuggle malware?
Join Aurélien Chalot at hashtag#leHACK 2025 to uncover how cache smuggling bypasses traditional defenses for silent payload delivery and network recon. Learn how to protect your organization!
🗓️ 27 June
🕐 2:00pm
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Don’t miss it!
#redteam #cybersecurity #leHACK
------------
🇫🇷✨ Et si le cache de votre navigateur permettait de diffuser des malwares ?
Aurélien Chalot présente le cache smuggling lors du hashtag#leHACK 2025 : techniques d’attaque, reconnaissance furtive et conseils pour s’en prémunir !
🗓️ 27 Juin
🕐 14h00
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Dernières places : https://billetweb.fr/lehack-2025-the-singularity
À ne pas manquer !
#redteam #cybersécurité #leHACK
🇬🇧✨ Can RAG systems leak hidden data through prompt injection?
Join Pedro PANIAGO at #leHACK 2025 to discover the “Up and Down Technique” for exfiltrating sensitive info from RAG applications. Real-world examples and actionable mitigation strategies await!
🗓️ 27 June
🕐 11:15am
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Late bird : https://billetweb.fr/lehack-2025-the-singularity
Don’t miss it!
#AIsecurity #cybersecurity #leHACK
------------
🇫🇷✨ Les systèmes RAG peuvent-ils divulguer des données cachées via une injection de prompt ?
Assistez au talk de Pedro PANIAGO lors de #leHACK 2025 pour découvrir la “Up and Down Technique” et comprendre comment protéger vos applications IA contre l’exfiltration de données.
🗓️ 27 Juin
🕐 11h15
🔗 https://lehack.org/2025/tracks/conferences
🎟️ Dernières places : https://billetweb.fr/lehack-2025-the-singularity
À ne pas manquer !
#sécuritéIA #cybersécurité #leHACK
🇬🇧✨ What can hands-on recon reveal that scanners miss?
Join Gaëtan HERFRAY at #leHACK 2025 as he shares how a user-centric and manual approach led him to his first €1K bug—without automated tools! Get practical insights for all bug bounty hunters.
📅 28 June, 10:00am
🔗 More talks: https://lehack.org/2025/tracks/conferences/
🎟️ Late bird : https://www.billetweb.fr/lehack-2025-the-singularity
Don’t miss out!
#bugbounty #cybersecurity #leHACK
------------
🇫🇷✨ Que peut découvrir la reconnaissance manuelle que les scanners ignorent ?
Gaëtan HERFRAY partage pendant #leHACK 2025 comment son approche utilisateur et pratique lui a permis de décrocher son premier bug à 1 000 €—sans outils automatiques ! Un talk à ne pas manquer pour tous les chasseurs de bugs.
📅 28 juin, 10h00
🔗 Plus de talks : https://lehack.org/2025/tracks/conferences/
🎟️ Dernières places : https://www.billetweb.fr/lehack-2025-the-singularity
À ne pas manquer !
#bugbounty #cybersécurité #leHACK
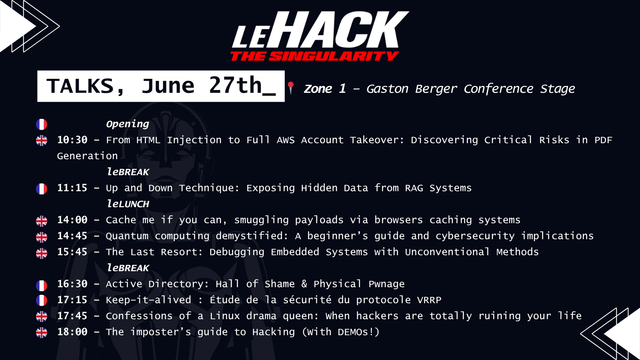
🇬🇧✨ What if a simple HTML injection could threaten your entire AWS account?
Join Raunak Parmar at #leHACK 2025 as he reveals how vulnerabilities in PDF generation can escalate to full account takeover. Gain practical strategies to secure your cloud assets!
📅 27 June, 10:30am
🔗 More talks: https://lnkd.in/eaTGkuiM
🎟️ Late bird : https://lnkd.in/e3xU3pXm
Don’t miss out!
#cybersecurity #cloudsecurity #leHACK
------------
🇫🇷✨ Et si une simple injection HTML mettait en péril tout votre compte AWS ?
Assistez à la session de Raunak Parmar à hashtag#leHACK 2025 et découvrez comment une faille dans la génération de PDF peut devenir critique. Repartez avec des solutions concrètes !
📅 27 juin, 10h30
🔗 Plus de talks : https://lnkd.in/eaTGkuiM
🎟️ Dernières places : https://lnkd.in/e3xU3pXm
À ne pas manquer !
#cybersécurité #cloud #leHACK
🇬🇧 💥 From payload smuggling to stealthy persistence...
This year, hashtag#leHACK 2025 talks are digging deep:
🕵️♂️ Cache me if you can – payloads via browser cache
🎭 The imposter’s guide to Hacking – with live demos
🎯 The Art of Staying In – unconventional backdoors on Windows & Linux
🚀 Explore the full lineup: https://lehack.org/2025/tracks/conferences/
🎟️ Don’t sleep on this : https://www.billetweb.fr/lehack-2025-the-singularity
------------
🇫🇷 💥 Du contournement au maintien d’accès furtif…
Cette année, les talks hashtag#leHACK2025 vont droit au système 😉 :
🕵️♂️ Cache me if you can – des payloads via le cache navigateur
🎭 The imposter’s guide to Hacking – avec démos en live
🎯 The Art of Staying In – backdoors atypiques sur Windows & Linux
🚀 Découvrez le programme complet : https://lehack.org/2025/tracks/conferences/
🎟️ N'oubliez pas vos places : https://www.billetweb.fr/lehack-2025-the-singularity
#Hacking #OffensiveSecurity #leHACK
[⏰ #REMINDER] [_WHO WANTS TO EARN BITCOINS?_] begins soon! Join virtualabs
for this new edition!
#leHACK wishes good luck to the teams involved 💪
₿ Rules & infos: https://buff.ly/3p44ZWb
[⏰ #REMINDER] Psst! Don't miss the OSINT CHALLENGE PRIZE CEREMONY which starts in 5 minutes 👀
📍 Zone 1 - Gaston Berger Conference Stage (https://buff.ly/3Lae5b4)
🎙️ Conferences lineup: https://buff.ly/3NSgeuq