Things I‘ll try to avoid for the rest of my life - #Watchguard. Unbelievable bad „customer“ experience, different statements from different supporters, solutions which don’t support standard development a customer environment can go through.
No Stars - No Recommendation.
~ Moved to @scs ~
Very strange behavior with #AzureAD, #MultifactorAuthentication and #ActiveDirectory #Migration. Maybe someone has an idea? Any help is much appreciated.
Situation: As usual we sync our #OnPrem ADs (at the moment five of them) with #AAD and use the mS-DS-ConsistencyGuid as the Source Anchor.
Last year we needed to "move" a user from one OnPrem (H) Domain to another (D). We created a new user in Domain H, removed the user in Domain D from the sync, copy/pasted his mS-DS-ConsistencyGuid from Domain D to Domain H and started the sync of the user in Domain H. So the user used the new credentials from Domain H but kept his 365 Data which he generated before with his account from Domain D.
A few weeks before we integrated #Multifactor #Authentication through #Watchguard #Authpoint MFA and activated it for the whole company and every user in every domain. Now as soon as the user changed his password for the first time since the MFA got in place, it was activated for him and the issues began.
Issue: When trying to logging into 365 with Authpoint MFA, the error message explains, that Azure awaits the the #immutableID based on the ObjectGUID of Domain H. But since we copy/pasted the mS-DS-ConsistencyGuid from the old Domain D, this is based on the ObjectGUID from the user of Domain D and so an authentication does not happen. If we change the immutableID to the awaited based on the ms-DS-ConsistencyGuid of Domain H, the user can log into Azure/365, but obviously the sync stops because ms-DS-Cons and immutableID dont match anymore.
So, for one person, that is maybe something you can do very dirty by editing the data in the metaverse, but unfortunately we are running soon a AD migration project where every user will be migrated to another single domain. So for me it seems like we are a few steps away from everything will explode?
Anybody has a hint/idea/solution/anything else? Every help and #boost is welcome and appreciated.
Very strange behavior with #AzureAD, #MultifactorAuthentication and #ActiveDirectory #Migration. Maybe someone has an idea? Any help is much appreciated.
Situation: As usual we sync our #OnPrem ADs (at the moment five of them) with #AAD and use the mS-DS-ConsistencyGuid as the Source Anchor.
Last year we needed to "move" a user from one OnPrem (H) Domain to another (D). We created a new user in Domain H, removed the user in Domain D from the sync, copy/pasted his mS-DS-ConsistencyGuid from Domain D to Domain H and started the sync of the user in Domain H. So the user used the new credentials from Domain H but kept his 365 Data which he generated before with his account from Domain D.
A few weeks before we integrated #Multifactor #Authentication through #Watchguard #Authpoint MFA and activated it for the whole company and every user in every domain. Now as soon as the user changed his password for the first time since the MFA got in place, it was activated for him and the issues began.
Issue: When trying to logging into 365 with Authpoint MFA, the error message explains, that Azure awaits the the #immutableID based on the ObjectGUID of Domain H. But since we copy/pasted the mS-DS-ConsistencyGuid from the old Domain D, this is based on the ObjectGUID from the user of Domain D and so an authentication does not happen. If we change the immutableID to the awaited based on the ms-DS-ConsistencyGuid of Domain H, the user can log into Azure/365, but obviously the sync stops because ms-DS-Cons and immutableID dont match anymore.
So, for one person, that is maybe something you can do very dirty by editing the data in the metaverse, but unfortunately we are running soon a AD migration project where every user will be migrated to another single domain. So for me it seems like we are a few steps away from everything will explode?
Anybody has a hint/idea/solution/anything else? Every help and #boost is welcome and appreciated.
My daughter's school took over my personal #Microsoft #Azure account https://www.jeffgeerling.com/blog/2023/my-daughters-school-took-over-my-personal-microsoft-account
Question: What's better than peanut butter and jelly for an Azure AD admin?
Answer: Our newly launched feature that adds conditional access policy support to Azure AD PIM.
Folks, this is a marriage made in heaven.
Read on for a quick walkthrough.
https://www.linkedin.com/pulse/you-know-whats-better-than-peanut-butter-jelly-azure-ad-fernando
Update on the #Exchange Server Antivirus Exclusions
Microsoft finally removed the recommendation to exclude PowerShell.exe and w3wp.exe and two others from the official documentation
Are you responsible for Azure AD in your org? We just published a new doc (aka.ms/entradeprecations) that lists all the upcoming changes in one place.
We plan on updating this quarterly, in line with our change announcements in Mar, Jun, Sep, and Dec.
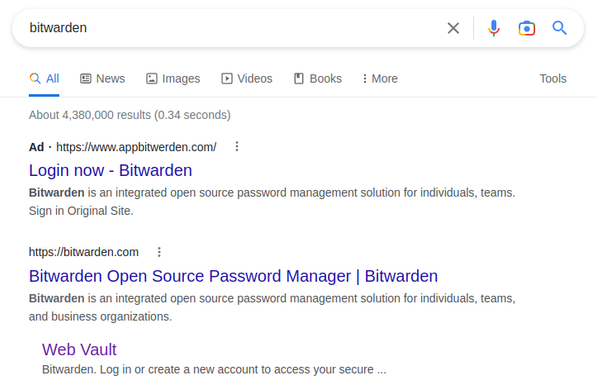
Ouch. Found a fake Bitwarden site.
loginbitwarden[.]com (Ad URL)
appbitwerden[.]com (Ad URL)
vaultbitwerdan[.]com
Saw two different google search ads for bitwarden yesterday, but didn't get them to redirect until today.
The URL is very close to the actual vault.bitwarden.com. It takes your username, regardless of it being a real account or not, then prompts for the master password. When you click to login, it claims there is an error. Naturally at this point it sent your username/password to the threat actor. It then does a redirect to the actual vault.bitwarden.com.
As a Bitwarden user this strikes too close to home! No me gusta.
Neues vom #ITGrundschutz: Das #ITGrundschutzKompendium wurde heute vom @bsi in der Edition 2023 veröffentlicht.
Das Kompendium ist als PDF und im XML-Format verfügbar. Die Bausteine als PDF und im Word-Format.
https://www.bsi.bund.de/DE/Themen/Unternehmen-und-Organisationen/Standards-und-Zertifizierung/IT-Grundschutz/IT-Grundschutz-Kompendium/it-grundschutz-kompendium_node.html
Don’t forget to increment the year in your password!
Compromised PyTorch-nightly dependency chain between December 25th and December 30th, 2022.
Steals all your SSH keys!
"If you installed PyTorch-nightly on Linux via pip between December 25, 2022 and December 30, 2022, please uninstall it and torchtriton immediately, and use the latest nightly binaries (newer than Dec 30th 2022)."
#infosec #machinelearning #deeplearning
@jgasmussen Very tough, yes, especially if it’s not only Hobby also the job. Then it’s so important to have regular “timeouts” to rest and avoid burn out. 😕
Happy new year.
@dazo In my case I‘m on an island, 200km away from home. I should take a deep breath and rest. Instead my thoughts come back every now and then to my next home projects. :-/ One the one hand, it’s some kind of fun for me, because I love what I do. On the others hand, I really need to take break. :-/
Does anyone know how to flash a broken iDRAC on a dell r620?
Boosts welcome
@nicoduck Da hab ich die Finger von gelassen. ^^ Hier bleibt es bei Planung und Vorbereitung (was sich so mit Phone und Tablet erledigen lässt).
Just wondering, is it just me and some kind of „addiction“ or is this „a thing“ being on vacation and thinking/planing about the rebuilding of the #HomeLab from scratch every now and then? 🤔
@alexbell 4 Yubikeys - one private, one business and one backup per key.
I published a new release of HardeningKitty 🚀😺
It is now official a PowerShell module, for all other changes see https://github.com/0x6d69636b/windows_hardening/releases/tag/v.0.9.0