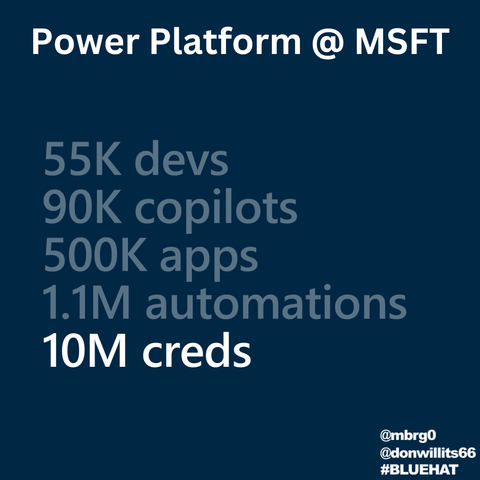
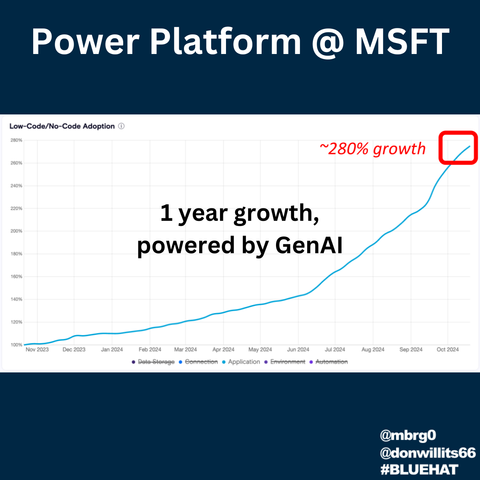
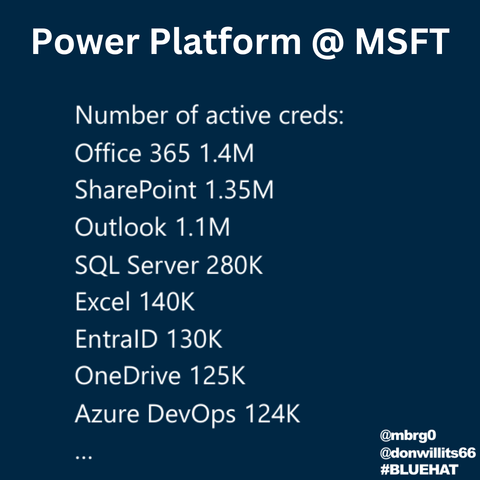
A couple of days ago, I unearthed my first #computer, an #MSX straight from the ‘80s. It was lost in some box in the basement for who knows how long. Just feeling its power switch gave me the goosebumps…
This discovery came after sharing my hacker’s origin story with Nic Fillingham and Wendy Zenone in a new episode of Microsoft’s #BlueHat #Podcast.
https://thecyberwire.com/podcasts/the-bluehat-podcast/52/notes
Join us while we chat about my first-ever #CVE, overlooked #vulnerabilities that continue to pose significant risks today, #ActiveDirectory and #password security, my unexpected journey into #bugbounty hunting and my involvement in the #ZeroDayQuest, how to learn new things, mentorship and positive leadership, and of course pineapple pizza 🍍🍕