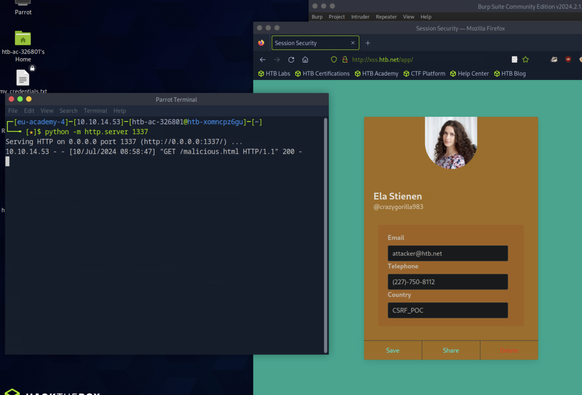
Lorenzo Gallegos presents 'How to Write Secure Code' July 25th at Nebraska.Code().
https://nebraskacode.amegala.com/
#securecode #OWASP #XSS #sqlinjection #crosssitescripting #lincoln #CrossSiteRequestForgery #serversiderequestforgery #Nebraska #PrivilegeEscalation #supplychain #webdevelopment #DeveloperConference #coding #TechSecurity #TechConference