El lado del mal - AI-Powered Adversaries: Atacantes armados con IA para hacer malware, vulnerar sistemas o cometer fraudes https://www.elladodelmal.com/2025/12/ai-powered-adversaries-atacantes.html #malware #Cibercrimen #Ciberespionaje #IA #AI #GenAI #Gemini #GTIG #InteligenciaArtificial
#GTIG
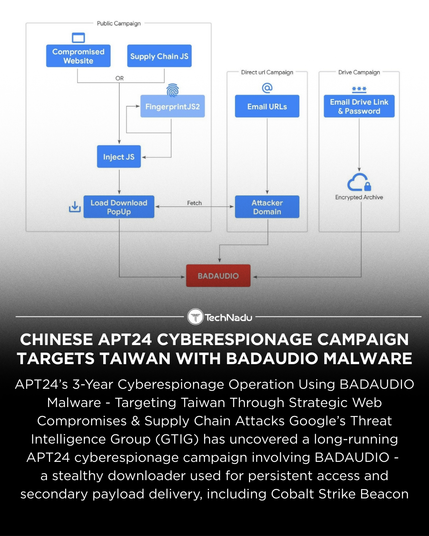
GTIG is tracking a multi-year APT24 cyberespionage campaign leveraging the BADAUDIO downloader.
Notable elements:
• Control-flow flattening + DLL Search Order Hijacking
• Targeted supply chain compromises impacting 1K+ domains
• Cobalt Strike Beacon (shared watermark w/ prior APT24 ops)
• Cloud-hosted phishing + JS injection on legitimate sites
• Strategic web compromise → selective payload delivery
Full report:
https://www.technadu.com/chinese-apt24-cyberespionage-campaign-targets-taiwan-with-badaudio-malware/614191/
Follow @technadu for daily threat intelligence.
#APT24 #BADAUDIO #CyberEspionage #ChinaCyber #GTIG #SupplyChainAttack #Taiwan #CobaltStrike #Malware #ThreatIntel
Die Cybercriminals so:
"Lass uns mal was mit AI machen!"
"Jo. Und dann fragt der Shit selbstständig bei der AI nach und besorgt sich aktuellen Code."
"Aber getarnt!"
Google’s Threat Intelligence Group (GTIG):
"Gegner nutzen künstliche Intelligenz, um neue Malware‑Familien zu verbreiten, die während der Ausführung große Sprachmodelle (LLMs) integrieren.
Dieser neue Ansatz ermöglicht ein dynamisches Ändern während der Ausführung und erreicht damit ein Maß an operativer Vielseitigkeit, das mit herkömmlicher Malware praktisch unmöglich zu erreichen ist.
Google bezeichnet die Technik als „Just‑in‑Time“‑Selbstmodifikation und hebt den experimentellen PromptFlux‑Malware‑Dropper sowie den PromptSteal‑(auch bekannt als LameHug‑)Datensammler, der in der Ukraine eingesetzt wurde, als Beispiele für dynamische Skriptgenerierung, Code‑Obfuskation und die Erstellung von On‑Demand‑Funktionen hervor."
https://cloud.google.com/blog/topics/threat-intelligence/threat-actor-usage-of-ai-tools/?hl=en
#infosec #infosecnews #google #gtig #Malware #PromptFlux #PromptSteal
More than 14,000 WordPress sites hacked, used to spread malware
a new threat actor codenamed UNC5142 has been successfully hacking into WordPress sites often using flawed WordPress themes, plugins, or databases.
#WordPress #malware #GTIG #security #cybersecurity #hackers #hacking #hacked
https://mashable.com/article/wordpress-hacked-unc5142-etherhiding-blockchain-malware-spreading
Advanced threat actor UNC6148 is actively targeting SonicWall SMA 100 series appliances with sophisticated OVERSTEP backdoor malware, bypassing patches through stolen credentials.
#SecurityLand #BreachBreakdown #UNC6148 #Mandiant #GTIG #SonicWall #OVERSTEP
Read More: https://www.security.land/sonicwall-sma-100-series-targeted-by-advanced-backdoor-campaign/
#DPRK escalated #cyberthreat from #NorthKorea who are increasingly targeting #Europe in addition to the #UnitedStates, as identified by the #Google Threat #Intelligence Group (#GTIG).
#DPRK #IT workers employ sophisticated tactics such as posing as legitimate remote workers, using fabricated identities, and engaging in extortion by threatening leak sensitive company information, including proprietary #data and #sourcecode like #defense and government in #EU
Google Threat Intelligence Group (#GTIG) tracked 75 actively exploited zero-day flaws in 2024
https://securityaffairs.com/177180/hacking/google-threat-intelligence-group-gtig-tracked-75-actively-exploited-zero-day-flaws-in-2024.html
#securityaffairs #hacking #zeroday
Google Threat Intelligence Group (GTIG) report: “Adversarial Misuse of Generative AI” details how threat actors (ATP and IO actors) are attempting to misuse Google’s Gemini web application and if these efforts have created any novel or unique AI-enabled attack techniques.
High level results: At this time, AI can be useful to threat actors for performing common tasks like troubleshooting, research, learning/training, and content generation. GTIG is indicating they are NOT seeing new or novel capabilities being created by threat actor activities with AI.
“Rather than enabling disruptive change, generative AI allows threat actors to move faster and at higher volume. For skilled actors, generative AI tools provide a helpful framework” … “For less skilled actors, they also provide a learning and productivity tool, enabling them to more quickly develop tools and incorporate existing techniques.”
DL report (PDF) here: https://services.google.com/fh/files/misc/adversarial-misuse-generative-ai.pdf
#AI #cybersecurity #Google #GTIG #LLMs #hackers #GenAI #Gemini