New #FileFix attack runs #JScript while bypassing #Windows #MoTW alerts
#JScript
🎯 #Microsoft’s Azure Blob Storage Abused in Phishing Campaigns
⚠️ #Cybercriminals are abusing the trust in Microsoft's сloud-based file storage solution by hosting #phishing pages on the service, employing techniques like HTML smuggling
Threat actors leverage the *.blob.core.windows[.]net subdomain to store documents
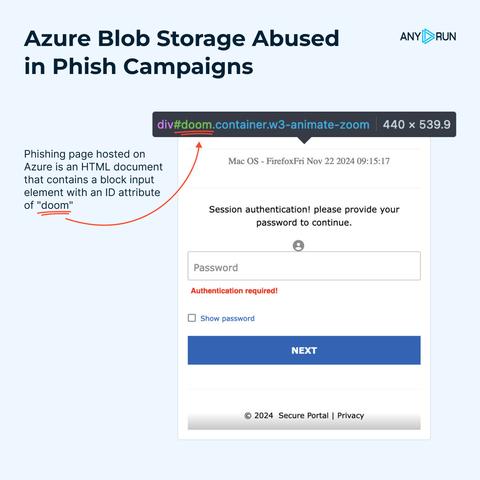
🔎 The original phishing page hosted on #Azure Storage is a well-known HTML document that contains a block input element with the ID attribute "doom"
🕵 To make the phishing page more convincing, it includes information about the user's software obtained via #JScript:
window.navigator.platform - identifies the operating system
window.navigator.userAgent - detects the browser being used
Company logos, extracted using email address parsing, are loaded from the logo[.]clearbit[.]com service
To collect and store stolen data, an HTTP POST request is sent to nocodeform[.]io for collecting form submissions
📌 Phishing pages on Azure Blob Storage typically have a short lifespan. To remain active longer, attackers may host pages with redirects to #phish sites. With minimal suspicious content, these pages can evade detection slightly longer
Take a look at the sandbox session:
https://app.any.run/tasks/60157f76-92ec-463e-a1d0-c17930af3da6/?utm_source=mastodon&utm_medium=post&utm_campaign=azure_phishing&utm_content=linktoservice&utm_term=021224
🔍 Use this #TI Lookup query to find threats targeting the set of requested domains:
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=azure_phishing&utm_content=linktoti&utm_term=021224#%7B%2522query%2522:%2522domainName:%255C%2522.blob.core.windows.net%255C%2522%25C2%25A0and%25C2%25A0%25C2%25A0domainName:%255C%2522aadcdn.msauth.net%255C%2522%2520and%2520domainName:%255C%2522cdnjs.cloudflare.com%255C%2522%2520and%2520domainName:%255C%2522www.w3schools.com%255C%2522%2522,%2522dateRange%2522:180%7D%20
👨💻 Find links to HTML pages hosted on Azure Blob Storage using this search request:
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=azure_phishing&utm_content=linktoti&utm_term=021224#%7B%2522query%2522:%2522commandLine:%255C%2522https:/*.blob.core.windows.net/*.html%255C%2522%2520%2522,%2522dateRange%2522:180%7D%20
Analyze and investigate the latest #malware and phishing threats with ANYRUN 🛡️
Реализация событий через HTTP
Для некоторых задач, связанных с обновлением данных в реальном времени — например, новостные ленты, уведомления или поток чата, можно обойтись без сложных двусторонних протоколов, как WebSocket. Мы можем использовать простой механизм передачи данных от сервера к клиенту через HTTP, который часто оказывается удобнее и эффективнее в настройке для однонаправленного обмена данными.
Con #JScript no pudieron, pero con #TypeScript nos la han metido bien doblada estos de #Microsoft. Parece pensado para 1) desarrollar en #JavaScript por gente que le jode cómo funciona JavaScript; 2) privatizar un estándar haciéndose el guay … #DeveloperThinks
Часть 1. TMA на KMP. Пишем кликер на Kotlin/JS
В этой статье рассмотрим старт проекта как обычное веб-приложение с минимальным функционалом. Остальные функции будут завязаны на Telegram API и веб-приложение сможет запускаться из Telegram.
Researchers have uncovered a multi-stage attack involving infected sites, #fake Chrome updates, and a #JScript downloader to deploy the BadSpace #malware.
https://thehackernews.com/2024/06/hackers-exploit-legitimate-websites-to.html
想不到去年寫的勉強堪用的 #jscript 模組功能還有真的翻出來用的一天。
那時想做一個像 python 的 import 可以直接匯入 top level 變數的模組系統,而不是 require.js 那種需要顯式匯出的。
本來想做 amd.js 但寫到一半發現太麻煩就逃了。
Given the popularity, power and success of this modern approach to building web applications, why on earth would you consider an older, clunkier and less popular approach like hypermedia?
JavaScript Fatigue
We are glad you asked!
#webdev #html #json #api #jscript
Hypermedia: A Reintroduction https://hypermedia.systems/hypermedia-reintroduction/
@pbeens If my tone wasn't obvious: never.
That's a fool's errand. A windmill to tilt at. (Insert other literary references for futility here.)
See also: #ActionScript—also #ECMAScript-based, as part of #Flash—or #JScript, because Microsoft do as Microsoft do.
這幾天玩 windows #jscript 的腳本,用了 #excel object model 來讀寫 excel 表格、ActiveX 的 #ajax 、FileSystemObject 來存檔 http response 作快取 (不過最後沒用到) 。
把變數名稱、url、資料碼掉後分享出來,至少我覺得 jscript 在讀寫 excel 自動化這點還蠻方便的,windows 內建不用裝其它有的沒的,也不用特別調什麼設定,雖然比起 #VBA 明顯少掉 msgbox 這類對話框功能,但對不想學 basic 的人還是可以一用。
#js
https://gist.github.com/GHolk/119afb3d5c34b0c528e212c2dc6a23a4
Microsoft Zero-Day Actively Exploited, Patch Forthcoming - CVE-2020-0674 is a critical flaw for most Internet Explorer versions, allowing remote code executi... more: https://threatpost.com/microsoft-zero-day-actively-exploited-patch/152018/ #securityvulnerability #remotecodeexecution #internetexplorer #vulnerabilities #cve-2020-0674 #websecurity #jscript.dll #aptattacks #workaround #darkhotel #microsoft #windows7 #zeroday #patch #bug