#ESETresearch has uncovered the #MirrorFace Operation AkaiRyū, which extends the group’s usual focus beyond Japan into Europe. The initial lure centered around Expo 2025 in Japan, compromising a Central European diplomatic institute.
https://www.welivesecurity.com/en/eset-research/operation-akairyu-mirrorface-invites-europe-expo-2025-revives-anel-backdoor/
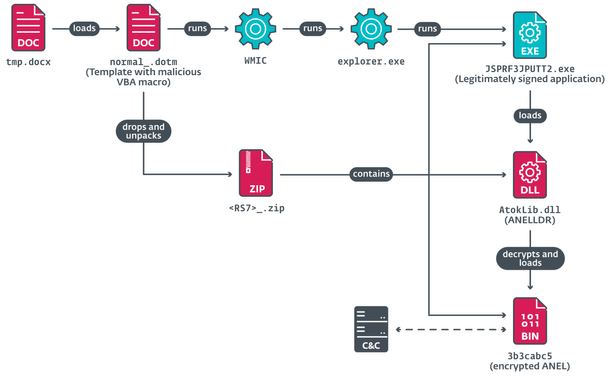
Surprisingly, #MirrorFace used #ANEL – a backdoor historically linked only to #APT10 – highlighting a shift in the group’s tactics and reinforcing suspicions that MirrorFace could be part of the APT10 umbrella.
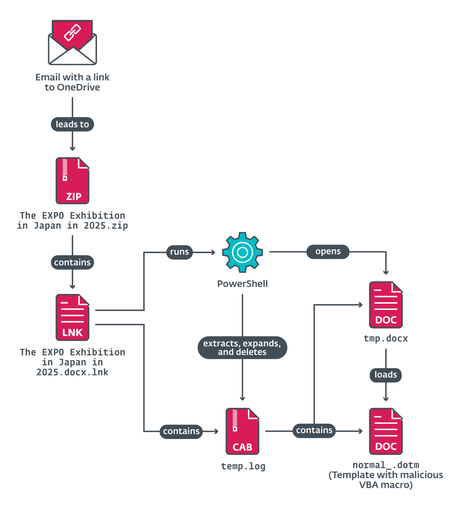
Operation AkaiRyū began with targeted spearphishing emails referencing the victim’s past correspondence and Expo 2025 , persuading recipients to download malicious attachments.
Once the files were opened, a layered compromise chain ensued . Collaborating with the victim allowed us to perform in-depth analysis, shedding light on MirrorFace’s post-compromise behavior – from credential harvesting to dropping additional tools for lateral movement.
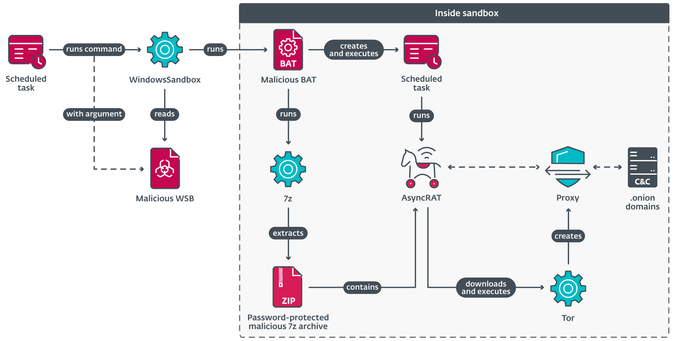
#MirrorFace used an intricate execution chain to stealthily run a highly tweaked #AsyncRAT within #WindowsSandbox, hampering detection efforts. This is the first time we’ve seen MirrorFace employ AsyncRAT.
In another twist, #MirrorFace utilized #VSCode remote tunnels, a tactic enabling covert access and command execution on compromised machines. This approach has also been seen with other China-aligned cyberespionage groups.
The group primarily leveraged #ANEL as a first-stage backdoor, #HiddenFace – MirrorFace’s flagship backdoor – was dropped later in the attack to bolster persistence . Notably absent this time was #LODEINFO, which #MirrorFace typically employs.
We presented our findings about Operation AkaiRyū conducted by #MirrorFace at @jpcert_ac on January 22, 2025: https://jsac.jpcert.or.jp.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/mirrorface