Also, all this ninja work to go through #WindowsSandbox to escape detection to finally raise a huge red flag by communicating over #Tor. It probably made sense for this target but still, what a let down...
#WindowsSandbox
#ESETresearch has uncovered the #MirrorFace Operation AkaiRyū, which extends the group’s usual focus beyond Japan into Europe. The initial lure centered around Expo 2025 in Japan, compromising a Central European diplomatic institute.
https://www.welivesecurity.com/en/eset-research/operation-akairyu-mirrorface-invites-europe-expo-2025-revives-anel-backdoor/
Surprisingly, #MirrorFace used #ANEL – a backdoor historically linked only to #APT10 – highlighting a shift in the group’s tactics and reinforcing suspicions that MirrorFace could be part of the APT10 umbrella.
Operation AkaiRyū began with targeted spearphishing emails referencing the victim’s past correspondence and Expo 2025 , persuading recipients to download malicious attachments.
Once the files were opened, a layered compromise chain ensued . Collaborating with the victim allowed us to perform in-depth analysis, shedding light on MirrorFace’s post-compromise behavior – from credential harvesting to dropping additional tools for lateral movement.
#MirrorFace used an intricate execution chain to stealthily run a highly tweaked #AsyncRAT within #WindowsSandbox, hampering detection efforts. This is the first time we’ve seen MirrorFace employ AsyncRAT.
In another twist, #MirrorFace utilized #VSCode remote tunnels, a tactic enabling covert access and command execution on compromised machines. This approach has also been seen with other China-aligned cyberespionage groups.
The group primarily leveraged #ANEL as a first-stage backdoor, #HiddenFace – MirrorFace’s flagship backdoor – was dropped later in the attack to bolster persistence . Notably absent this time was #LODEINFO, which #MirrorFace typically employs.
We presented our findings about Operation AkaiRyū conducted by #MirrorFace at @jpcert_ac on January 22, 2025: https://jsac.jpcert.or.jp.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/mirrorface
📰 «El espacio aislado de Windows está ahí para usarlo»
🔗 https://proxy.jesusysustics.com/2025/03/10532/
El espacio aislado de Windows (Windows Sandbox) nos permite virtualizar una versión por defecto del Sistema de usar y tirar. Tan pronto lo cierras, se olvida todos los cambios que has hecho, así que es ideal para jugar con fuego de forma controlada.
Hace cinco años que hablé sobre esta fantástica herramienta y viene bien recordarla al ser tan útil y socorrida, pero no viene instalada por defecto. Aquí se explican los pocos pasos que hay que seguir para activarlo y unos pequeños «trucos» al usarlo.
#️⃣ #máquinaVirtual #Microsoft #SistemaOperativo #virtualización #Windows #WindowsSandbox
Testing AI voice with my first tutorial video on YouTube about Windows Sandbox https://www.youtube.com/watch?v=0o60vJ8O_ok
#windows #windowssandbox #tutorial #tutorials #techtutorial #microsoft #sandbox #freelearning #learning #microsoftlearn
Exploring Windows Sandbox: Application Install and PowerShell Script Testing
#windows #Windows11Pro #microsoft #windowstips #windows11 #windowssandbox #dev #sandbox #dev #apps
#Microsoft bringt #FAT32-Format zurück und aktualisiert #WindowsSandboxClient | heise online https://www.heise.de/news/Microsoft-bringt-FAT32-Format-zurueck-und-aktualisiert-Windows-Sandbox-Client-9837202.html #Windows :windows: #WindowsSandbox
How to Enable or Disable Share Host Folders with #WindowsSandbox in #Windows11
https://www.elevenforum.com/t/enable-or-disable-share-host-folders-with-windows-sandbox-in-windows-11.27674/
How to Share Host Folder(s) with #WindowsSandbox in #Windows11
https://www.elevenforum.com/t/share-host-folder-with-windows-sandbox-in-windows-11.27671/
So, Godot 4.3 released.
https://godotengine.org/releases/4.3/
Good news for security-concerned gamers: since now there's a DirectX 12 renderer, Godot projects moving forward should hopefully work on Windows Sandbox (on Windows 10) without issue! Previously I found it simply impossible to get a Godot game working on Windows Sandbox due to requiring Vulkan or OpenGL, but this should slowly stop being an issue with newer Godot games.
…conversely, now GDScript has a basic form of source-code minification, which while it can help game developers protect their IP, it may also make games somewhat harder to reverse-engineer, particularly to figure out if the game contains malicious behavior.
Still arguably an overall security win, though.
#godot #cybersecurity #gamedev #windows #windowssandbox #reverseengineering
look-of-disapproval.png.webm.gif
https://developercommunity.visualstudio.com/t/exe-built-in-a-Windows-Sandbox-shared-pa/10340169
Run untrusted content safely with #WindowsSandbox
#Windows11 #Windows10 #sandbox
https://www.elevenforum.com/t/run-untrusted-content-safely-with-windows-sandbox.25167/
I shouldn't have to throw your #OpenSource software into #WindowsSandbox and disable networking to get it to behave.
Ever used Windows Sandbox? In my latest #blog post I talk about what it is, how I use it, and provide some example configuration files.
#Windows #Sandbox #WindowsSandbox
https://blog.jonsdocs.org.uk/2023/05/28/using-windows-sandbox/
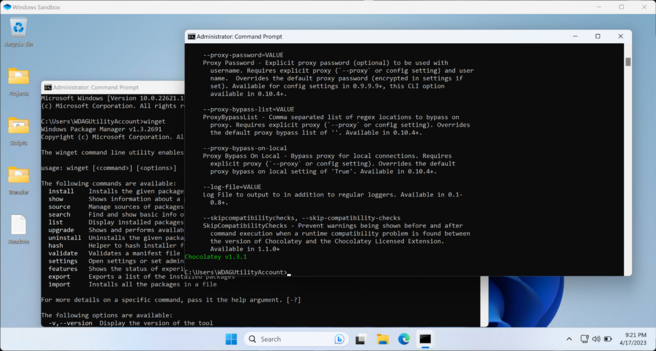
I was experimenting with Windows Sandbox over the weekend, and as a result I now have a sandbox config which launches it with drives mapped and both Winget and Chocolatey installed. 😁
The only hiccup I've run into is that Winget is being stubborn (there are some dependency issues) on Windows 10. 🤔
On Windows 11 however it's absolutely fine. 👍😎👍
#Windows #Windows11 #WindowsSandbox #VirtualMachine #VM #Tech #Software #Scripting
Windows 10 und 11 bringen eine Sandbox mit, um darin nicht vertrauenswürdige Software ausführen zu können. Wir zeigen was geht anhand unseres Notfall-Windows.
Notfall-Windows aus der Sandbox einsatzfähig machen und nutzen
#WindowsSandbox : quand une activation de l' #HyperV permettait une élévation de privilège sous #Windows10 !
เจอของเล่นใหม่ #WindowsSandbox
So, basically #bhyve for #Windows?
___________
#Microsoft unveils #WindowsSandbox: Run any app in a disposable virtual machine
First leaked a few months ago, the new feature should be coming to insiders imminently.