#ESETresearch noticed two #MirrorFace Excel documents, known as #ROAMINGMOUSE, were uploaded to VirusTotal from #Taiwan in March 2025. The documents contain a malicious VBA macro that deploys #ANEL backdoor on the compromised machine. @dbreitenbacher
The contents of the documents are written in traditional Chinese and the date used follows the Republic of China calendar. Based on this data and other information available to ESET, we assess with medium confidence that the target was a Taiwanese research institute.
Even though MirrorFace has been previously reported on targeting a Taiwanese entity, this is for the first time we don’t see any relation to Japan.
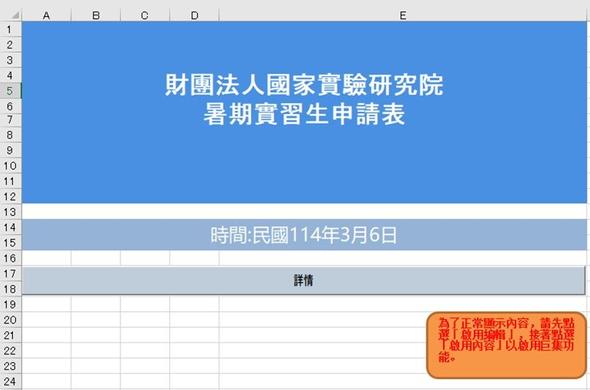
Our investigation indicates that both documents were used to target the same institute. MirrorFace employed a call-to-action textbox, asking targets to press “Enable editing” and then “Enable content” buttons to show the data in the worksheet.
Using multiple different malicious documents to compromise the same entity is an approach that was also observed in 2024 in “Case 1: Japanese research institute” described in our blogpost https://www.welivesecurity.com/en/eset-research/operation-akairyu-mirrorface-invites-europe-expo-2025-revives-anel-backdoor/.
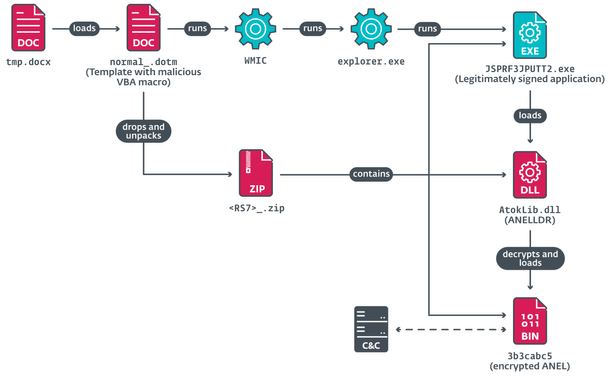
The overall compromise chain, leading to the execution of #ANEL to establish the initial foothold, remained the same as some observed in 2024. In particular, the approach was described as “Case 1” in Trend Micro’s report https://www.trendmicro.com/en_us/research/24/k/return-of-anel-in-the-recent-earth-kasha-spearphishing-campaign.html.
The overall compromise chain, leading to the execution of #ANEL to establish the initial foothold, remained the same as some observed in 2024. In particular, the approach was described as “Case 1” in Trend Micro’s report https://www.trendmicro.com/en_us/research/24/k/return-of-anel-in-the-recent-earth-kasha-spearphishing-campaign.html.
Besides the documents, a sample of #ANELLDR loader and a sample of #FaceXInjector were uploaded to VirusTotal from Taiwan around the same time as well.
IoCs
1BAC9E61C0D433964972BC91A5F38F31B85558C1 (ROAMINGMOUSE)
634D52E10E168A61C8201130F44925CC497C1251 (ROAMINGMOUSE)
E5F20192DB09EA033FEDD9CCEB782321EBB9C66E (FaceXInjector)
948CA0DAC99470775523809C1E7E60740B70C0FD (ANELLDR)
C&Cs:
64.176.34[.]120 (ANEL)
192.46.215[.]56 (ANEL)