The FBI's IC3 released 42,000+ domains tied to LabHost, a major phishing platform dismantled in April 2024.
#LabHost
#FBI shared a list of phishing domains associated with the #LabHost PhaaS Platform
https://securityaffairs.com/177293/cyber-crime/fbi-shared-a-list-of-phishing-domains-associated-with-the-labhost-phaas-platform.html
#securityaffairs #hacking #phishing
Phishing Domains Associated with LabHost PhaaS
#LabHost
https://www.ic3.gov/CSA/2025/250429.pdf
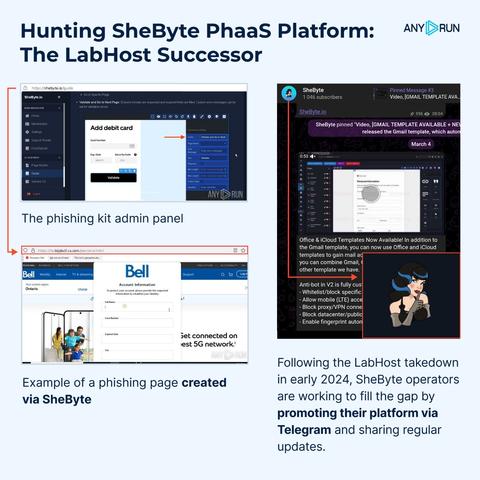
🚨 Hunting #SheByte PhaaS Platform: The LabHost Successor
🎯 This #PhaaS targets major banks in Canada and USA, including Interac, delivery services, telecom, toll roads. It also extends to Coinbase, popular email providers like Yahoo, Gmail, and Outlook, and impersonates brands such as Bell, Apple, and Amazon.
Following the #LabHost takedown in early 2024, SheByte operators are working to fill the gap by promoting their platform via Telegram and releasing major updates:
🔹 Geofiltering: prevents access to the phishing page from outside the targeted regions.
🔹 Connection Type Filtering: restricts VPN, hosting, mobile.
🔹 Fingerprint Detection: detects bots and sandboxes.
🔹 Enhanced Control of Page Flow: enables real-time control over the victim’s interaction flow.
🔹 V2 Page Builder: phishing page builder that mimics legitimate sites, adds custom data-stealing forms, and requires no coding skills.
🔗 Execution chain:
Phishing link ➡️ Fake bank login page ➡️ Credential harvesting ➡️ OTP interception ➡️ Security question capture ➡️ Redirect to legitimate bank site
👨💻 With #ANYRUN Sandbox, analysts can explore the phishing kit functionality available through the phishkit's admin panel: https://app.any.run/tasks/56ddc9be-3d32-405e-a53b-33b90640602e/?utm_source=mastodon&utm_medium=post&utm_campaign=shebyte&utm_content=linktoservice&utm_term=300425
Explore captured and detonated phishing site samples, most likely created using the SheByte phishing builder:
https://app.any.run/tasks/2b23cac6-fe32-4ac8-8f60-1a4758eaf711/?utm_source=mastodon&utm_medium=post&utm_campaign=shebyte&utm_content=linktoservice&utm_term=300425
https://app.any.run/tasks/6aacde46-d7e8-47a1-b2bf-606137c46bd8/?utm_source=mastodon&utm_medium=post&utm_campaign=shebyte&utm_content=linktoservice&utm_term=300425
https://app.any.run/tasks/d39f8b11-b228-4a52-9c4e-3a07fb745f26/?utm_source=mastodon&utm_medium=post&utm_campaign=shebyte&utm_content=linktoservice&utm_term=300425
🔍 These #phishkits often include data collection forms. Victims are tricked into entering sensitive information, which is sent directly to the attacker. This behavior can be used as a hunting pivot:
🔹 /file/db_connect<digits?>.php + request body parameters: name=
🔹 /t3chboiguru<digits?>.php + request body parameters: usr= psd=
📌 Indicators and patterns for hunting SheByte-related infrastructure:
CSS file hashes:
🔹 SHA256: 58d0a27afc6ed22f356c907579f15f41f120c913c118837dba9c1b8da13a5a4f
🔹SHA256: bc054fd38e88a7c9c1db08bd40dfe7ad366fa23efdce184e372d2adb431c91d2
Reverse DNS reused across multiple phishing-related domains:
🔹 my1[.]bode-panda[.]shop
Favicon of FIRST Bank loaded from a non-legitimate domain:
🔹 SHA256: 6e18a721d5559f569e5a6585bb6430c1965788e4607ea6704601872de8168811
🔹 Legitimate domain: bankatfirst[.]com
A URL request chain with a low number of HTTP requests in the session:
🔹 /personal.html
🔹 /otp.html
🔹 /c.html
#IOCs:
172[.]93[.]121[.]9
162.241[.]71.139
172.93[.]120.134
santosjjax[.]com
ghreo[.]net
cractil[.]net
sitygma[.]net
👨💻 SheByte Admin Dashboards:
www[.]lillliiilllliiiiilliilllllllliiii[.]site
jonathanserhan[.]shebyte[.]io
Analyze and investigate the latest #malware and phishing threats with #ANYRUN 🚀
Projet Nova : l’empire pirate LabHost s’effondre au Québec
https://www.zataz.com/projet-nova-lempire-pirate-labhost-seffondre-au-quebec/
#Infosec #Security #Cybersecurity #CeptBiro #ProjetNova #LabHost #Quebec #Zataz
Excellent investigation by Zataz into Project Nova. The operation is a success. This operation, led by 19 countries, aims to undermine LabHost (shut down in 2024). A 38-year-old British man was arrested and convicted.
Current operations (April 2025) are attempting to target and track the platform's users.
#Zataz #LabHost #Hacking #Spam #Infosec #Cyber #Cybersecurity #Quebec
https://www.zataz.com/projet-nova-lempire-pirate-labhost-seffondre-au-quebec/
Police take down $249-a-month global phishing service used by 2,000 hackers
Law enforcement officials in 19 countries have shut down an online platform that earned at least $1 million by selling phishing kits to cybercriminals, helping them launch attacks on tens of thousands of people worldwide.
#LabHost #Met #police #Europol #phishing #cybercrime #security #cybersecurity #infosec #hackers #Hacking
https://www.cnn.com/2024/04/18/tech/labhost-cybercrime-phishing-arrests/index.html
Global law enforcement cracked down on #LabHost phishing service!
"Operation Nebulae" arrested 32 individuals, including UK masterminds. LabHost ran 40,000 domains, victimizing over 94,000 in Australia.
https://thehackernews.com/2024/04/global-police-operation-disrupts.html
Phishing-as-a-service platform LabHost shut down in global operation
https://therecord.media/phishing-platform-labhost-shutdown-europol #cybercrime #phishing #LabHost #seized #GlobalOperation
#Europol nimmt #Phishing-Dienste-Plattform #Labhost hops | Security https://www.heise.de/news/Europol-nimmt-Phishing-Dienste-Plattform-Labhost-hops-9689381.html #CyberCrime
Phishing-as-a-Service (PhaaS) provider LabHost was taken down in an international law enforcement operation on 18 April 2024. Chainalysis maps out LabHost's on-chain activity and use of cryptocurrency. This includes the likely payment of monthly fees by cybercriminals (for LabHost's phishing tools) to identified LabHost cryptocurrency wallets. "LabHost then sent most of those funds to a few mainstream exchanges, presumably to be cashed out, as well as to a popular mixer, likely to launder the funds and obfuscate their origins." LabHost also sent funds to a payment processor (merchant services provider) and an Infrastructure-as-a-Service provider (while not identified, Chainalysis alludes to other criminal organizations using these services for web hosting, email tools, proxy services, etc.). There are links to iSpoof, another illicit provider of tools used for fraud that was shut down by the Metropolitan Police and other law enforcement agencies in 2022. 🔗 https://www.chainalysis.com/blog/labhost-disruption-phishing-as-a-service/
#LabHost #PhaaS #iSpoof #blockchain #cybercrime #moneylaundering
#DickeyBetts is now trending across Mastodon
#LabHost is now trending across Mastodon
#infosec #cybersecurity #labhost
LabHost shut down - local view from #Ireland.
Two arrested by gardaí as part of global operation that shut down phishing platform
https://www.thejournal.ie/two-arrested-gardai-global-operation-labhost-phishing-6357692-Apr2024/
Police smash LabHost international fraud network, 37 arrested https://www.tripwire.com/state-of-security/37-arrested-police-smash-labhost-international-fraud-network #Guestblog #Law&order #Phishing #phishing #LabHost
Group-IB also participated in the global takdown operation of LabHost Phishing-as-a-Service provider, a sophisticated criminal network offering stolen credit card data for sale. They dive into the operations of LabHost and its subsidiary, LabCVV. LabHost stands out due to its unique business model, which includes not only phishing services but also avenues for monetizing stolen credit cards and banking credentials through services like LabRefund. Grou-IB performs a source code analysis of the phishing template, analysis of cybercrime communications on Telegram and the dark web, of LabSend spam management service, and of LabCVV Card Shop. IOC provided 🔗 https://www.group-ib.com/blog/labhost-operation/
Police smash LabHost international fraud network, 37 arrested - Police have successfully infiltrated and disrupted the fraud platform "LabHost", used by ... https://www.tripwire.com/state-of-security/37-arrested-police-smash-labhost-international-fraud-network #guestblog #lawℴ #phishing #labhost
Law enforcement operation dismantled #phishing-as-a-service platform #LabHost
https://securityaffairs.com/162001/hacking/labhost-phaas-dismantled.html
#securityaffairs #hacking #malware
📬 LabHost-Phishing-Dienst zerschlagen: Über 30 Festnahmen weltweit
#ITSicherheit #europol #Internetkriminalität #LabHost #OperationNebulae #PhishingasaService #PhishingKit #PhishingSeiten https://sc.tarnkappe.info/d0b959
The Fall of LabHost: Law Enforcement Shuts Down Phishing Service Provider
#LabHost
https://www.trendmicro.com/en_us/research/24/d/labhost-takedown.html