#NetworkScanning
GitHub Continuous Integration checks went OK. It's up to someone else with commit access to merge it.
(Thankfully, someone else already updated zenmap to 7.97; but why zenmap was broken out into its own port instead of maintained as a subport is beyond me. It's also beyond me why someone would go through the trouble to update zenmap without also updating nmap; but given that my zenmap 7.96 update was apparently not making another MacPorts maintainer happy, maybe it's all for the best?)
#nmap #MacPorts #NetworkScanning #infosec #security
https://github.com/macports/macports-ports/pull/28422
GitHub Actions Continuous Integration checks are running (2 of 3 completed successfully so far).
Hopefully those will go OK?
It will be up to someone else with write access to merge it if so.
#ZMap #MacPorts #NetworkScanning #OpenSource
https://github.com/macports/macports-ports/pull/27538
2/3 of GitHub's Continuous Integration checks are running with a third queued. Hopefully those will go OK?
If they do, it's up to someone else with commit access to merge it.
#ZMap #MacPorts #NetworkScanning #InfoSec #OpenSource
Is Palo Alto actually scanning for their compromised and vulnerable customers? At least from the logs on one of my servers, there is a log entry for a GET HTTP request with a peculiar User-Agent.
To be honest, it would have been a positive step to see vendors actively scanning and notifying their customers.
Maybe they should team up with @shadowserver to perform it at a larger scale?
205.210.31.109 - - [01/Jan/2025:11:18:03 +0000] "GET / HTTP/1.1" 200 186832 "-" "Expanse, a Palo Alto Networks company, searches across the global IPv4 space multiple times per day to identify customers' presences on the Internet. If you would like to be excluded from our scans, please send IP addresses/domains to: scaninfo@paloaltonetworks.com"
Version Fingerprinting Tricks: Automating Software Identification for Vulnerability Scanners.
Presentation done at FIRST conference 2024.
🔗 https://d4-project.org/2024/07/02/version-fingerprinting-tricks.html
I would love ALL, absolutely ALL, #VPS providers to block all out going traffic except port 53, 80 and 443 by default.
To get access to more outgoing ports, the VPS owner would need to explicitly open them one-by-one in a cumbersome, slow and horrendous web based admin panel for EACH VPS host. No APIs.
Maybe all the port scans from basically ALL VPS providers would slow down by limiting the default access. And VPS providers could easily spot and detect abuses quicker and smoother.
But I suspect VPS providers don't give a f***. They earn quick money on customers ordering 100s of VPSes which are (ab)used to scan the Internet randomly.
I submitted a PR to update MacPorts' version of ZMap to version 3.0.0 which was officially released!
https://github.com/macports/macports-ports/pull/19211
It's passed the build bot/CI checks.
However, since I do not have commit access, it is up to someone else to merge it.
Thanks to @zakir for merging one of my PRs in the upstream project before this release!
Thanks to Herby Gillot (not sure where Herby may be on the FediVerse) for giving me a heads up that 3.0.0 was officially out (I had previously been working on PRs for RC2).
@zakir I submitted this PR which seems to have made the CI/build bots happy at least:
https://github.com/macports/macports-ports/pull/19015
Though it would probably still be advisable to get the Assets and branch tags in closer alignment for whenever this progresses beyond Release Candidates?
Regardless, it's up to someone else to merge that PR, but hopefully it improves things a little bit for MacPorts users!
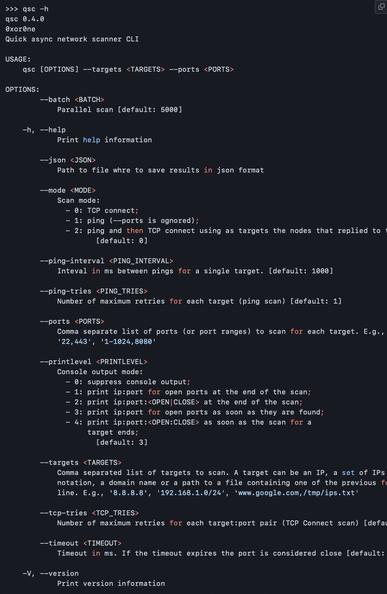
If you're interested in a minimal network port scanner, check out Qscan:
https://github.com/0xor0ne/qscan
and its companion command line tool qsc:
How To Use Nmap (Network Mapper) – A Comprehensive Guide: Basics To Advanced
Nmap is a free and open-source network discovery and security audit tool. In simple terms, network discovery is the process of finding out the devices that are on the network. Whether you are a network engineer or a penetration tester, Nmap is one of the most important tools in your arsenal.
It can help show what devices are connected to your network, can scan what ports they have got open, and also glean some additional information about these devices (eg. those -sY and -O flags). If you suspect a neighbour is using your home network, then this is a tool that will show that connected device.
It runs on Linux, MacOS and Windows and this guide really covers all the basics including the background to IP addresses and ports and how a device connects to a network.
See How To Use Nmap - A Comprehensive Guide: Basics To Advanced
https://bytexd.com/how-to-use-nmap/ https://squeet.me/objects/962c3e10b991f17b01b933bad00f51f55667569f