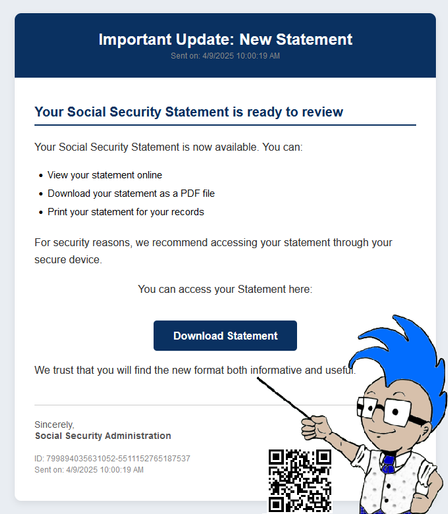
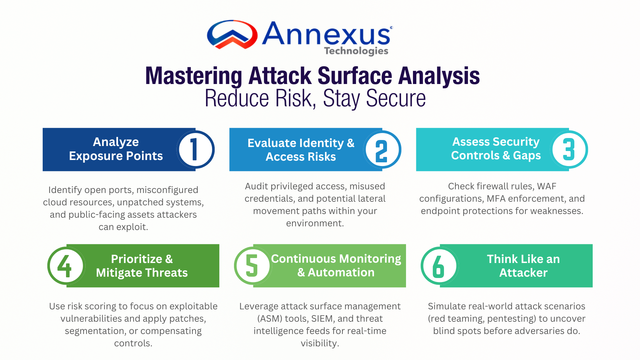
Just released! Our Top Cybersecurity Control selection for Q2 2025 is Continuous Vulnerability Management (CVM).
Why CVM? We’ve analyzed the trends, and today’s threat landscape demands more than periodic scans and reactive fixes. Attackers are exploiting new vulnerabilities within hours, sometimes minutes, of disclosure. You need a program that’s always on, and it’s also becoming a compliance necessity.
Read the analysis on why CVM is the top control for Q2 and how to put it into action: https://www.lmgsecurity.com/why-continuous-vulnerability-management-is-the-top-cybersecurity-control-for-q2-2025/?latest
#Cybersecurity #ContinuousVulnerabilityManagement #VulnerabilityManagement #CVM #RiskManagement #AttackSurface #Infosec #IT #Cyberaware #CISO #Compliance #CyberRisk #Security