Readers of 2600 might find this fun, interesting, and cute...
#Phreak
old meets new
haven’t made use of the flipper much yet aside from some harmless fun and my new flipper tamagotchi pet.
kinda fun that it comes with a red box app tho
So the @connections crew have gotten a chance to do something Amazing:
https://www.youtube.com/watch?v=RBXu7qJ7dNQ
More info soon. If you're in the #denver area and like #phones -- We need archivists and docents and the like who are passionate about technology.
If you were an OG #Phreak and want to help people relive and learn about Ma Bell and her children, go watch the video and fill out the form
A photo from my personal collection. Pacific Telemanagement Services #payphone #publictelephone #phreak
SECRETS OF THE LITTLE BLUE BOX
OCTOBER 1 1971 RON ROSENBAUM
Photography RONALD BARNETT
Still unpacking boxes from my move. Always fun finding this in my tech junk drawer. A redbox I built when I was about 12. Still works! (not on pay phones sadly…)
very interesting youtube channel of a #phreak #phonephreaking #hacking
https://www.youtube.com/@evandoorbell4278
Why is this article significant? The person being interviewed in the article is Lewis de Payne, aka "Roscoe" as the author of the article named him, Kevin Mitnick's perennial #hacker comrade. This article documents the LA phone #phreak scene which was on the verge of becoming part of the early 80s California #hacking scene, a hotspot in the early days.
This one time in 1936 Popeye's nemesis Bluto engaged in a bit of phone phreaking and prank calling, and (spoiler) got beat up for it.
https://www.dailymotion.com/video/x2su0d1
https://popeye.fandom.com/wiki/Hold_the_Wire
#Popeye #Bluto #phreaking #phreak #PrankCall
I’ve clipped interviews with hackers from the 1980’s from longer TV news or documentary segments, you can find the longer videos linked below as well. None of the clips here are longer than a few minutes.
We are talking about primary sources here, hackers in the 1980’s talking about hacking, filmed at the time.
Some of these clips are from longer broadcasts that were essentially lost to the public, that I have retrieved from closed archival sites and uploaded for anyone to view and use.
ABC 20/20 – 1982
Geraldo Rivera interviews infamous California phone phreak and hacker Susan Thunder about phreaking, hacking and the art of dumpster diving at the local telephone company offices. You can find the whole, longer video over at HackCurio and I highly recommend watching it all.
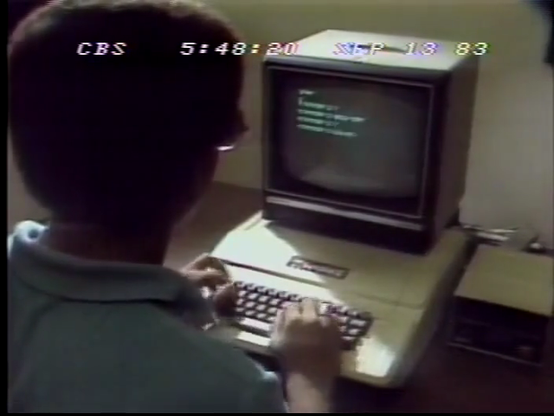
CBS News – 1983
This clip from a longer CBS evening news broadcast from September of 1983 features some brief interview segments with a 17 year old anonymous hacker who describes gaining access to bank systems with passwords shared between friends.
He describes hacking as a communal “project”, with kids physically getting together around a computer to test their wits. You can find the longer broadcast on my channel here.
If you want to learn about why 1983 was a pivotal year for public awareness of the hacker underground you can read that blog.
NBC News – 1983
The first hacker group arrests to make the news nationwide in the U.S. were the raids of members of the 414s. This clip from NBC news also in September of 1983 features a brief interview with the 414s member who would become almost an unofficial spokesman for the group, Neil Patrick.
You can find the longer broadcast on my channel here. You can also find a short but very informative documentary on the 414s here.
Sveriges Television AB – 1984
Below we have two video clips from a Swedish TV documentary about hackers and phone phreaks from back in 1984.
The interview clips themselves are in English and feature Cheshire Catalyst, a phone phreak and activist who edited TAP Magazine, the original underground publication for phone phreaks in the 1970’s.
Cheshire Catalyst talks about hacking and some of the exploits he has been privy to over the years. You can find the whole documentary, in a mixture of Swedish and English, over on Internet Archive here.
CBS News – 1985
“If I break into your computer system how are you going to find me out?”
3 different young hackers talk about their exploits and their lack of fear in regards to consequences in this short clip from CBS News in August of 1985. The full news segment is available to watch here.
BBC – 1989
A brief portion of an interview Edward Austin Singh gave to the BBC for an episode of a TV show called Antenna, which focused on computer viruses and hacking.
Singh had been arrested the year before for trespassing in an English university computer lab and had then been linked to hacking incidents at U.S. government and military installations. He ultimately escaped prosecution because of a lack of laws relating to hacking in the UK at the time of his arrest.
Conclusion
If you enjoyed this blog consider checking out the realhackhistory YouTube channel, Internet Archive uploads and twitter or mastodon accounts.
https://realhackhistory.org/2024/09/09/80s-hackers-in-their-own-words/
#1980s #80s #ABC #CBS #documentary #dumpsterDiving #hacker #hackers #hacking #history #NBC #news #Phreak #Phreaking #video #videos #YouTube
A lot of people consider hacktivism to be a phenomenon associated with the mid to late 90’s, or maybe the late 2000’s with Anonymous and their various spin-offs.
This blog is about a hacktivist campaign run out of Durham, North Carolina, that took place in 1986 though, U.S. hackers taking on the Soviet Union over the arrest of an American journalist.
How do we define hacktivism and hacktivists? Now that is a can of worms in my opinion.
Wikipedia says: “Internet activism, hacktivism, or hactivism (a portmanteau of hack and activism), is the use of computer-based techniques such as hacking as a form of civil disobedience to promote a political agenda or social change.”
Personally I take exception with the language “computer-based”, as to my mind hacktivism can involve anything to do with technology – think “black faxes” or jamming radio or TV signals.
In this case we are looking at hacktivism via phones.
September 12th, 1986, Nicholas Daniloff speaks with the press in Moscow after his release to the U.S. EmbassyOn the 2nd of September, 1986, U.S. News & World Report reporter Nicholas Daniloff was arrested in Moscow, accused by the KGB of espionage.
The Reagan administration was of the opinion that Daniloff was arrested as retaliation for the U.S. detaining Gennadi Zakharov, an employee of the Soviet UN Mission, three days earlier.
Ultimately on September 23rd Daniloff was allowed to leave the USSR after having been released to the U.S. Embassy in Moscow. In turn, Zakharov was allowed to leave the U.S. and return to the Soviet Union.
“Computer Hacker Jams Soviet Phones”, AP, Herald-Journal, 14th September, 1986In the weeks between Nicholas Daniloff’s arrest and his return to the U.S. there was an article run by the Associated Press that appeared in U.S. newspapers. The article centered around the anger caused by the arrest of Daniloff.
Kirk Eidson, a self-described “computer hacker” from Durham, North Carolina, gave an interview in which he described his plan for a “crude pressure tactic”. In coordination with a group of like-minded people, Eidson planned on tying up the phone lines of the Soviet Embassy in Washington, the Soviet Mission to the United Nations, the Soviet airline Aeroflot and “any other phone that the Russians may use within the United States.” His goal was to prevent communication incoming to the U.S. to the USSR on official channels.
“Until he (Daniloff) is released, we won’t release their phones.”
Kirk Eidson, “Computer Hacker Jams Soviet Phones”, AP, Herald-Journal, 14th September, 1986
Eidson’s plan even had a name, like an Anonymous style op, he christened it “Tele-Lock”. Tele-Lock was essentially what I call a “manual style DDoS”, similar to campaigns by groups like Strano Network to get people to physically hit refresh on target webpages at the same time to take them down in the mid 90’s, but in this case the target was phone numbers associated with the USSR.
“Members [of Tele-Lock] make a person-to-person call to a phone used by the Soviets in the United States. The caller asks for Nicholas Daniloff, who, of course, is not there”
Looking at the dates associated with the AP article and events relating to Daniloff’s case I think by the time Tele-Lock was being discussed in newspapers across the United States Nicholas Daniloff had already been released into the custody of the U.S. Embassy in Moscow.
Aeroflot offices, courtesy of Wikimedia CommonsI wonder how Kirk Eidson came to be interviewed for the Associated Press, how the Associated Press came to hear about the Tele-Lock campaign in the first place and how Tele-Lock itself was organized.
Also interesting to note what wasn’t done as part of this hacker campaign against the Soviet Union, as by 1986 hackers in the U.S. were well versed in phone phreak tricks that could make anyone with a phone miserable.
80’s phreaks and hackers could have phone numbers disconnected, reassigned, incoming calls forwarded to other numbers, phone lines reassigned to become pay phone lines and social engineering details of unpublished private numbers associated with individuals, organizations or businesses.
“Durham freedom hacker vows to jam Moscow lines”, AP, Star-News, 14th of September, 1986The fact that this campaign is associated with someone willing to use their real name and disclose their profession (“freelance computer programmer”), combined with the fact that the campaign seems careful to stay within the confines of the law makes me think that this was a campaign organized by the “computer enthusiast” end of the hacker spectrum, as opposed to the “darkside”.
If you were involved in Tele-Lock please get in touch with me on Twitter or via a comment here, I’d love to learn more about this whole incident.
https://realhackhistory.org/2024/07/26/u-s-phone-phreaks-versus-the-ussr-hacktivism-in-1986/
#1986 #Durham #GennadiZakharov #hacktivism #hacktivist #KGB #KirkEidson #NicholasDaniloff #NorthCarolina #phone #Phreak #Phreaking #Russia #SovietUnion #TeleLock #USSR
Am I the only '90s #phreak who developed the life-skill of memorizing my credit card numbers?
When you spot two payphones about a block from one another, and of course neither have a dial tone!
AC14 (2280Hz) Signalling Demo Progress…
The wiring between the relaysets is done with the exception of the connections that go to the #phone end, the #phoneExchange end, and the 4-wire circuit between the two ends of the link.
So, 9 wires remaining then I can start powering it up… but first, I need to find a suitable method of terminating those connections that allows me to add in annamplifier/speaker so you can hear the tones.
It’s back to the sketchbook and eBay searches!
More progress on the AC14 (2280Hz signalling) demo rack!
I’ve fitted all the shelf u-points, which are the strips of spring contacts that mate with the contacts on the back of the relay sets
They're second hand, so I spent lunchtime cleaning off the old wiring. I stopped counting at 60 bits of wire… but there are 160 contacts in total (5x32) - not all had wires on!
The next job is to start putting in the new wiring.
#strowger #telephoneExchange #phone #phreak #telecoms #telephone
Now this is a nice find!
I've been passed a scan of a notebook from the late 1950s containing details of all the #telephoneExchanges in the UK
This sort of information was used by #telephone enthusiasts (UK #phreaks) to navigate their way around the toll (trunk) network
There were various techniques to get yourself onto a trunk, but once you were there the dialling codes in this notebook would get you anywhere in the country!
#phone #telephoneHistory #telecoms #phreak #telephoneHeritage
Metalwork done at last!
This shelf holds 4 cans of #gpo #relays that between them form an AC14 “out-of-area” line.
These would have been used to connect a #phone to a line that was too long for pulse dialling to work reliably.
The two on the left are the #TelephoneExchange end, the two on the right are the subscribers end.
Between them, they convert pulse dialling into bursts of 2280Hz tones which can be transmitted much further without distortion
My new bedtime reading has arrived…
In the UK, AC13 telephone signalling used pulses of 2280Hz to represent the digits of a dialled phone number, call progress state etc.
This training document from 1983 was pretty late in the lifespan of in-band signalling like this, which had been around for 20+ years by this point.
It’ll be fun reading this from a “what would it do if I poked $thing at $time” point of view
#telephoneHistory #telecomHistory #telephone #telecoms #phreak #phreaking #phones
This is extremely silly.
I have a Nokia 105 #phone. No data or apps. Just a plain, dumb, mobile phone
Using a sim from aa.net.uk I've connect it to the C*Net VoIP network https://ckts.info
It's accessible on a CNet number, and can place calls just like any other phone on CNet!
Do I need this?
No.
Can it make normal calls?
Absolutely not!
Is it useful?
Not in the slightest.
Is it cool as heck?
Absolutely!
I'll make a demo video later…