Die 7. Folge unseres Podcasts ist da! 🎉
In dieser Episode sprechen wir mit Hagen Molzer, Leitender Berater und Experte für Active Directory Security, über das spannende Thema Tiering-Modell.
Wir klären, was sich hinter dem Begriff verbirgt, warum eine strukturierte Gliederung der IT-Infrastruktur nach Sicherheitsstufen heute so entscheidend ist und wie Unternehmen dadurch ihre Angriffsflächen deutlich reduzieren können.
Mit dabei:
• Praxisnahe Einblicke aus dem Beratungsalltag
• Anschauliche Beispiele
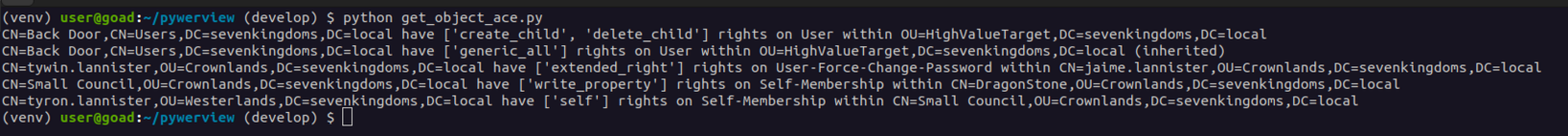
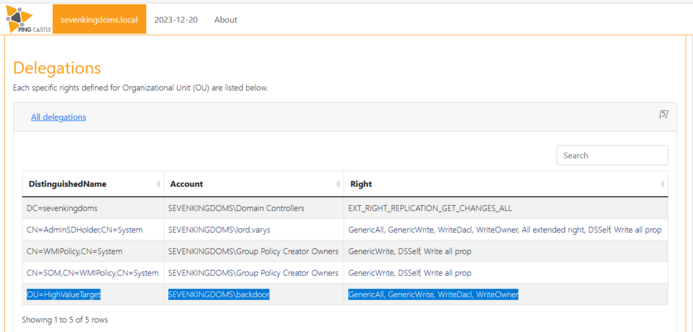
• Hilfreiche Tools wie BloodHound und PingCastle
• Tipps für den Einstieg in ein sicheres Tiering-Konzept
Perfekt für alle, die IT-Sicherheit strategisch denken und nachhaltige Schutzmaßnahmen etablieren möchten.
Höre gerne rein:
🎧 Spotify: https://open.spotify.com/show/63K9JjKKOdewLx2Ma0DuNE
🍏 Apple Podcast: https://podcasts.apple.com/de/podcast/it-security-inside/id1751424875
🌐 Unsere Website: https://cirosec.de/podcast/
#ITSicherheit #TieringModell #ActiveDirectory #CyberSecurity #Podcast #BloodHound #PingCastle #ITSecurityInside