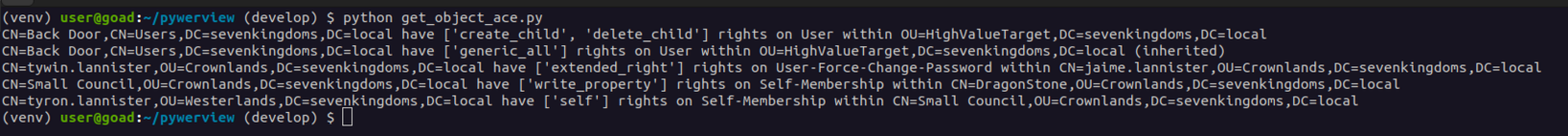
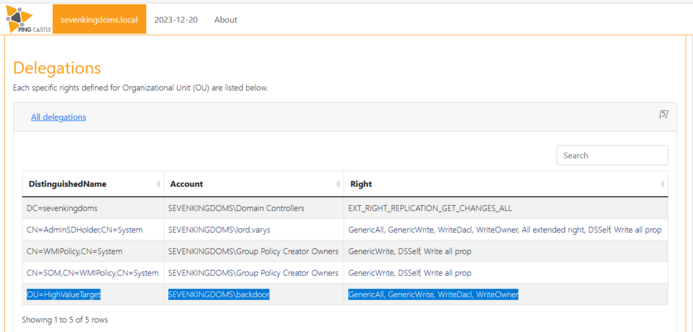
RT by @SwiftOnSecurity: Real-World #PingCastle Finding #14: Misconfigured Certificate Templates
The attackers gained Domain Admin rights within 2 hours after the initial infection on a recent IR engagement, investigated by @NOP_0x090. That’s quick - how could they gain DA so fast? I’m glad you asked.
SpecterOps published their ground-breaking paper “Certified Pre-Owned” over two years ago, and I think that ADCS (Active Directory Certificate Services) as an attack vector is broadly known on the red side - but not as much on the blue side.
See the screenshot below? Yep, that’s how they managed to gain DA rights in under 2 hours.
The topic of abusing misconfigured certification templates is far more complex than would fit here in a single tweet, so I encourage you all to
a) run PingCastle first and check for issues on certificate templates, and if something shows up,
b) check some of the great resources that talk about how an attacker can abuse the various misconfigurations and how we can detect them (or how to fix the misconfigurations). Some recommended blogs are [2], [3] and [4]
Good luck ☘️
[1] https://posts.specterops.io/certified-pre-owned-d95910965cd2 [2] https://www.riskinsight-wavestone.com/en/2021/06/microsoft-adcs-abusing-pki-in-active-directory-environment/ [3] https://m365internals.com/2022/11/07/investigating-certificate-template-enrollment-attacks-adcs/ [4] https://www.blackhillsinfosec.com/abusing-active-directory-certificate-services-part-one/
🐦🔗: https://nitter.oksocial.net/malmoeb/status/1744770135964237840#m
[2024/01/09 17:16]