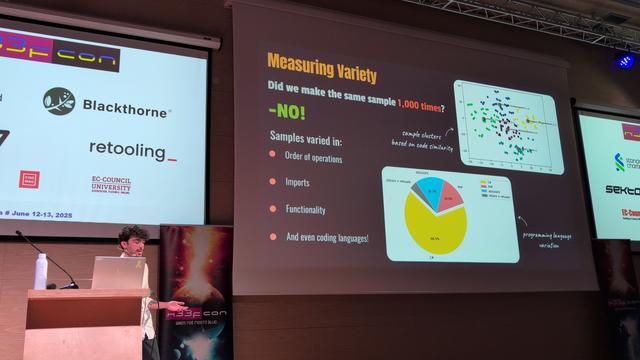
Rem Dudas and Bar Matalon on the use of AI for generating malware. Interesting to see the variation of malware stemming from the repetition of the same question.
#x33fcon
Dirk-Jan Mollema on the use of roadoidc and the use of federated credentials which can be used for persistence.
Roei Sherman on the Snowflake breach but more generally on the shared security model when using cloud. Certainly when it comes to SaaS the gap today is often bigger than thought.
Roberto Rodriguez' latest experiment. Give it a shot.
And off we go!
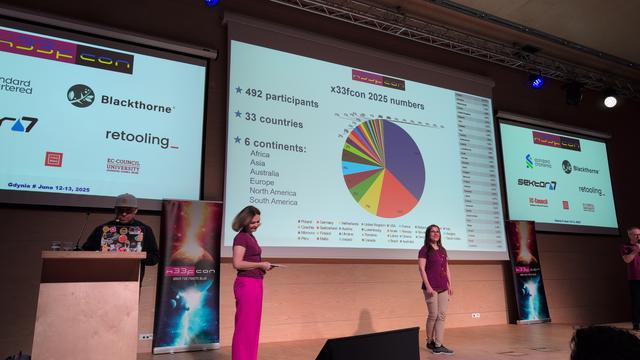
We are 492 like-minded people this year. Let's make this a great 9th edition!
Just arrived in Gdynia, I'm excited for the #x33fcon tomorrow!
Surprise! Really excited to announce that the next "𝑺𝒐𝒄𝒊𝒂𝒍 𝑬𝒏𝒈𝒊𝒏𝒆𝒆𝒓𝒊𝒏𝒈 & 𝑶𝒑𝒆𝒏-𝒔𝒐𝒖𝒓𝒄𝒆 𝑰𝒏𝒕𝒆𝒍𝒍𝒊𝒈𝒆𝒏𝒄𝒆 𝒇𝒐𝒓 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝑻𝒆𝒂𝒎𝒔" open class will be happening at x33fcon in Gdynia, Poland!!
This is an intensive, 2-day training. We will cover:
🔹 Timeless Social Engineering Attack Scenarios: The tricks that keep working (and why).
🔹 The Psychology behind social engineering (we will go well beyond influence tactics!!)
🔹 Hybrid & advanced attack techniques that combine multiple attack verticals.
🔹 The use of AI in all phases of the social engineering kill-chain.
🔹 OSINT: How to conduct reconnaissance on a target (business / person) and what to look for.
🔹 Highly practical open-source intelligence (OSINT) tools & techniques that facilitate attack scenarios.
🔹 Blue Team Countermeasures: How to disrupt social engineering attacks & create a defense strategy.
...but there will also be some surprises 🤫 ✨ ✨
If you're attending #x33fcon this year I look forward to seeing you there!
Class Details & Registration: https://www.x33fcon.com/?fbclid=IwAR2B-2KwiZ3dJeKl-#!t/SE_OSINT.md
Ahoy, me hearties! Exactly one week ago we bravely set sail across Gdansk Bay aboard our man-o-war chanting, bilging and looting. Luckily we did not end up in Davy Jones's locker!
While looking back at last week's events leaves me pondering with a heavy heart, I hang on to the thought that we meet again in only 50 weeks!
Counting down!
And block your agenda's for the 12th and 13th of June next year!
A kind reminder from Andy Robbins and Jonas Bülow Knudsen to regularly assess the security of your Active Directory environment using tools such as Bloodhound and Pingcastle.
These tools are free to use. Do it! No excuses!
#bloodhound #pingcastle #cybersecurity #whenredmeetsblue #x33fcon
And here we go!
For its 8th edition, x33fcon is hosting 416 participants from 30 countries.
Let the games begin!
Happy to see Kuba Gretzky kicking it off with one of my favorite topics and what can indeed be labeled as one of the biggest elephants in the cybersecurity community's room. How to prevent bad guys from using red teaming tools?
For sure there are no easy cures but we should at least acknowledge the issue and work towards solutions.
Ready for x33fcon!
Wanna spend two days finding evil in #pcap files? Erik Hjelmvik is teaching a class in Network Forensics for Incident Response at #x33fcon in Poland on June 11-12.
https://www.netresec.com/?page=Blog&month=2024-03&post=Network-Forensics-training-at-x33fcon
🇬🇧 Recordings from the x33fcon Europe 2023 conference available now
🇵🇱 Są już dostępne nagrania z konferencji x33fcon Europe 2023
https://www.youtube.com/playlist?list=PL7ZDZo2Xu3332bKrXyCb0VEg52nqmMAcv
link without tracking / link bez śledzenia
https://yewtu.be/playlist?list=PL7ZDZo2Xu3332bKrXyCb0VEg52nqmMAcv
I am very excited to watch the talks from x33fcon this year!
We’ve taken pretty much all the Active Directory tradecraft from the years and distilled it into this course. The hard part has been finding the Goldilocks zone for intermediate hackers - not too entry level, not too AD 1%, but just right. It’s being given at @x33fcon to a small class. We’d love to see you there. https://www.x33fcon.com/#!t/adexploit.md
@Viss It is! I was actually hoping to do a "Baltic trip" by combining #x33fcon with #SecurityFest but in hindsight I submitted kind of a crappy idea... oh well.
I am NOT going to #RSAC - and I'm VERY cool with that.
I AM going to #HackTheCapitol, @x33fcon #x33fcon, and #HagueTIX2023 though - and very much looking forward to them!
📢🔔 Just 1 more day to submit your talk at X33f Con cc @x33fcon! https://cfptime.org/cfps/1635/ #cfp #infosec #x33fcon