"The problem with rainbow tables is that they have uses¹, but if you're unsure whether you need them, then you really don't. And this creates a weird effect where the only people who use them ... don't need to ask about them." ~ Uly
#Rainbowtables
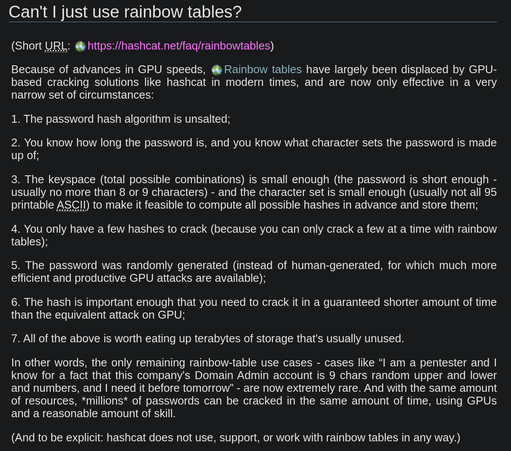
Next time password cracking comes up conversationally and someone says "And can't you can just use rainbow tables" ... send them this.
https://hashcat.net/faq/rainbowtables
tl;dr They are only worthwhile in a very specific (and rare) set of circumstances.
For some reason I didn’t have the NTLM-9 #RainbowTables #BitTorrent files listed on https://infocon.org/
Now fixed! It’s a big 6+ TB rainbow table.
La segunda parte del artículo de #criptografia para #dummies ya está disponible. Os contamos como funcionan los principales ataques y que se puede hacer para remediarlos
#ROOR7 #cryptography #seguridad #security #mitm #rainbowtables #replay #cyber
https://ibolcode.net/roor/2024-05-criptografia-para-dummies--parte-ii
New #Approach in the #RainbowTables Method for Human-Like #Passwords #2020
https://ieeexplore.ieee.org/document/9039311
not #openaccess :`(
#Rainbowtables #explained How they work and why they’re (mostly) #obsolete
#Rainbowtables are #precomputed tables of #hashes used to #crack #passwords #Ophcrack is a free open-source #program that uses rainbow tables to crack #Windows log-in passwords. It can import hashes from a variety of formats, including dumping directly from the #SAM files of Windows, and can be run via the #commandline or using the program’s #gui
(1/7)
Apple AirDrop leaks user data like a sieve. Chinese authorities say they’re scooping it up.
https://arstechnica.com/security/2024/01/hackers-can-id-unique-apple-airdrop-users-chinese-authorities-claim-to-do-just-that/ #Apple #airdrop #data #leak #china #concession #RainbowTables
#Apple #AirDrop leaks user data like a sieve. Chinese authorities say they’re scooping it up: [...] exploiting a weakness Apple has allowed to go unfixed for 5 years, 20240112,
by Dan G,
https://arstechnica.com/security/2024/01/hackers-can-id-unique-apple-airdrop-users-chinese-authorities-claim-to-do-just-that/
#insecureEmissions #identityHash #rainbowTables
Na super. Jetzt muss ich mein langjährig genutztes Passwort "345gs5662d34" in etwas schwieriges ersetzen... Man hat ja sonst nichts zu tun :mastocheeky:
l+f: Das rätselhafte root-Passwort | Security https://www.heise.de/news/l-f-Das-raetselhafte-root-Passwort-9299197.html #Hacking #CyberCrime #RainbowTables #BruteForce
.@blacktraffic Great question!
Here are some reasons why #RainbowTables are obsolete for #password #cracking:
In any given password database, 92-98% of the passwords are going to be created by highly predictable humans (as opposed to being randomly generated.) Because of this, modern password cracking is heavily optimized for exploiting the human element of password creation, concentrating on probabilistc methods that achieve the largest plaintext yield in the least amount of time. As such, modern password cracking tools and techniques have evolved to become highly dynamic, requiring agility, flexibility, and scalability.
This is evident when looking at how #Hashcat has evolved over the last decade. Hashcat used to be heavily optimized for raw speed, but today it is optimized for maximum flexibilty (plus, lite, and cpu merged into a single code base, dropped the 15-character limit, introduced pure kernels, brain, and slow candidate mode, etc.) This need for dynamicity is also why we largely still use GPUs today, rather than having moved on to devices with potentially higher throughput, such as FPGAs or even ASICs.
With this in mind, it's rather easy to see that rainbow tables are the antithesis of modern password cracking. Rainbow tables are static, rigid, and not at all scalable. They directly compete with unordered incremental brute force, which in the context of modern password cracking, is largely viewed a last resort and generally only useful for finding randonly-generated passwords (although, can also be useful in identifying new patterns that rules and hybrid attacks failed to crack.) They also do not scale. If you have a handful of hashes, rainbow tables will likely be faster than brute forcing on GPU. But if you are working with even a modestly large hash set, rainbow tables will be slower than just performing brute force on GPU, even if you are using GPU rainbow tables.
Overall, rainbow tables are an optimization for an edge case: cracking a small amount of hashes of an algorithm for which we have tables, within the length and character sets for which we have tables, that fall within that 2-8% of hashes that we cannot crack with probabilistic methods. And even then, most people who are #security conscious enough to use use random passwords aren't going to make them only 8 or 9 characters long, so the percentage of those passwords that will actually be found in your tables will be much lower.
The questions you have to ask yourself: is that worth the disk space and the bandwidth to download and store rainbow tables, and do you really care about that 2-8%, keeping in mind that only a small percentage of that is going to fall within the tables you have? If the answer is "yes", then continue to use rainbow tables. However, the for the vast majority of us, the answer for the past 11 years has been a resounding "no." And that's why rainbow tables are, by and large, a relic of a bygone era.
With that said, rainbow tables do still have some utility outside of #passwords. For instance, cracking DES or A5/1 #encryption. There's also the cousin of rainbow tables, lossy hash tables (LHTs), which have some utility as well for things like old Microsoft Office and Adobe Acrobat encryption keys.
Dear wannabe hackers at #cccamp19, do come to the #Digitalcourage tent (Q9) at 6pm today if you wanna acquire haxor skillz.
You will learn how to pwn poorly coded web appz. You will go home with a licence to hack issued by yours truly.
#xss #sqlinjection #rainbowtables #1337 /c
You can unscramble the hashes of humanity's 5 billion email addresses in ten milliseconds for $0.0069 https://boingboing.net/2018/04/09/over-the-rainbow-table.html #quantityhasaqualityallitsown #de-identification #re-identification #computerscience #cloudcomputing #rainbowtables #cryptowars #crypto #Post #gdpr