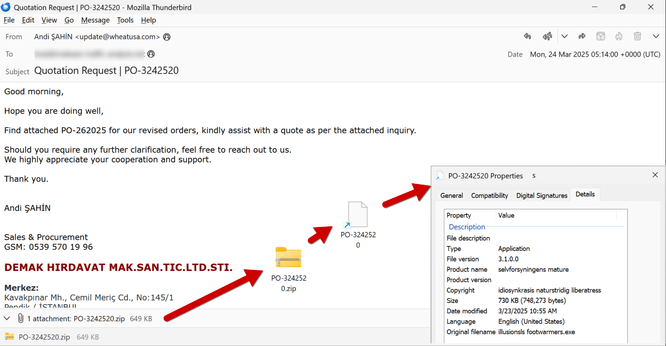
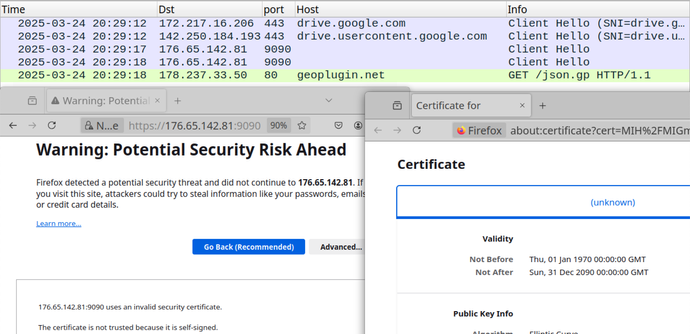
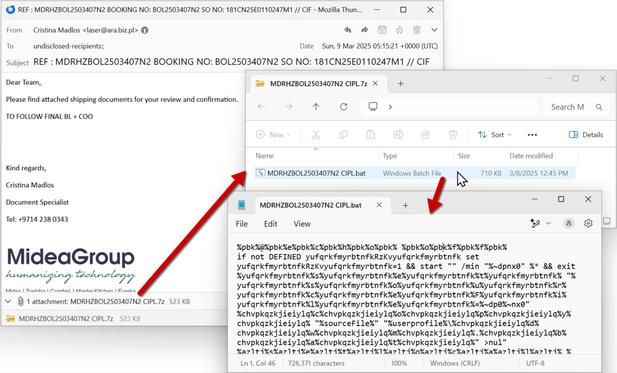
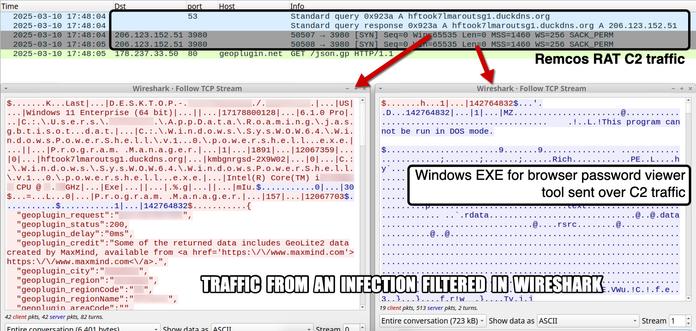
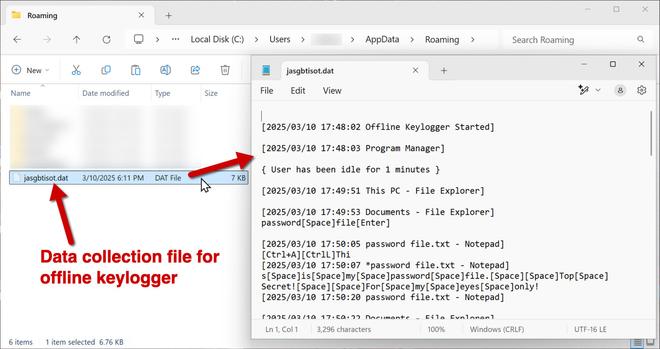
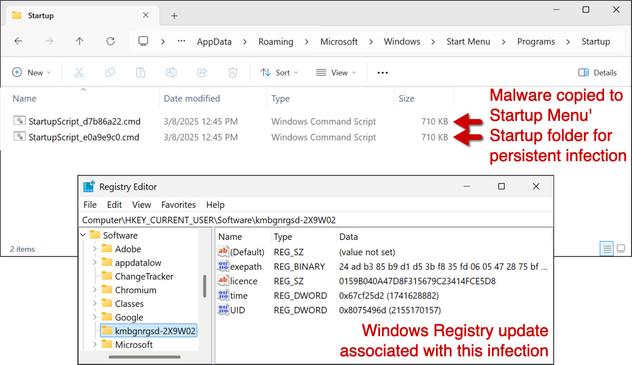
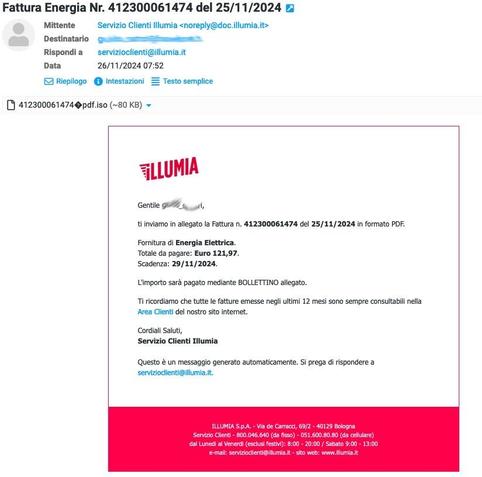
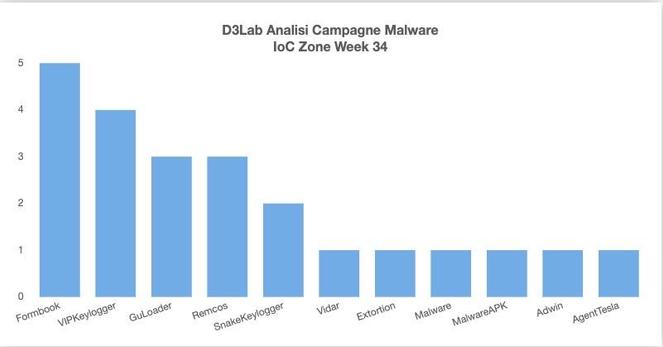
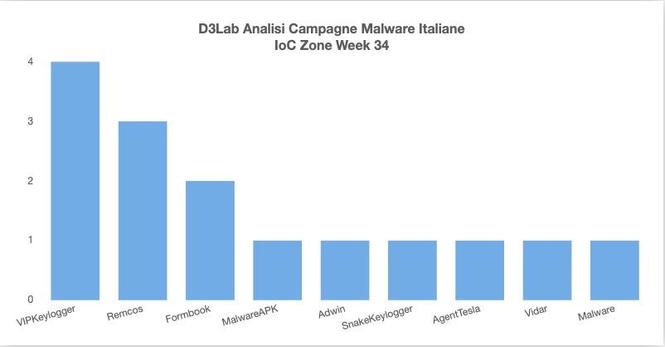
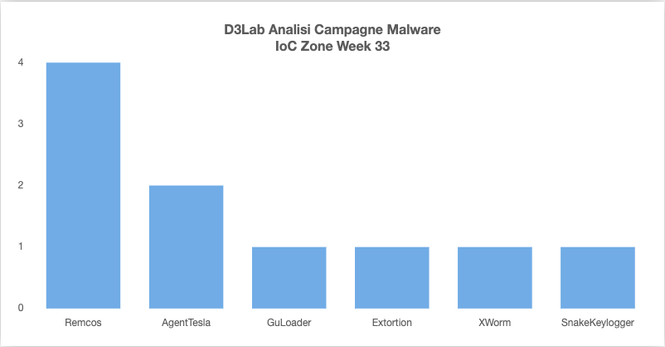
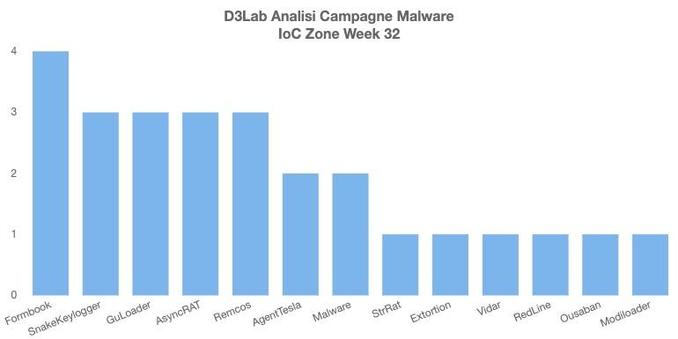
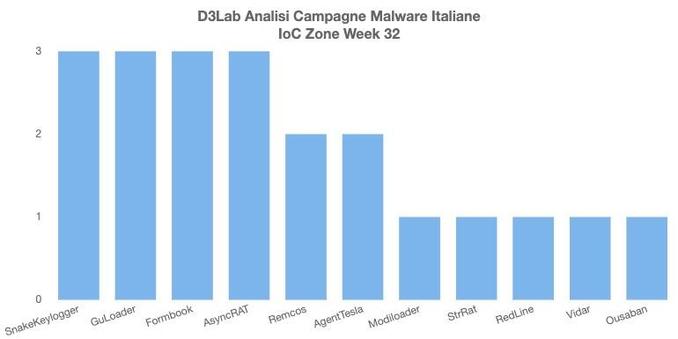
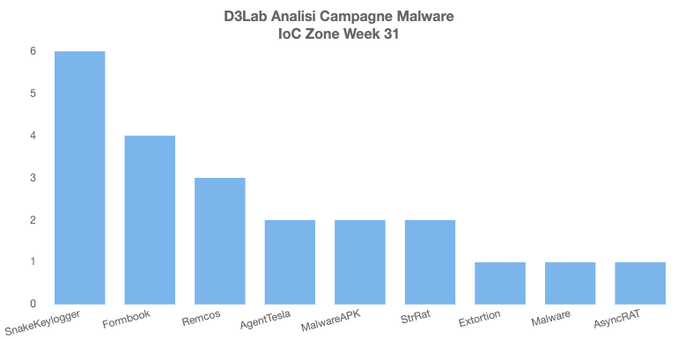
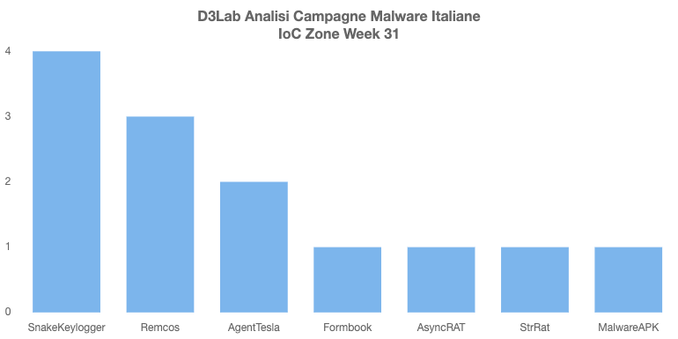
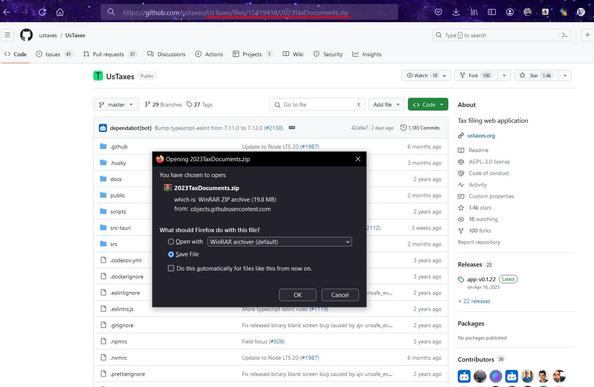
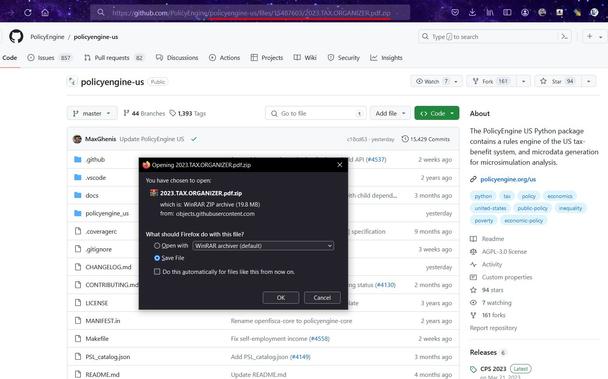
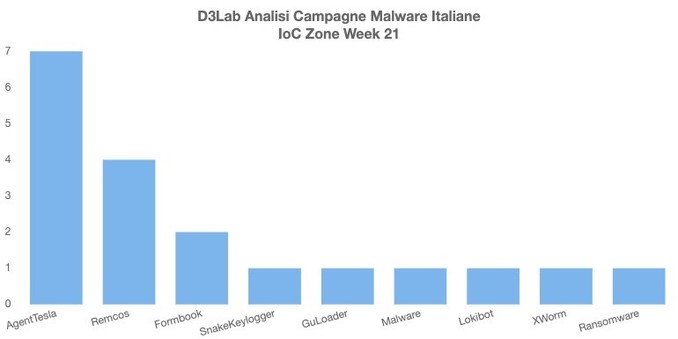
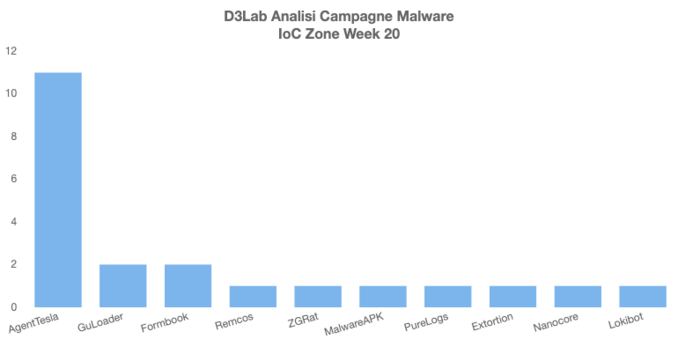
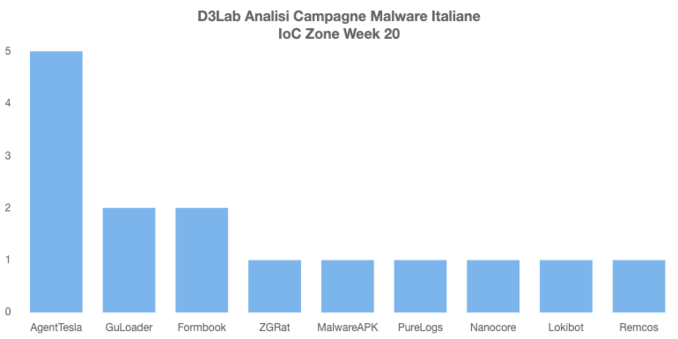
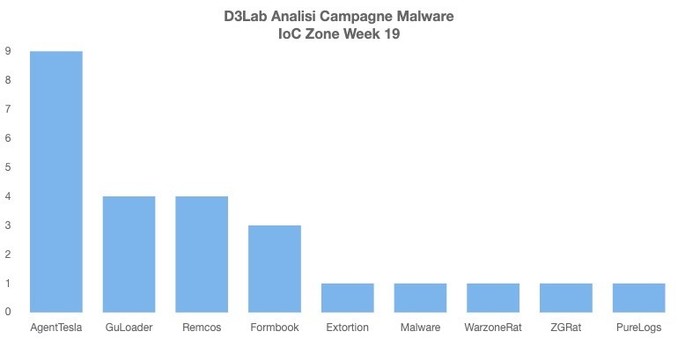
Remcos RAT Delivered via MSHTA and PowerShell in Fileless Malware Campaign
Hashes (SHA256) are commonly used to identify people who are at risk of falling into a relationship with a different party or organisation. and their potential impact on their respective social status is revealed.
Pulse ID: 6840214f09754e0950515733
Pulse Link: https://otx.alienvault.com/pulse/6840214f09754e0950515733
Pulse Author: cryptocti
Created: 2025-06-04 10:34:55
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#CyberSecurity #InfoSec #Malware #OTX #OpenThreatExchange #PowerShell #RAT #Remcos #RemcosRAT #bot #cryptocti