🚀🔒 TeraWave's "cutting-edge" #satellite network is apparently a glorified browser test. Who knew secure communication required JavaScript skills? 🤔✨
https://www.blueorigin.com/terawave #TeraWave #CuttingEdge #BrowserTest #SecureCommunication #JavaScriptSkills #HackerNews #ngated
#SecureCommunication
Oh look, the #wizards of secure communication are "on it" 🤹♂️—rest easy knowing your cryptographic nightmares are still under construction. Because nothing says "confidence" like a webpage with zero details and a promise to return later. 🔮🔧
https://gpg.fail #securecommunication #cryptography #technews #cybersecurity #HackerNews #ngated
🎈Happy 13th birthday to @@threemaapp 🎂, the messenger that's been keeping our conversations private and secure for over a decade! Here's to many more years of protecting our digital freedom! [link] #ThreemaBirthday #DigitalPrivacy #SecureCommunication
#PrivacyMatters
#SecureMessaging
#DigitalSecurity
#PrivacyFirst
#PrivacyRevolution
#SecureOnline
#PrivateCommunication
Готово — английский перевод + хэштеги в конце.
Below is what I found about the Mycelium developers and the project itself (its goals, architecture, and status).
👤 Who is behind Mycelium — developers and initiators
Mycelium is developed by ThreeFold (ThreeFold Tech / ThreeFold Grid).
In official announcements, a contributor named **Lee Smet** is mentioned as leading the effort to build a new IPv6 overlay network.
The project is open-source, with the repository hosted on GitHub.
ThreeFold is an organization promoting decentralized networks and infrastructure. Mycelium is a component of their ecosystem — not a third-party plugin, but a native project.
🛠 What is Mycelium — architecture and key properties
Mycelium is:
An IPv6 overlay network written in Rust.
When joining, each node receives an IPv6 address from the `400::/7` range.
All connections are end-to-end encrypted; each node has a public/private key pair, and its network address is cryptographically tied to the private key.
The network is **locality-aware** — routing chooses optimal paths with minimal latency.
It supports multiple transport protocols: TCP, QUIC, etc.
Routing is inspired by (or partially based on) the **Babel routing protocol**.
Mycelium can operate without a TUN interface (as a **message bus only**) for lightweight encrypted data exchange.
The repository includes a **message-system** layer enabling encrypted messaging above the network layer.
📡 Project goals, design, and future direction
Mycelium aims to deliver a **secure, efficient and scalable** alternative to the traditional Internet with focus on privacy, decentralization, and resilience.
It is designed as part of the wider **ThreeFold Grid** ecosystem — serving as the network backbone for their services.
The developers target **planet-scale scalability**.
Mycelium is positioned not only as a private networking solution, but as infrastructure for many scenarios: secure P2P communications, self-hosting, IoT networking, decentralized services, cloud infrastructures, CDN-like usage, etc.
As of 2024–2025, Mycelium remains under active development — scaling is a key focus.
✅ Status, implementation and limitations
Mycelium is operational with builds available for Linux, macOS, Windows; iOS and Android are planned / in beta.
Documentation claims support for **up to ~100,000 nodes** within a single network.
Planned improvements include: enhanced resilience, NAT support, QUIC hole-punching, protocol expansion, easier deployment.
Mycelium is an actively maintained open-source project under the Apache-2.0 license.
🔎 Summary — strengths and potential risks
**Strengths:**
High-level security and privacy: true E2E encryption and crypto-bound addressing.
Decentralization — no single point of control.
Flexible: full IPv6 network or lightweight encrypted message bus.
Suitable for many use cases: private networking, P2P, IoT, remote work, decentralized services, private Internet access.
**Limitations / risks:**
Still maturing — global scaling goal remains unproven.
P2P overlay networks always depend on trust and correct configuration of peers.
Unclear real-world adoption and number of active nodes — affects reliability.
Some external services may still see public exit IP addresses (e.g., through NAT), which may reduce anonymity in practice.
If you want, I can **check live network metrics** — number of active nodes, adoption level, known issues, etc.
Hashtags
#Mycelium #ThreeFold #OverlayNetwork #IPv6 #RustLang #EndToEndEncryption #Decentralized #CyberSecurity #P2P #PrivateNetworking #SecureCommunication #NextGenInternet #ZeroTrust #NetworkingTech
Your privacy deserves the best protection! 🔒
With Zoho Mail, your data stays safe, secure, and private — always. 💼✨
Switch to smarter communication with Risedigitech, your trusted #ZohoAuthorizedPartner. 🚀"
Book your FREE demo today!
📞 +91 8770896004
🌐 Visit: https://zurl.co/3hJMG
#ZohoMail #DataSecurity #EmailPrivacy #Risedigitech #ZohoPartner #SecureCommunication #DigitalWorkspace #CloudMail #TechForBusiness #BusinessSolutions #zohosoftware #mail #zoho
Need reliable long-distance serial communication in mission-critical operations?
The Versitron RS-530 Fiber for Defense ensures secure, interference-free data transmission for tactical and command networks.
How do you safeguard your serial communications in the field?
#Versitron #RS530 #DefenseTech #FiberOptic #SecureCommunication #MilitaryNetworking
Managing secure communication networks for government or defense?
The Versitron RS-530 Converter for Government Security provides precision, reliability, and data integrity for mission-critical systems.
What’s your top priority encryption, speed, or reliability?
#Versitron #GovernmentSecurity #RS530 #DefenseSystems #SecureCommunication
POP3, SMTP, WebDAV, CRM – vier Kürzel, die klingen wie Nebencharaktere aus einem Sci-Fi-Film, sind aber heimliche Helden unserer digitalen Kommunikation. Bei mailbox lieben wir Standards, aber wir wissen auch: Die muss man erst mal verstehen. Entdecken Sie, was wirklich hinter diesen Protokollen steckt – klar erklärt und mit einem Augenzwinkern. Verraten Sie uns danach, welches IT-Kürzel Sie als Nächstes gelüftet haben wollen!
#mailboxorg #TechExplained #SecureCommunication #PrivacyFirst
Quantum Key Distribution Investment by Canadian Government
Author(s): Scott Douglas Jacobsen
Publication (Outlet/Website): The Good Men Project
Publication Date (yyyy/mm/dd): 2025/05/05
Cordell Grant is a pioneering aerospace engineer, cryptography enthusiast, and well’s CEO and co-founder of QEYnet. With over 20 years of experience leading low-cost, high-performance satellite programs—including BRITE-Constellation, CanX-4&-5, and GHGSat-D—he has been at the forefront of innovative space technology. Cordell’s academic background spans a Bachelor of Science in Mathematics from Cape Breton University, a Bachelor of Engineering from Dalhousie, and a Master of Applied Science from the University of Toronto Institute for Aerospace Studies, Space Flight Laboratory. His passion for space exploration and secure communications fuels his pioneering satellite-based quantum key distribution work. Renowned for merging space and cryptography. Quantum key distribution (QKD) is a cryptographic method that uses quantum mechanics to exchange encryption keys securely. Unlike classical encryption, QKD transmits individual photons, making interception detectable. Ground-based QKD relies on fibre optics, which introduces signal loss, limiting its range. Space-based QKD, using satellites, enables global encryption key exchange without intermediaries. The Canadian Space Agency invests in QEYNet to counteract threats from quantum computing, which could break classical encryption. QKD secures long-term satellite communications by allowing in-orbit re-keying. This technology reduces costs, enhances security, and facilitates the development of scalable global quantum networks.
Scott Douglas Jacobsen: What is quantum key distribution?
Cordell Grant: Quantum key distribution (QKD) is a cryptographic technology that has been in development for about 40 years, first proposed in the early 1980s. At its core, QKD enables the secure exchange of encryption keys using quantum mechanics.
Unlike classical key exchange methods, QKD transmits individual photons—quantum particles of light—from one party to another. Each photon is polarized in a specific but randomly chosen way.
Fundamental quantum principles ensure that any attempt to intercept these photons disturbs their state, making eavesdropping detectable. This property guarantees the security of the exchanged encryption keys, as unauthorized interception cannot go undetected.
QKD’s reliance on the laws of physics rather than computational complexity makes it exceptionally secure. However, a key challenge has been reliably transmitting single photons over long distances. This is where advancements in QKD technology, including space-based systems, play a crucial role.
Jacobsen: How does QKD technology enhance data security in space compared to ground-based methodologies? Is there a significant difference?
Grant: There is a significant difference between ground-based and space-based QKD. On the ground, photons are typically transmitted through fibre optic cables. While fibre optics are widely used for data transmission, they introduce signal loss. At the single-photon level, this loss becomes significant, limiting the effective range of QKD to about 100–150 kilometres without using trusted relay nodes.
If we attempt to scale QKD globally using fibre optics alone, we would require numerous intermediate stations to receive, store, and retransmit the encryption keys, which introduces security vulnerabilities.
Space-based QKD offers a more efficient solution. Instead of relying on fibre optics, photons are transmitted directly between ground stations and satellites. In space, there is no medium to absorb or scatter the photons, significantly reducing transmission loss over long distances.
A QKD-enabled satellite in orbit can establish secure key exchanges with multiple ground stations worldwide. By acting as a trusted intermediary, the satellite allows distant locations on Earth to securely share encryption keys without relying on fibre optic infrastructure or multiple ground-based relays.
This approach enhances global cybersecurity and enables highly secure communications for governments, financial institutions, and critical infrastructure.
Jacobsen: Why is the Canadian Space Agency investing $1.4 million in QEYnet?
Grant: The Canadian Space Agency has invested in this technology, specifically space-based quantum key distribution, for about 15 years. Canada has determined that this technology is valuable for various reasons.
The primary reason often cited for the importance of QKD, particularly space-based QKD, is the looming quantum threat posed by quantum computers. The basic premise is that quantum computers are advancing rapidly and becoming increasingly powerful. Once they reach a certain level of computational capability, they can break many encryption methodologies widely used worldwide.
A key example is public key encryption, which is used when logging into your bank’s website. This type of encryption relies on mathematical complexity, but that complexity applies only to classical computers. Quantum computers, however, are exceptionally efficient at solving the mathematical problems that underlie this encryption.
As a result, the encryption technologies we currently rely on are vulnerable to the advent of quantum computing. Since encryption is embedded in nearly every aspect of digital security, replacing existing systems with quantum-secure alternatives will take time.
QKD is one of the technologies being explored as a potential replacement. It ensures secure communication in preparation for what is sometimes called “Y2Q”—when quantum computers become powerful enough to break conventional encryption.
Jacobsen: Are we suggesting that Y2K wasn’t a real issue?
Grant: It was a real issue but wasn’t a major crisis because we prepared for it in advance. The hope with Y2Q is that the outcome will be similar—we will have taken proactive measures, preventing a catastrophic failure of banking systems or any other critical infrastructure by having quantum-secure systems in place ahead of time.
That’s the typical rationale for QKD. However, at QEYNet, our perspective is slightly different. Numerous applications already do not rely on the types of encryption at risk from quantum computers.
When you examine these applications, many employ surprising methods to distribute encryption keys—often involving the physical transport of key material. In the military, for example, encryption keys are frequently distributed using physical hardware, with large cryptographic devices transported globally to support troop deployments.
Similarly, diplomatic missions often carry physical encryption keys. A diplomat, for instance, might transport new key material to an embassy in a diplomatic pouch, which is protected from search and seizure at customs.
For our immediate use case—specifically, the one funded by the Canadian Space Agency—we are focused on securing communications for spacecraft.
Most people aren’t aware that, much like a spacecraft launches with all the fuel it will ever have, it also launches with all the encryption keys it will ever use. This is simply because transmitting new keys to an orbiting satellite is extremely difficult—and expensive.
Because satellite missions can last for decades, relying on conventional encryption methods, like those used in banking, may not be viable over the entire mission duration. The security of these encryption methods cannot be guaranteed indefinitely.
With QKD, we enable spacecraft to be re-keyed, making them more secure and fundamentally shifting the paradigm in the space industry. By offering QKD technology to other spacecraft providers, we help ensure their satellites remain protected throughout their operational lifespan.
Jacobsen: What are the benefits of successfully demonstrating space-based QKD technology?
Grant: Ultimately, we hope to prove that QKD works in space with this demonstration. Designing this hardware, testing it in a lab, or conducting field trials are just a few things. It’s entirely different to successfully execute QKD between Earth and an orbiting satellite 600 kilometres above.
We aim to demonstrate that all the analysis, mathematics, and testing done so far hold up in a real operational environment. It’s time to combine the pieces and prove we can achieve this in a compact system. The hardware that will be placed on the spacecraft is about the size of a two-litre milk carton. Yet, it will detect individual photons from 600 kilometres away.
Jacobsen: What cost challenges may arise with QKD technology in space? Any new technology tends to be more expensive than well-established alternatives with lower performance or efficiency.
Grant: Yes, there’s no doubt that launching anything into space is costly. One of the key differentiators of QEYNet is that we have deliberately worked to minimize these costs.
Many existing space-based QKD solutions are highly complex, driving up costs. We’ve taken two key steps to make our system more affordable, particularly for spacecraft manufacturers looking to secure their satellites.
First, we have placed the receiver in space rather than the transmitter. In QKD, the receiver is generally the more straightforward component. In contrast, generating individual, polarized photons is technically complex and requires significant data processing. Performing this photon generation onboard a spacecraft would be incredibly challenging due to limited resources such as power, processing capability, and weight constraints. Keeping the receiver in space significantly reduces the system’s complexity and cost.
Second, we have designed our system to eliminate many highly complex and resource-intensive components typically in QKD technology. Traditional QKD systems require highly sensitive detectors to measure individual photons. The most advanced detectors are designed for maximum efficiency, but they add to the overall cost and complexity of the system.
They need to be cooled to about minus 80 degrees Celsius, which requires extensive thermal control technology onboard the spacecraft and large radiators to dissipate excess heat. Instead, we use less efficient detectors that operate at room temperature. This allows us to eliminate all the additional hardware and complexity associated with cooling systems.
Another challenge with these so-called “better” detectors is that they are fibre-fed. This means they require a fibre optic cable in front of them and all the light collected from 600 kilometres away must be precisely focused by a large telescope onto the tiny tip of the fibre. This process must be executed in a highly dynamic thermal environment with constant changes, adding to the system’s complexity.
By contrast, the detectors we use do not require fibre feeding. They have a larger detection area, allowing us to shine the light directly onto them, eliminating the need for fine-pointing mechanisms and complex optical alignment.
These design choices reduce the cost of the satellites we will ultimately deploy by at least an order of magnitude, making the technology significantly more affordable and accessible.
At the very least, our solution is much more efficient than the existing methods of encryption key distribution—such as physically transporting hardware and personnel worldwide. Traditional methods are not only expensive but also pose security risks. Given these factors, we are confident that our approach will remain cost-competitive.
Jacobsen: What might be the broader benefits of QEYNet’s demonstration for quantum networks?
Grant: As I’ve described, the immediate application is spacecraft security. Once we successfully demonstrate this capability, we will validate the first half of our initial vision, where a satellite performs QKD exchanges with two separate locations and acts as an intermediary between them.
In this trial, we aim to demonstrate the ability to facilitate key exchanges between Earth and an orbiting satellite and between two separate locations on Earth via the satellite. If we achieve that, it opens up a wide range of possibilities.
One of the longstanding challenges with quantum networks is the chicken-and-egg problem. The technology already exists to build quantum networks for localized areas, such as an urban region. In any given city, for instance, you could leverage existing fibre optic infrastructure to create a functional quantum network.
However, the real challenge is that a local quantum network has limited value if it cannot connect to other regions. If it remains isolated, communications are restricted only within that local area.
That’s where satellites come in. But simultaneously, those seeking funding for quantum satellites face a dilemma. They can only connect point to point, and there aren’t yet established networks to expand the user base.
So, who goes first? Do we build the satellites, hoping the networks will follow? Or do we build the networks, hoping the satellites will be developed? Nothing will move forward until we demonstrate that the satellite technology is viable.
That’s why proving this technology in space—showing that it is affordable, reliable, and secure—is the first step toward making quantum networks more common and enabling their growth.
QKD technology is not something every person worldwide will use anytime soon. However, if it becomes readily available over the existing fibre optic infrastructure, many applications could benefit from it.
Jacobsen: Cordell, thank you very much for your time today. I appreciate it. Thank you.
Grant: It was fun.
Jacobsen: Excellent. Thank you. Bye.
Grant: Bye.
Last updated May 3, 2025. These terms govern all In Sight Publishing content—past, present, and future—and supersede any prior notices. In Sight Publishing by Scott Douglas Jacobsen is licensed under a Creative Commons BY‑NC‑ND 4.0; © In Sight Publishing by Scott Douglas Jacobsen 2012–Present. All trademarks, performances, databases & branding are owned by their rights holders; no use without permission. Unauthorized copying, modification, framing or public communication is prohibited. External links are not endorsed. Cookies & tracking require consent, and data processing complies with PIPEDA & GDPR; no data from children < 13 (COPPA). Content meets WCAG 2.1 AA under the Accessible Canada Act & is preserved in open archival formats with backups. Excerpts & links require full credit & hyperlink; limited quoting under fair-dealing & fair-use. All content is informational; no liability for errors or omissions: Feedback welcome, and verified errors corrected promptly. For permissions or DMCA notices, email: scott.jacobsen2025@gmail.com. Site use is governed by BC laws; content is “as‑is,” liability limited, users indemnify us; moral, performers’ & database sui generis rights reserved.
#CanadianResearchFunding #quantumEncryption #quantumKeyDistribution #quantumTechnologyInvestment #secureCommunication
🟪 Microsoft 365's July 2025 Updates
🔹 Microsoft's latest updates are here to streamline your organization's experience across platforms! 🚀 Check out these transformative features designed to boost productivity and enhance security.
💡 Tailor your Teams notifications with compact toast sizes for focused work environments.
🔍 Secure your communications with Teams URL validation and Outlook's unverified sender banners.
⚖️ Stay efficient with the new Workflows app for effortless task automation across Microsoft 365.
Explore these game-changing features today and see how they can transform your work dynamics! What are you most excited about?
#Microsoft365 #ProductivityBoost #SecureCommunication #TechUpdates
Take control of your digital sovereignty with Openfire! 🌐
Discover how this open-source, XMPP-based platform for instant messaging, group chat, voice and video calls, and file sharing can secure your data, enhance privacy, and offer unmatched customization. 💬🔐
#DigitalSovereignty #Openfire #DataPrivacy #SecureCommunication
https://www.igniterealtime.org/support/articles/whitepaper_digital_sovereignty.jsp
Launched on June 23, the QUICK³ #nanosatellite is testing components for future #quantumsatellite systems. 🛰️The goal is to enable rapid and secure communication using #quantumtechnology. First results are expected by the end of the year: http://go.tum.de/156580
📷SpaceX
@MunichQuantum
Tuta (@tutaprivacy.bsky.social)
https://bsky.app/profile/tutaprivacy.bsky.social/post/3lpbriaivjs2i
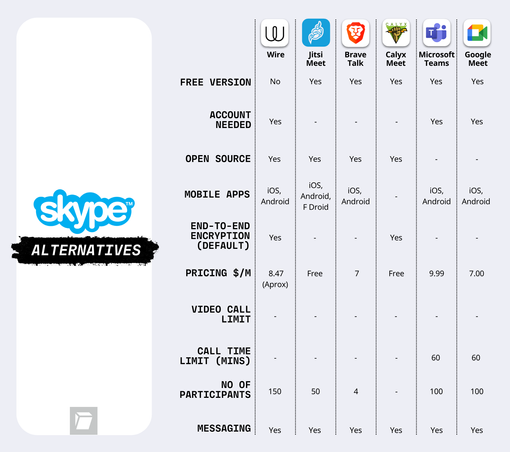
> Now that #Skype has officially shut, It's time for an upgrade.
🙌 Discover secure, privacy-first alternatives to Microsoft Skype for your video calls.
👉 Read more: https://tuta.com/blog/microsoft-skype-video-call-alternatives
#PrivacyMatters #SkypeAlternatives #SecureCommunication #Tuta
Now that #Skype has officially shut, It's time for an upgrade. 🙌
Discover secure, privacy-first alternatives to Microsoft Skype for your video calls.
👉 Read more: https://tuta.com/blog/microsoft-skype-video-call-alternatives
#PrivacyMatters #SkypeAlternatives #SecureCommunication #Tuta
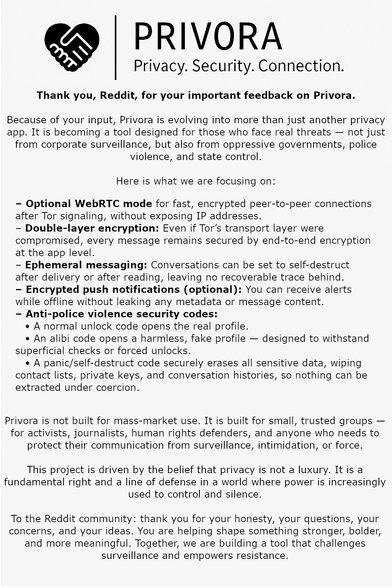
We’re not building just another privacy app.
We’re building a shield — for those facing real threats.
🛡️ For activists.
🕵️♂️ For journalists.
✊ For human rights defenders.
🔥 For everyone resisting surveillance, violence, control.
Privora is small, sharp, and built for trust.
Check the image → all the details.
#Privacy #SecureMessaging #EncryptedMessaging #Tor #WebRTC #CyberSecurity #OnlineSafety #ResistSurveillance #HumanRights #ActivistTools #Journalism #PressFreedom #SecureCommunication
🔓 Discover how anonymous calling works in Resonance!
No phone number, no email, no KYC — just pure privacy with 16 seed words.
🚀 Built by Neuronus, 100% independent, encrypted, and VPN-ready!
🎥 Watch the demo now 👉 https://youtu.be/ox6ftROjnzc
🌐 Try it today at www.resonance.my!
#Privacy #AnonymousCalling #Resonance #Neuronus #SecureCommunication
🐾✨ Behold, the xPal Encrypted Messenger, a majestic fusion of furry dreams and engineering nightmares! 🤖🔧 With the security of a leaky bucket and the elegance of a duct-taped keyboard, it's the perfect choice for those who think JavaScript is a feature, not a requirement. 🙈💻
https://furry.engineer/@soatok/114381133533722007 #xPalMessenger #FurryDreams #EngineeringNightmares #JavaScriptNotRequired #SecureCommunication #HackerNews #ngated
🚨 Messaging Apps Are Failing Your Privacy — Here’s What Comes Next
Ditch the compromises. Resonance by Neuronus Computing delivers next-gen secure messaging with:
🔐 Unbreakable Encryption | 🌐 Decentralized Power| ⏳ Self-Destructing Messages | 💰 Crypto Transactions
Dive into the blog now and see the future of communication.👉
#SecureMessagingApp #PrivateMessaging #EncryptedMessaging #AnonymousChatApp #EndToEndEncryption #CryptoMessagingApp #SecureCommunication #Neuronus