Gratis-Tool: Sicherheitsforscher knacken #ShrinkLocker-#Verschlüsselung | Security https://www.heise.de/news/Gratis-Tool-Sicherheitsforscher-knacken-ShrinkLocker-Verschluesselung-10034933.html #Malware #Ransomware #encryption
#ShrinkLocker
Happy Wednesday everyone!
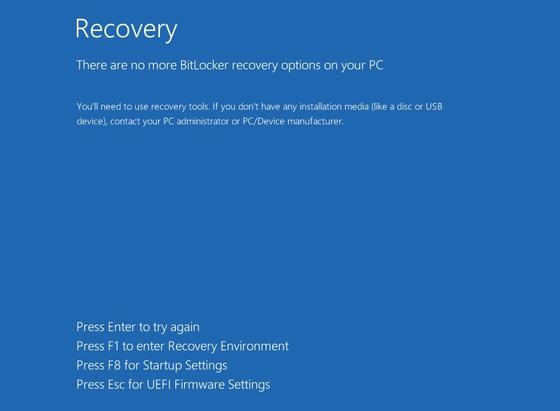
Some good news from the Bitdefender research team! They took a look at the #ransomware strain dubbed #ShrinkLocker and its behaviors and discovered that it abuses a built-in #Windows feature for encryption. It modifies BitLocker (a Windows security feature that encrypts drives to protect data from theft or exposure if a device is lost or stolen) and, if needed, installs it, then re-encrypts the system using a randomly generated password which is delivered to the attacker. Using this feature and paired with Group Policy Objects (GPOs) and scheduled tasks, encrypting an entire network doesn't take much time at all.
The good news: The BitDefender team discovered a window of opportunity for data recovery and have made the decryption tool publicly available. They walk you through the process to recover your data.
Artifacts to hunt for:
Some highlights from the report-
- Look for scheduled tasks that were created that run .vbs scripts and may be in strange locations or have names that are spelled incorrectly or do not match your normal naming convention (if you have one). In this case, "ADHelathCheck" appears that it should have been "ADHealthCheck".
- If scheduled task visibility is an issue, look for svchost.exe being the parent process of abnormal living-off-the-land binaries.
- Monitor RDP connections and identify abuse. This may not be easy but having a baseline or understanding of your environment is paramount.
Well, that is all for now! I hope you enjoy the article and get some good hunts in! Happy Hunting!
ShrinkLocker (+Decryptor): From Friend to Foe, and Back Again
https://www.bitdefender.com/en-us/blog/businessinsights/shrinklocker-decryptor-from-friend-to-foe-and-back-again
Intel 471 #ThreatIntel #ThreatHunting #ThreatDetection #HappyHunting #readoftheday Cyborg Security, Now Part of Intel 471
Bitdefender lanceert decryptor voor shrinklocker ransomware https://www.trendingtech.news/trending-news/2024/11/47544/bitdefender-lanceert-decryptor-voor-shrinklocker-ransomware #ShrinkLocker #Bitdefender #decryptor #ransomware #BitLocker #Trending #News #Nieuws
“Utiliser la fonctionnalité native #BitLocker pour chiffrer des volumes entiers et voler la clé” : quand BitLocker sous #Windows devient un #ransomware ! (#ShrinkLocker)
👉 ShrinkLocker: il nuovo ransomware che sfrutta BitLocker di Windows
Kaspersky scopre ShrinkLocker, un sofisticato ransomware che abusa della funzionalità di crittografia BitLocker di Windows per bloccare l'accesso ai dati
https://gomoot.com/shrinklocker-il-nuovo-ransomware-che-sfrutta-bitlocker-di-microsoft
#bitlocker #blog #kaspersky #news #picks #ransomware #ShrinkLocker #sicurezza #tech #tecnologia
New #ShrinkLocker ransomware uses #BitLocker to encrypt your files
#ShrinkLocker : où comment transformer #BitLocker en #ransomware
Ce n'est pas la première fois que nous voyons BitLocker utilisé pour chiffrer des disques et demander une rançon. Auparavant, les attaquants avaient utilisé cet utilitaire de Microsoft pour chiffrer des systèmes critiques après y avoir accédé et les avoir contrôlés. Dans ce cas, cependant, l'adversaire a pris des mesures supplémentaires pour maximiser les dégâts de l'attaque et empêcher une réponse…
https://antivirus-france.com/shrinklocker-ou-comment-transformer-bitlocker-en-ransomware/