Exhaustive enumeration of Rogue seeds progress:
I've created an S3 bucket full of bitmaps for each room "feature" (currently only position and size), one bit per seed. This will allow reverse lookups -- if we want to find seeds where room 0 has height 6 and width 17, we can AND the corresponding bitmaps and find which bits are set. This is about 231GiB large.
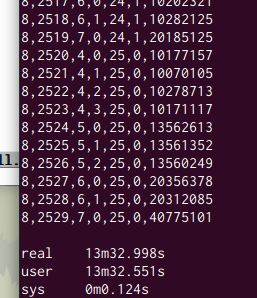
But, the slow part is actually uploading to S3. Running a complete enumeration locally takes less than 14 minutes (and this without any particular effort put into optimization or parallelization!) So building a query engine over this data may not be worth the investment if it only takes that little time to run an exhaustive search.
I'm still thinking of a visualization. There are 2529 possible room configurations so a nice 51x50 grid could plot the relative frequency of each, in each room position. But, this makes large rooms look more probable than they are. (Rogue picks a room size and then places it to fit second, so there are many configurations for small rooms and only one for the largest room.)
However, this is still Rogue(*) not real Rogue. A small variant in which monsters are placed _after_ room creation, not _during_.
#Rogue #ProceduralContentGeneration #BruteForce