@nixCraft That's why #Octo (docs.yottadb.com/Octo) automatically creates indexes as needed. The first time you run a query, it may be slower if it has to create indexes it needs that don't exist (i.e., were not created by other queries). On subsequent times it will just use the available indexes.
#octo
Und nochmal die Konzerte:
21.06.25
#AxelPulgar
#AHorseOfAnotherColour
26.06.25
#WantonStringBand
#Garefowl
29.06.25
#Octo
#LisaTreda
Leider konnte @dasORM nicht spielen, aber trotzdem werde ich mit meinen Freund*innen von AHOAC am 21.6. nach Jahren Pause wieder auf der Bühne stehen.
Ich freu mich drauf!
4/4
CIMB Octo Drops Android 9, iOS 14 Support Starting 25 June 2025 #android #app #apps #banking #cimb #ios #octo #requirements
https://www.lowyat.net/2025/351512/cimb-octo-drops-android-9-ios-14-support-starting-25-june-2025/
CIMB Clicks App Discontinuation Pushed To 19 April 2025 #app #apps #banking #cimb #cimbclicks #clicks #date #discontinuation #octo #postponement
https://www.lowyat.net/2025/347708/cimb-clicks-app-discontinuation-pushed-to-19-april-2025/
Octo would like to wish everyone a #HappyMothersDay. We hope you all have a wonderful day!
#Octocon #Octocon2025 #Fantasy #Scifi #ScienceFictionConvention #Fandom #Octo
Inertia est la bande originale de l'exposition Inertia produite en 2022 au Planétarium Rio Tinto Alcan de Montréal. En Partenariat avec l'UQAM et l'Université Concordia.
“Just as the Earth tends to disappear into the eye of Voyager's optical instruments, our living conditions on Earth deteriorate. I imagine a dialogue between devices that are billions of kilometers apart. Inertia proposes a sonification of the Voyager probes' increasing distance from Earth, but also of data from an environmental probe located east of Montreal, close to the metropolis' petrochemical industrial site...”
Inertia is the soundtrack to the Inertia exhibition produced in 2022 at Montreal's Rio Tinto Alcan Planetarium. In partnership with UQAM and Concordia University.
https://errorishuman.bandcamp.com/album/inertia
#music #art #generative #modularsynth #modular #octo #dataart #data
Julie Sweet, la directrice générale, met fin aux politiques d’inclusion et de diversité chez Accenture.
Nous n’en sommes plus à une menace vague et lointaine d’un avenir déplaisant, ce sont les conséquences concrètes de politiques autoritaires de Trump. Il n’aura fallu que 17 jours pour qu’Accenture se plie aux exigences de Trump et de son administration fasciste.
https://solidaires-octo.com/post/sunset-de-la-diversite-rise-up-des-luttes/
https://blog.octo.com/octo-sopo-care-and-code
ralentir pour avancer mieux, de manière durable et humaine.
Marine Boudeau commence par une évidence qu’on oublie parfois dans le tourbillon des projets : le numérique doit avant tout servir
#octo
BVL Octo Roma Tourbillon Automatic RG-Blue
Bulgari # For Men #Octo Roma Tourbillon # 7AA Premium Collection # Dial Size – 44mm PRECISION AND STYLE FOR YOUR WRIST ❣️ – Working Tourbillon – - 12 Hour Analog – Water Resistant – Skeletal Open Heart Dial – Premium Quality Leather Finish Silicone Strap – Combines the Gun Metal style Case & Brand Embossed Bezel -Back Open With Visible Skeleton Machinery – Dual Heavy clasp Original lock – High Quality & Performance 100%…
https://thewatchemporium.in/shop/watches/bvlgari/bvl-octo-roma-tourbillon-automatic-rg-blue/
BVL Octo Roma Tourbillon Automatic Black-Blue
Bulgari # For Men #Octo Roma Tourbillon # 7AA Premium Collection # Dial Size – 44mm PRECISION AND STYLE FOR YOUR WRIST ❣️ – Working Tourbillon – - 12 Hour Analog – Water Resistant – Skeletal Open Heart Dial – Premium Quality Leather Finish Silicone Strap – Combines the Gun Metal style Case & Brand Embossed Bezel -Back Open With Visible Skeleton Machinery – Dual Heavy clasp Original lock – High Quality & Performance 100%…
https://thewatchemporium.in/shop/watches/bvlgari/bvl-octo-roma-tourbillon-automatic-black-blue/
The @dgarchive team recently found a couple of strange #octo #malware sample that caused problems with jadx, 7zip and other tools.
When I analyzed it, I found out, the Threat Actor set the encrypted flags in the ZIP header, although the content is not actually encrypted. This leads to errors during decryption in analysis tools, while the Android loader seems to just ignore the flag. The sample still runs correctly.
After flipping the encryption bits again, I was able to load the file in jadx. Decompression with 7zip also worked again.
I could not find any posts or articles about this obfuscation technique. It may be brand new. Let me know if you've seen this before!
Samples:
- 3366f1f9057ca8b0734a58cf9b50407556c0dd6792ea0aa589837085e3f25392 (see screenshot)
- 14f577e9cc458b0b47f9e8d6da85130cd290b1a6ebd0804afd92f314a523ae61
- 253f17461d8627a8db2823512a2dbd1a14f0e1721698cdb8f832c313b5b79990
- 0338989191ce53a1a4adf3d4dd5471e470a299f6e8a30b1aa1858e1bc1b5f203
Triage run: https://tria.ge/241028-hde9pstaqj
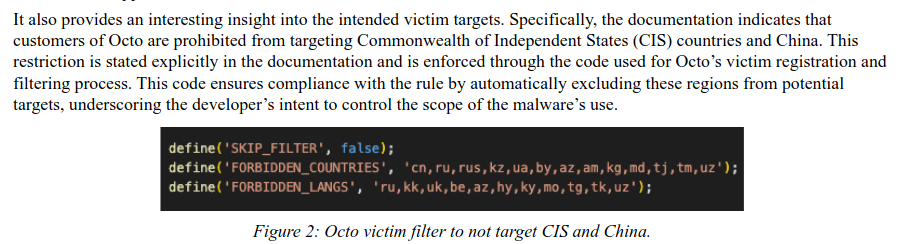
Funny facts from Android/Octo botnet: the documentation stipulates that "customers" of Octo should not attack Commonwealth of Independent States and China:
ref: Octopus Prime: it didn't turn into a truck, but a widely spread Android botnet at @VirusBulletin
The banking trojan, Octo2, now employs a Domain Generation Algorithm (DGA)!
The new variant of the Octo (ExobotCompact) banking trojan, Octo2, is targeting mobile users with several new advanced features. This malware is known for disguising itself as legitimate apps, taking control of the victim’s device to steal sensitive information and commit on-device fraud. For now, the malware has been seen in the wild in Italy, Poland, Moldova, and Hungary, masquerading as apps like NordVPN and Google Chrome. Unfortunately, given its history, it is expected to become global soon.
This new variant, investigated by ThreatFabric, features enhanced functionalities, including a Domain Generation Algorithm (DGA) that dynamically changes its command-and-control (C2) server addresses, making it significantly harder to detect.
Here are some domains associated with this new variant that we have in our collection:
5106c5dbc9e0d004489af35abec41027[.]info
7729f264dc01834757c9f06f2d313e28[.]com
a414602e421935fd057be3c06a3d080c[.]info
53cd7bfaebd095ad083c34f007469ff5[.]biz
5fa5009fb05a5cee1abd7a2dbb6eb948[.]net
8921267492331aabcb4394c801d4e490[.]shop
bbad1dcadd801af41da97ecf292b147f[.]xyz
c80530d100da2e953c21c55d7cb4b86a[.]info
ffce9e39ccdfbe3f1e88806545321ad7[.]org
ThreatFabric report: https://www.threatfabric.com/blogs/octo2-european-banks-already-under-attack-by-new-malware-variant
#dns #cybersecurity #InfobloxThreatIntel #Infoblox #Octo #Octo2 #ExobotCompact #Malware #IOCs #threatintel #cybercrime #infosec #dga #c2 #Trojan
BVL Octo Roma Black Chronograph Quartz Grey
BVLGARI # For Him # ETA QUALITY #Octo Finissimo Chronograph > Grey Dial With Black Chronograph Needles >Working 24Hour Stop Watch & Anolog * Stainless steel Silver case * Rust Free Stainless Steel Silver Bezzel & Case * Glare Proofed mineral crystal glass •Water Resistant Body Pure Stainless steel Chain Chain With ORIGINAL LOCK HEAVY QUALITY 100% ORIGINAL JAPANESE QUARTZ MACHINERY ❤️
https://thewatchemporium.in/shop/watches/bvlgari/bvl-octo-roma-black-chronograph-quartz-grey/
CIMB Clicks To Be Gradually Wind Down Starting August 2024 #app #banking #cimb #cimbclicks #octo
https://www.lowyat.net/2024/327649/cimb-clicks-wind-down-august-2024/
The #Octo #Tempest group adds #RansomHub and #Qilin #ransomware to its arsenal
https://securityaffairs.com/165811/cyber-crime/octo-tempest-ransomhub-qilin-ransomware.html
#securityaffairs #hacking
CIMB To Implement SecureTAC Approval For All Online Fund Transfers By Month’s End #apps #banking #cimb #clicks #octo #securetac #security #transfers
https://www.lowyat.net/2024/325287/cimb-securetac-fund-transfer-june-24s/