🎁 Holiday Gift or Holiday Grift?
As we head toward the season of giving, it seems we've been on the receiving end of some tempting offers on luxury brand items including bags and watches.
"Step right up, bargains galore!?"
✉️ Unsolicited emails flaunting tempting deals with subjects like:
- [Black Friday 2025] Elevate Every Moment – Luxury Watches from $250
- [Black Friday 2025] Elevate Your Style – Louis Vuitton Bags from $200
🔗 Links in these emails use punycode (xn--) internationalized domain names, with Cyrillic text unrelated to the brand they impersonate.
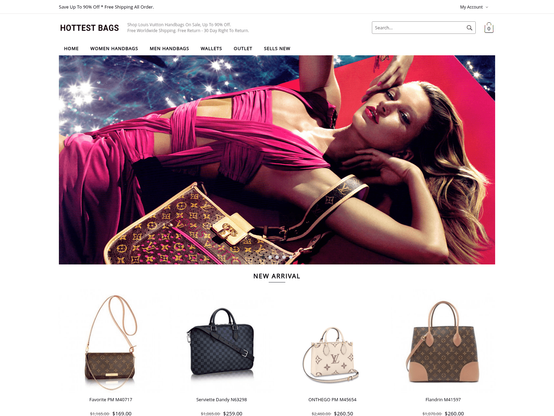
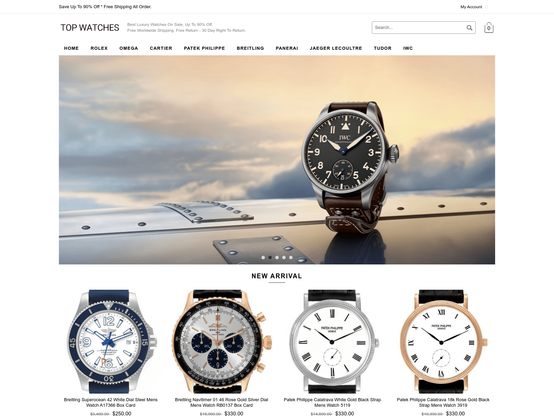
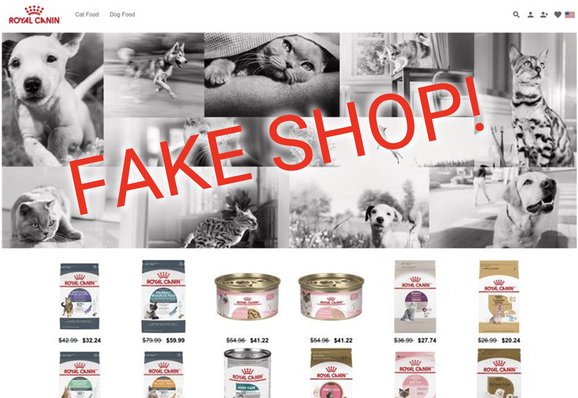
➡️ These domains redirect to, or load resources from, a handful of '.com' domains that do a reasonable job of mimicking the sleek style of luxury brand websites.
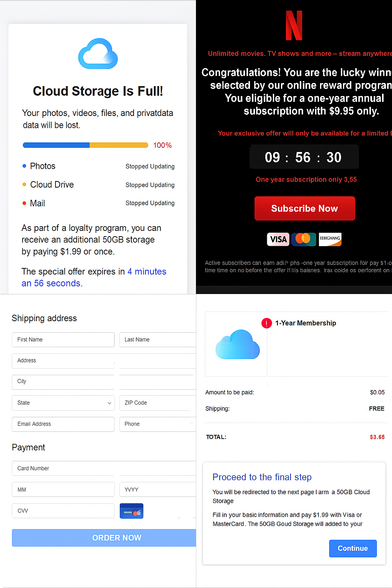
💰 As in our earlier post, the checkout process is a familiar tale - passing your PII and payment card details through an intermediate domain which attempts to take payment via a legitimate payment gateway.
Email punycode/IDN examples:
🚫 xn--80aaae9btead2a[.]xn--p1ai
🚫 xn--80aclvcqeaduhb[.]xn--p1ai
🚫 xn--90ahaa0atead2a[.]xn--p1ai
🚫 xn--90askabadrf6a[.]xn--p1ai
Redirect/resource examples:
🚫 lsrox[.]com
🚫 lux-lvs[.]com
Payment intermediate example:
🚫 topcccbook[.]online
Tempted to treat a loved one, or 'bag' yourself a bargain? Whether it's a knockoff or nothing at all, 'watch' out - the only thing you'll be unwrapping is another scam!
#dns #threatintel #threatintelligence #cybercrime #cybersecurity #infosec #infoblox #infobloxthreatintel #scam #blackfriday #thanksgiving #holidays
![Screenshot of a Steam profile where the username contains the domain 3pq[.]cc and the profile picture contains epk[.]cc](https://files.mastodon.social/cache/media_attachments/files/115/231/834/574/955/781/small/0b11f97aabb6a12c.png)