#OperationEndgame3: 1025 Server von Netz genommen | Security https://www.heise.de/news/Operation-Endgame-3-1025-Server-von-Netz-genommen-11077049.html #OperationEndgame #Malware #Infostealer #Botnet #Elysium #VenomRAT #Rhadamanthys
#operationendgame
Major APT activity, AI-enabled attacks, GitHub credential leaks, and global takedowns (Rhadamanthys, VenomRAT, Elysium) dominate this week’s cybersecurity landscape.
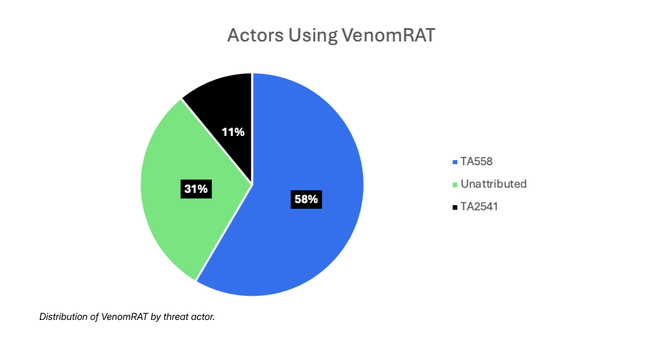
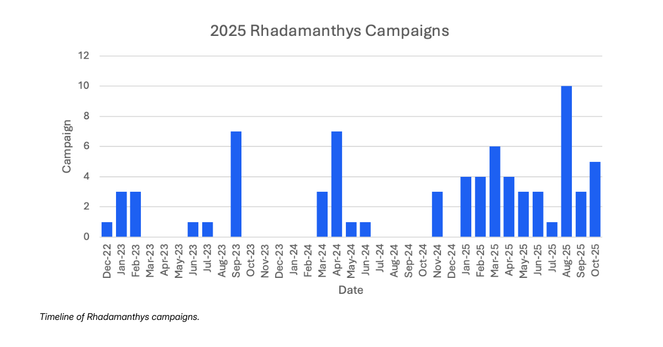
Operation Endgame 3.0 disrupted major components of three malware ecosystems - Rhadamanthys, VenomRAT, and the Elysium botnet.
1,025+ servers were taken down across 11 countries with support from more than 30 cybersecurity organisations.
A rare example of coordinated action targeting the infrastructure layer of cyber-crime: botnets, RATs, and infostealers.
What’s your assessment - sustained impact or short-term setback?
Follow for more threat-intel updates.
#infosec #ThreatIntel #OperationEndgame #Malware #BlueTeam #IncidentResponse #CyberDefense #TechNadu
Operation Endgame
Gestern noch den Counter veröffentlicht, heute ist das Ergebnis verfügbar: In einer koordinierten Einsatzphase der Operation Endgame, die vom Europol-Hauptquartier in Den Haag aus gesteuert wurde, wurden die Infostealer‑Plattform Rhadamanthys, der Remote‑Access‑Trojaner VenomRAT und das Botnet Elysium vollständig zerstört, sagt Europol.
Mehr: https://maniabel.work/archiv/209
#Botnet #infosec #infosecnews #Europol #OperationEndgame #BeDiS
Police take down three cybercrime operations in latest round of ‘whack-a-mole’
🔥 Operation Endgame 3.0 is here! This phase targets the notorious information and credential stealer #Rhadamanthys. It's another major international effort that’s seen 1,025 servers taken down and 20 domains seized. 💪
👏 Excellent work by @Europol and all partners involved — the takedown of Rhadamanthys marks a significant win for the global cybersecurity community.
As with earlier phases of #OperationEndgame, Spamhaus is providing remediation support. Those affected will be contacted in due course with guidance on next steps.
Operation Endgame website 👉 https://www.operation-endgame.com
Europol press release ⤵️
https://europol.europa.eu/media-press/newsroom/news/end-of-game-for-cybercrime-infrastructure-1025-servers-taken-down
#OperationEndgame: Authorities shut down infrastructure for Rhadamanthys Infostealer, VenomRAT and the Elysium botnet, seize 1025 servers and arrest one key suspect.
Read: https://hackread.com/operation-endgame-rhadamanthys-venomrat-elysium-malware/
#CyberCrime #Malware #Rhadamanthys #Infostealer #CyberSecurity
Proofpoint is proud to have assisted law enforcement in the #OperationEndgame investigation that led to the November 13, 2025 disruption of #Rhadamanthys and #VenomRAT, both #malware used by multiple cybercriminals.
• Rhadamanthys: https://brnw.ch/21wXs1N
• VenomRAT: https://brnw.ch/21wXs1O
---
Since May 2024, Operation Endgame—a global law enforcement and private sector effort that includes Proofpoint—has significantly disrupted the #malware and #botnet ecosystem.
👉 #Europol called the May 2024 Operation Endgame actions “the largest ever operation against botnets.”
👉 In May 2025, additional malware families and their creators, including #DanaBot, were taken down.
---
Each disruption forces threat actors to adapt and invest time and resources to retool their attack chains.
With our unique visibility and leading detection capabilities, Proofpoint researchers will continue monitoring the threat landscape and provide insight into the biggest cyber threats to society.
BKA & internationale Partner stoppen Rhadamanthys und VenomRAT – Operation Endgame erschüttert Cybercrime-Ökosystem
And it's out!
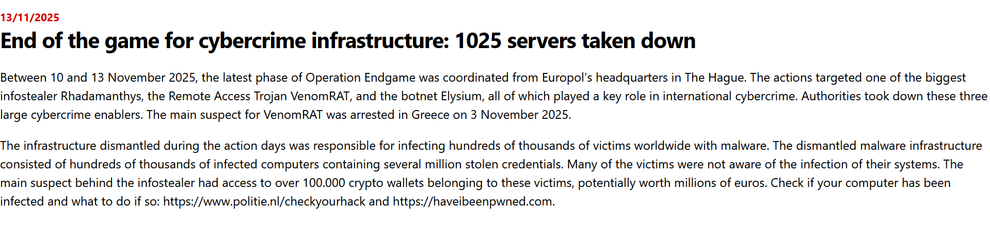
End of the game for cybercrime infrastructure: 1025 servers taken down
Between 10 and 13 November 2025, the latest phase of Operation Endgame was coordinated from Europol’s headquarters in The Hague. The actions targeted one of the biggest infostealer Rhadamanthys, the Remote Access Trojan VenomRAT, and the botnet Elysium, all of which played a key role in international cybercrime. Authorities took down these three large cybercrime enablers. The main suspect for VenomRAT was arrested in Greece on 3 November 2025.
#OperationEndgame #rhadamanthys #infostealer #VenomRAT #Elysium
Less than 10 minutes left on the Operation Endgame's counter. Wonder what they gonna announce. Maybe just the takedown of rhadamanthys infostealer infra.
Rhadamanthys Infostealer’s TOR infrastructure goes offline in apparent law enforcement takedown - possibly tied to Operation Endgame.
https://www.technadu.com/rhadamanthys-infostealer-infrastructure-disrupted-in-apparent-law-enforcement-takedown/613164/
#CyberSecurity #Rhadamanthys #Infostealer #LawEnforcement #OperationEndgame
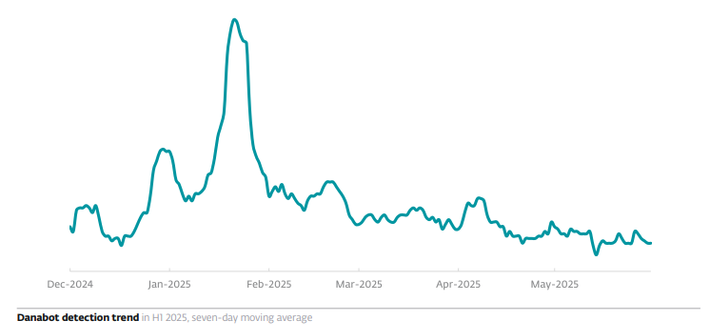
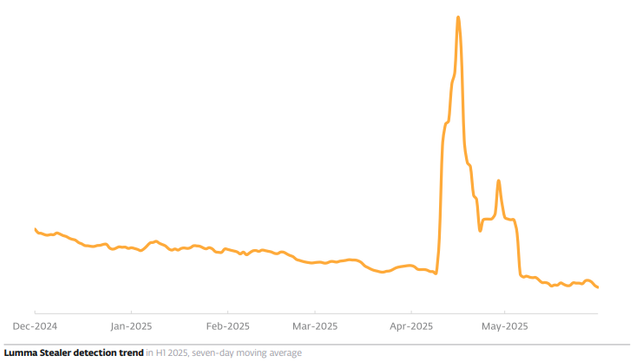
In May 2025, #ESET participated in operations that largely disrupted the infrastructure of two notorious infostealers: #LummaStealer and #Danabot.
As part of the Lumma Stealer disruption effort, carried out in conjunction with Microsoft, BitSight, Lumen, Cloudflare, CleanDNS, and GMO Registry, ESET supplied technical analysis and statistical information.
Danabot was targeted by the #FBI and #DCIS, alongside #OperationEndgame led by #Europol and #Eurojust. ESET participated together with several other companies. We provided the analysis of the malware’s backend infrastructure and identified its C&C servers.
Before these takedowns, both infostealers were on the rise: in H1 2025, Lumma Stealer detections grew by 21%, while Danabot’s numbers increased by more than 50%.
For a time, Lumma Stealer was the primary payload of HTML/FakeCaptcha trojan, used in the #ClickFix social engineering attacks that we also cover in this issue of the #ESETThreatReport. In recent months, we have seen Danabot being delivered via ClickFix as well.
For more details on these two operations and on the ClickFix attacks, read the latest #ESETThreatReport: https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
#OperationEndgame: Behörden zerschlagen #Antivirus-Testseite #AVCheck | Security https://www.heise.de/news/Operation-Endgame-Behoerden-zerschlagen-Antivirus-Testseite-AVCheck-10422496.html #CyberCrime #Malware #OperationEndgame2
🚨 Authorities just dismantled major malware evasion services used by cybercriminals! Operation Endgame took down AVCheck & more, striking at the heart of cybercrime tools that help malware dodge antivirus defenses. Huge win for cybersecurity! 🔒🌐
Read more: https://cyberinsider.com/authorities-take-down-malware-evasion-services-used-by-cybercriminals/
#CyberSecurity #OperationEndgame #Malware #LawEnforcement #AVCheck #newz
📬 AVCheck zerschlagen: Behörden schlagen zu, Szene rüstet nach
#Malware #Rechtssachen #AVCheck #CounterAV #Cybercrime #DarknetTools #FBI #MalwareTesting #OperationEndgame https://sc.tarnkappe.info/60983a
Fahndung BKA:
»Vitalii Nikolaevich KOVALEV (oder: Vitaly Nikolayevich, Vitaliy Nikolayevich) steht im Verdacht, als Gründer der Gruppierung hinter der Schadsoftware #Trickbot einen wesentlichen Tatbeitrag zur Durchführung von globalen Cyberattacken geleistet zu haben.«
🇷🇺 #Stern #OperationEndgame
bka.de/DE/IhreSicherh...
Global operation dismantles DanaBot malware network, indicting 16 and recovering $50M+ in losses. #Cybersecurity #DanaBot #OperationEndgame
More details: https://cyberscoop.com/danabot-malware-botnet-seizure-takedown - https://www.flagthis.com/news/15679
#DanaBot botnet disrupted, #QakBot leader indicted: #OperationEndgame, mounted by law enforcement and judicial authorities from the US, Canada and the EU, continues to deliver positive results by disrupting the DanaBot botnet and indicting the leaders of both the DanaBot and Qakbot Malware-as-a-Service operations. (May 2025)
🌐🚨 Grote klap voor cybercriminelen! 300 servers en 650 domeinen in beslag genomen tijdens #OperationEndgame. Samen staan we sterk tegen ransomware! 💪🔒 #Cybersecurity
https://itinsights.nl/cybersecurity/hackers-ontwricht-300-servers-vernietigd-in-epische-slag/