Whew! It took two attempts but the #Synacktiv team successfully exploited the #ChargePoint EV Charger and demonstrated signal manipulation over the connector. They are off to the disclosure room to go over how they did it. #P2OAuto #Pwn2Own
#synacktiv
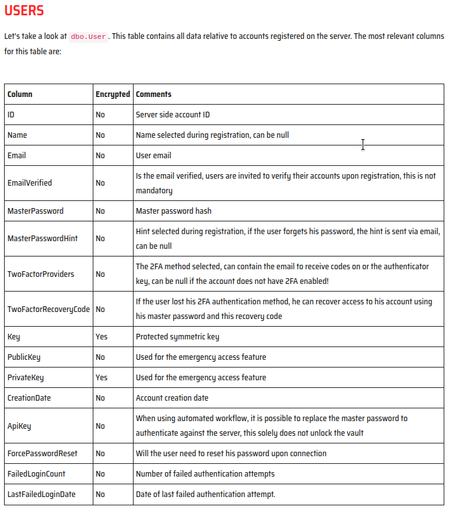
Forensic analysis of bitwarden self-hosted server
https://www.synacktiv.com/en/publications/forensic-analysis-of-bitwarden-self-hosted-server
Today, our #WebPKI session 😍
If you weren't sleeping during the last decade, you know that @letsencrypt and #CertificateTransparency (CT) have revolutionized web security ⚡️
#pts24 will welcome no less than:
- Aaron Gabble, #techlead at @letsencrypt
- Philippe Boneff, #techlead of #Google CT team
- and an offensive research by Kévin Schouteeten & Paul Barbé from #Synacktiv on certs issuance in managed K8s env.
IMHO, you shouldn't miss this session!
👉 REGISTER https://pretix.eu/passthesalt/2024/
“0-Click RCE on the Tesla Infotainment Through Cellular Network” https://www.synacktiv.com/sites/default/files/2024-05/tesla_0_click_rce_cellular_network_offensivecon2024.pdf #synacktiv #tesla
2 public holidays in a row here in France 😎
👉 What about taking your #free seat at @passthesaltcon ?
⚡️ Attend 21 talks and 9 workshops given by experts from @letsencrypt #Google @quarkslab #Synacktiv
etc
⚠️ Not sure there's enough for everyone!
SPONSOR
Next, we continue our tour by warmly welcoming #Synacktiv as a #pts23 Silver sponsor! 💙
We are **really** grateful to the company for supporting us since 2019 🙏
#Synacktiv provides you Security services (audits, pentests ...), security products, trainings and CSIRT services.
On the FLOSS side, @Synacktiv ninjas often audit Free Software projects as CVE-2023-22809 found on Sudo has recently proved it 👍
Ref : https://www.synacktiv.com/sites/default/files/2023-01/sudo-CVE-2023-22809.pdf
@0xMitsurugi the offsec session of @passthesaltcon usually provided at approx. 75% by ... #synacktiv 😅
The #Synacktiv team succeeds in exploiting a #Canon printer, however, they used a bug previously seen in the contest. They win $5,000 and 1 Master of Pwn point.
Canon patched the heap overflow vulnerability in CADM service in ~2 months. Honestly, that's impressive. #pwn2own2021 #BlackAlps22 #synacktiv
Corporate website with nice articles relaunches. Of course the RSS feed goes 404.
You wouldn't expect any response after complaing about the missing feed, but in case of #synacktiv the CEO actually answered 👏 .
Please provide more RSS/Atom feeds!