Fuzz your cargo-fuzz harness with LibAFL!
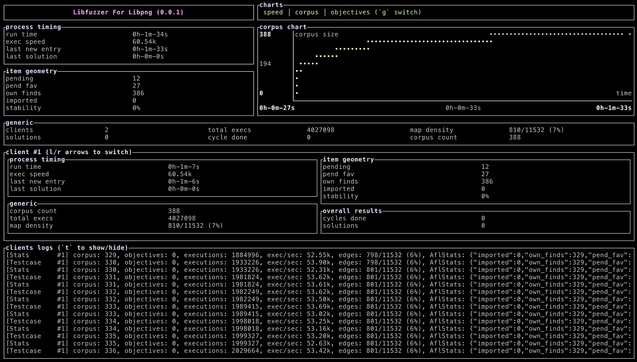
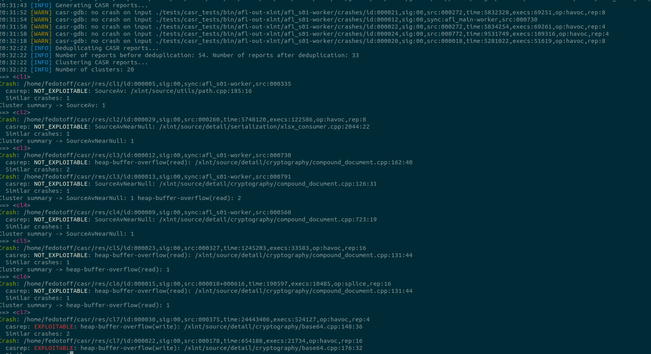
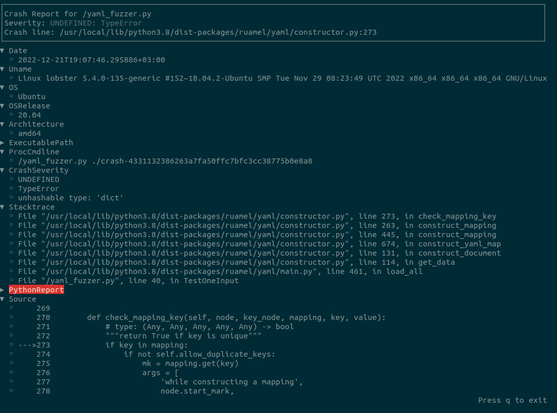
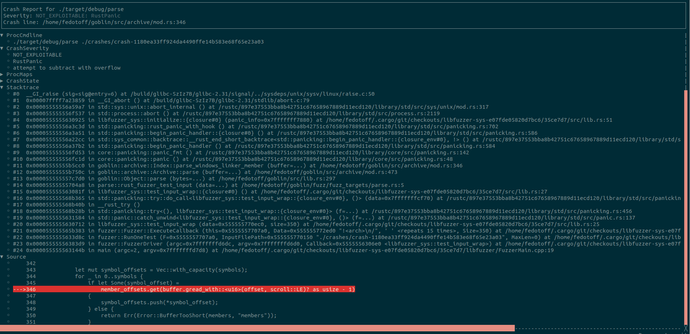
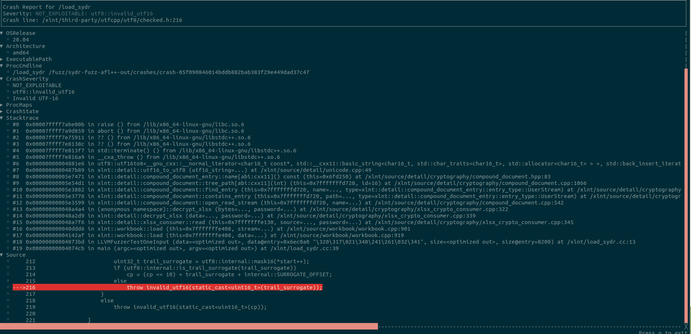
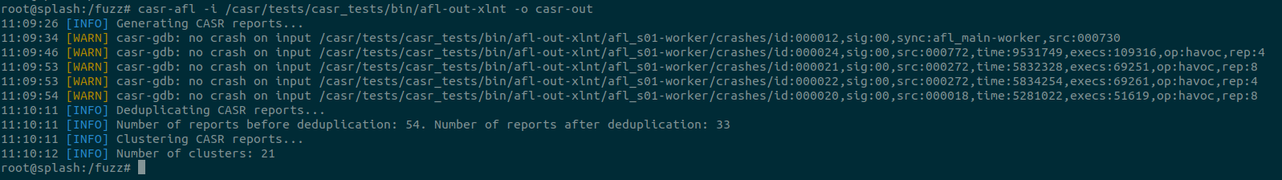
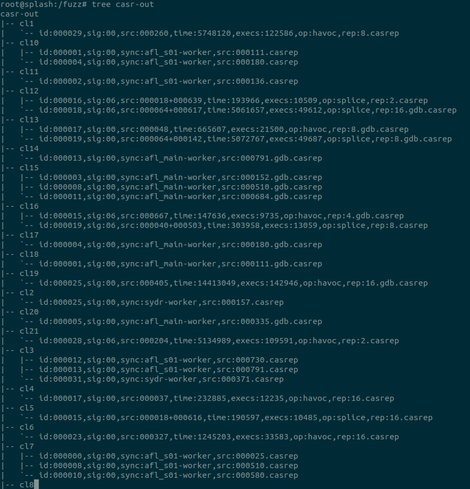
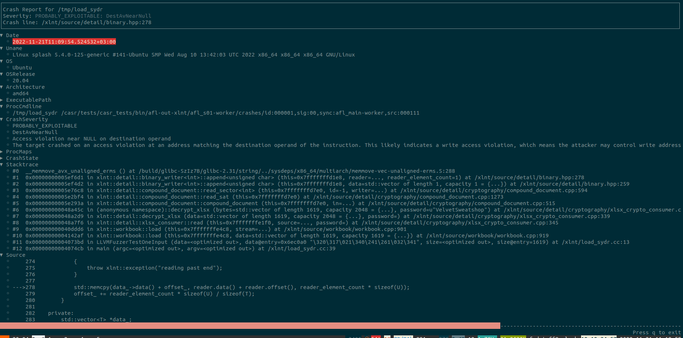
I'm happy to share the fuzz runtime described in our recent FUZZING'23 report, CrabSandwich, which expands on libafl_libfuzzer to allow for Rust support. This allows Rust developers to switch away from the now-in-stasis libFuzzer to a LibAFL-based runtime which supports most common features of libFuzzer seamlessly.
Want to try it out for yourself? Simply edit your existing cargo-fuzz harnesses' Cargo.toml to change the libfuzzer-sys dependency as shown here: https://github.com/rust-fuzz/cargo-fuzz/issues/330#issuecomment-1592911175
In most cases, the entire edit is a single-line change (!). At this time, we only support Linux, but are looking for contributions to expand to Windows and macOS as well.
Happy hunting! #fuzzing #rust #libafl #AFLplusplus