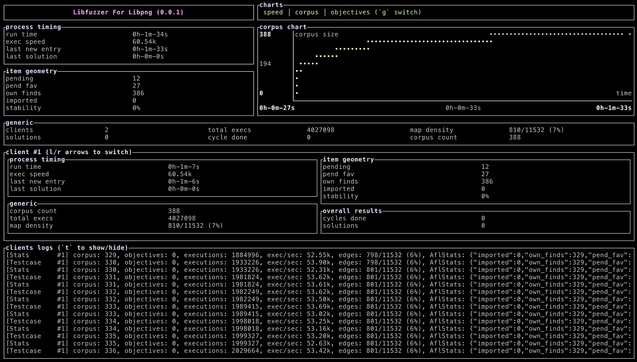
Want to learn how to build your own #libafl components, but never had the right project? Try working through the interactive exercises that I released today: https://github.com/addisoncrump/parking-game-fuzzer
You'll work through building your own LibAFL components with templates, allowing you to understand them progressively through the context of trying to solve "Tokyo Parking" (AKA Thinkfun's "Rush Hour") puzzles with fuzzing.
#fuzzing #aflplusplus #puzzles #rust #rustlang
#aflplusplus
Guess who just released #LibAFL 0.15.3?
That's right, you all did! (thank you☺️)
Highlights:
- better forkserver
- scriptable Lua mutations
- SIMD performance in stable rust
- CmpLog and RISC-V for LibAFL_Unicorn
- TMin for LibAFL_QEMU
- Updated Sugar for easy fuzzing
🚨 LibAFL 0.15.2 🚨
- Rust 2024 edition
- LibAFL_Unicorn
- Use LibAFL rand types for other crates
- Allow logging to StatsD
- LibAFL_QEMU updates like binary-only ASan in Rust 🦀🦀🦀, inputs via StdIn, better snapshots
And so much more:
is there a simple way to have the target binary dump it's own test-case while running from afl-fuzz #aflplusplus #afl++ - the thing is, the target binary generates some crypto keys at the start which are used later. i thought to have persistent mode first generate the internal state, then dump the message that is basis for fuzzing and that later in processing needs those keys. but when i run afl-fuzz it complains that the input directory is empty, and when i write the file it's not picked up...
Late last year we released #LibAFL 0.11.2
Highlights:
- Unicode-preserving mutators, better mutations for text!
- GSoC project: Nicer TUI
- Scalability introspector
- Improved libafl_frida
- Extended libafl_qemu - added CmpLog and more!
Full changelog:
https://github.com/AFLplusplus/LibAFL/releases/tag/0.11.2
If you want to play with the injection vulnerability detection feature shown at #37c3: for AFL++ read instrumentation/README.injections.md; for libafl_qemu check out the vhqemu branch and use fuzzers/qemu_launcher with "-y injections.yaml". #aflplusplus #afl #fuzzing #fuzzing-tools
Fuzz your cargo-fuzz harness with LibAFL!
I'm happy to share the fuzz runtime described in our recent FUZZING'23 report, CrabSandwich, which expands on libafl_libfuzzer to allow for Rust support. This allows Rust developers to switch away from the now-in-stasis libFuzzer to a LibAFL-based runtime which supports most common features of libFuzzer seamlessly.
Want to try it out for yourself? Simply edit your existing cargo-fuzz harnesses' Cargo.toml to change the libfuzzer-sys dependency as shown here: https://github.com/rust-fuzz/cargo-fuzz/issues/330#issuecomment-1592911175
In most cases, the entire edit is a single-line change (!). At this time, we only support Linux, but are looking for contributions to expand to Windows and macOS as well.
Happy hunting! #fuzzing #rust #libafl #AFLplusplus
Almost a year after my defense, my PhD thesis "Automated Security Testing of Unexplored Targets Through Feedback-Guided Fuzzing" is now archived on the university server. 🎉
We fuzzed Nvidia drivers, tcp servers, basebands, WebAssembly,...
Enjoy reading :)
https://depositonce.tu-berlin.de/items/c3aaf2ec-8036-4651-a609-9c3b11a7f705
Finally came around to do some #fuzzing on #sectxtlib with #AFLplusplus and directly found an issue in one of its dependencies 🔥
@anfedotoff @aflplusplus Very cool!
I had the same realization and created a multi-fuzzer utility for Rust at work (@srlabs), using #AFLplusplus #honggfuzz and #libfuzzer in parallel.
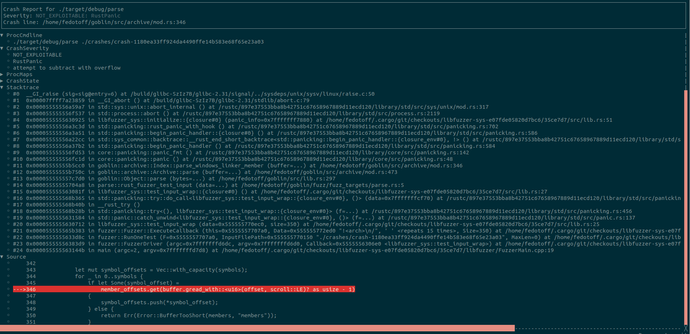
New casr 2.4.0 is available!
https://github.com/ispras/casr/releases/tag/v2.4.0
casr-cli now provides a joint statistics all over reports!
casr-afl now copies crashes next to reports, produces casr reports in parallel and prints casr-cli joint statistics!
#casr #AFLplusplus
LibAFL 0.9.0 is out with a new logo🔥
Highlights:
→ QEMU user-mode and system-mode snapshot fuzzing
→ Stable CorpusId when removing/updating entries in Corpus
→ Tinyinst binary-only instrumentation
→ Full support to AFL++ binaries with forkserver
...
Checkout new #casr 2.3.0 release!!!
https://github.com/ispras/casr
- rust panic support in casr-san/casr-gdb
- c++ exceptions support in casr-san/casr-gdb
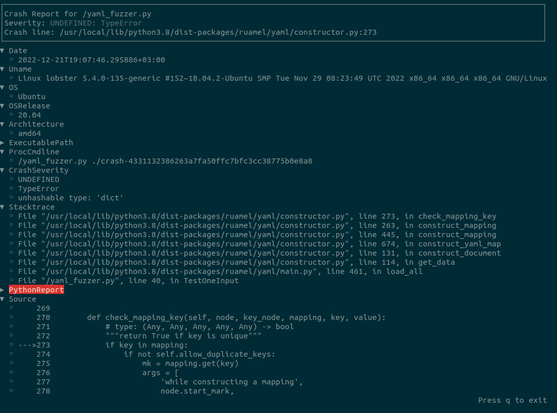
- casr-python for creating CASR reports from python crashes🔥
P. S. Merry Christmas! ❄️❄️❄️
#fuzzing #afl #aflplusplus #python
I have a YouTube channel where I talk about fuzzing, please like subscribe and share:
https://youtube.com/@MrHardik05
#fuzzing #vulnerability #afl #AFLplusplus #libfuzzer #winafl #jackalope #honggfuzz
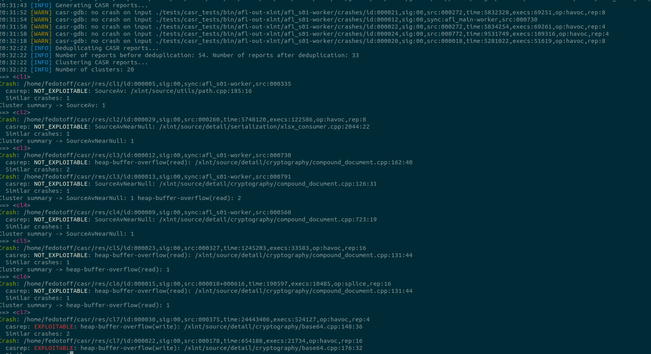
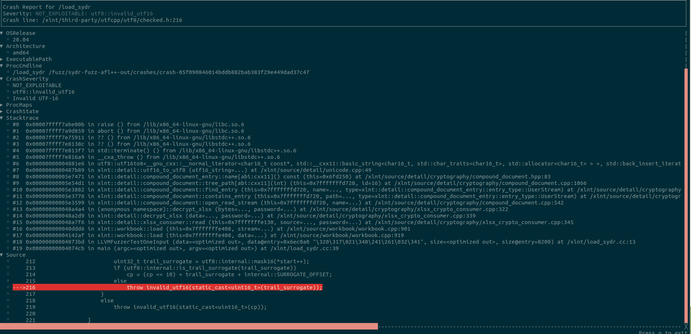
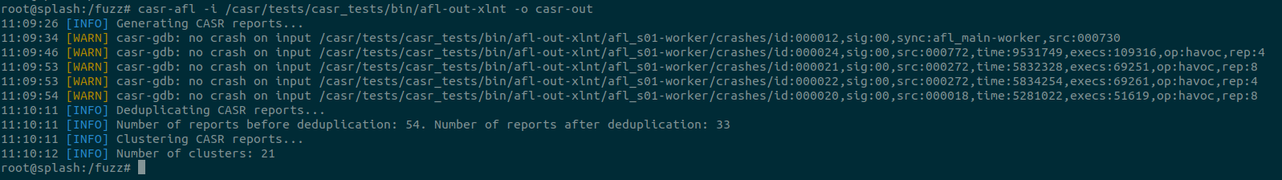
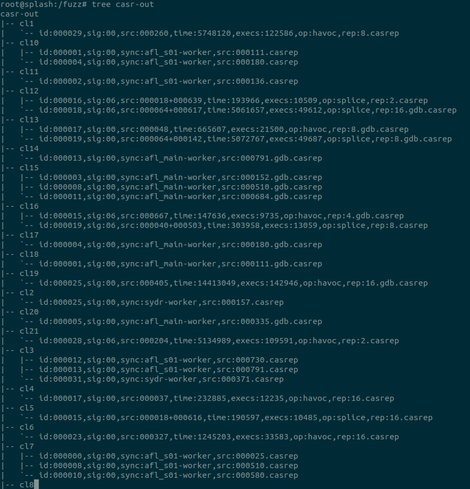
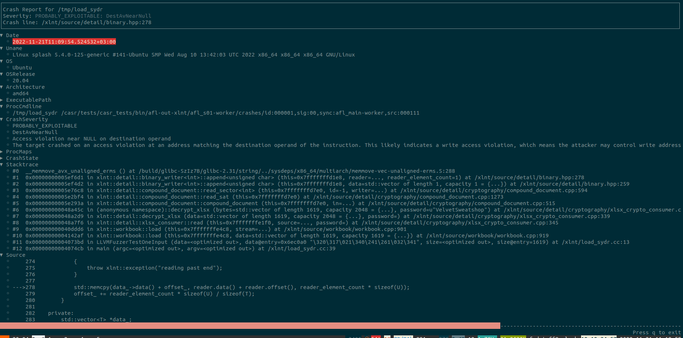
At last, new casr 2.2.0 release with casr-afl!!!
Triaging crashes found by @aflplusplus as simple as it could be:
$ cargo install casr
$ casr-afl -i afl-out -o casr-out
$ casr-cli casr-out/cl1/<report_name>
For binary-only emulation in #LibAFL qemu, you can now dump DrCov traces to see in #idapro (lighthouse), #binaryninja (bncov), or #ghidra (dragondance) which paths the executions took.
This helps you understand where your fuzzer gets stuck, develop the harness further, and reach greater depth in the binary, eventually.
Binary-only modes of #AFLplusplus ( #qemu / #frida ) and libafl_frida also support DrCov output, already.
#fuzzing #fuzzingTips
https://github.com/AFLplusplus/LibAFL/pull/878