🚀✨ Oh wow, look out programmers, #fuzzing is going to magically make all your porting dreams come true by automating everything with #LLMs – because who needs human skill when you can have a robot write your code, right? 🤖📜 But sure, let's trust the same clarity you get after a couple of beers. 🍻🥴
https://rjp.io/blog/2025-06-17-unreasonable-effectiveness-of-fuzzing #automation #programming #future #tech #humor #HackerNews #ngated
#fuzzing
The Unreasonable Effectiveness of Fuzzing for Porting Programs
https://rjp.io/blog/2025-06-17-unreasonable-effectiveness-of-fuzzing
#HackerNews #Fuzzing #Porting #Programs #Technology #Software #Development #Cybersecurity
Fuzzing WebSockets for Server‑Side Vulnerabilities
Research reveals a technique using the Backslash Powered Scanner extension to fuzz WebSocket endpoints and find server‑side bugs.
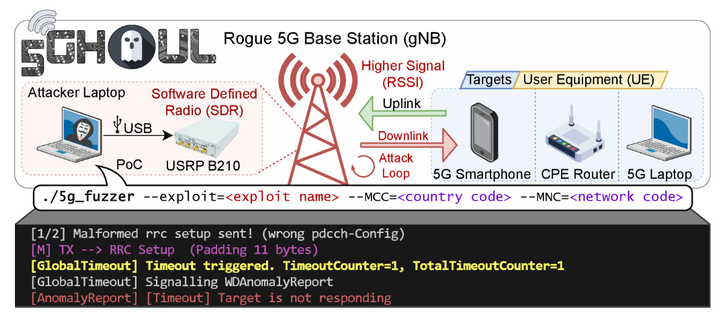
5Ghoul - 5G NR Attacks & 5G OTA Fuzzing:
(project): https://github.com/asset-group/5ghoul-5g-nr-attacks
(paper): https://asset-group.github.io/papers/5Ghoul.pdf
#telecom #infosec #cybersecurity #fuzzing #ota #5g #smartphones #mobile #mobilesecurity
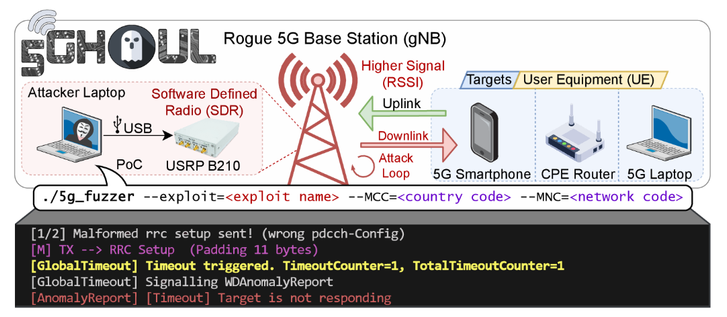
5Ghoul - 5G NR Attacks & 5G OTA Fuzzing:
(project): https://github.com/asset-group/5ghoul-5g-nr-attacks
(paper): https://asset-group.github.io/papers/5Ghoul.pdf
#telecom #infosec #cybersecurity #fuzzing #ota #5g #smartphones #mobile #mobilesecurity
Elige qué gobierno totalitario ciberatacar
https://youtu.be/ye9ytwCcBeI
#hacking #hackintools #fuzzing #nmap #informatica #redes #totalitarismo #gobierno #dictaduras #tiranos
High-Performance Network Fuzzing with LibAFL and libdesock
Custom fuzzer using LibAFL and libdesock achieves 42x speedup over AFLNet via tokenized inputs and shared memory, uncovering new bugs.
https://lolcads.github.io/posts/2025/05/high_performance_network_fuzzing/
Attacking #EDRs Part 4: #Fuzzing Defender's Scanning and Emulation Engine (mpengine.dll)
https://labs.infoguard.ch/posts/attacking_edr_part4_fuzzing_defender_scanning_and_emulation_engine/
So, what's next for fuzzing CPython with fusil?
The results point to interesting future ideas, including expanding fuzzing to new environments like subinterpreters, using more tools like Thread Sanitizer, and developing more advanced fuzzing techniques.
A huge thank you to everyone who contributed!
And thank you for reading!
P.S.: if you have a C/Rust extension, we can fuzz it too: https://mastodon.social/@danzin/114383188014599269
(5/5)
One finding I really like is the bug discovery pattern.
There wasn't a steady stream of bugs, but spikes of findings: 1st, a huge number of crashes as I started testing a CPython that hadn't been fuzzed by fusil in a decade.
Later, a new wave of issues tied to the addition of new features to the fuzzer, like support for "weird classes" and typing objects.
So periodic campaigns may have better cost-benefit than continuous fuzzing.
(4/5)
The credit for fusil's effective design goes all to Victor Stinner (@vstinner), who created it nearly two decades ago. It was responsible for finding release blockers way back in 2008. I just contributed a little to revive and enhance it.
Some enhancements included running generated code in threads and adopting new "interesting" objects and values as inputs, helping to discover more crashes.
(3/5)
All this was only possible due to the great response from the Python community.
Thanks to the developers efforts to triage, diagnose, and fix the problems, the campaign became a collaborative effort to improve Python.
The impact was considerable, mobilizing Core Devs and contributors to create 98 PRs to fix these bugs. The average time to fix an issue was about 20 days, with a median of just five days.
(2/5)
Happy to share the results of a fuzzing campaign targeting CPython that ran from Oct 2024 to May 2025. Using the fusil fuzzer, the goal was to find crashes and improve CPython's robustness.
I really like the results we got: the effort uncovered 52 unique crash-related issues. These reports approached 30% of all "type-crash" issues filed during that period. One of the crashes was classified as a Release Blocker, that was a nice result! :)
(1/5)
So, my technical report on fuzzing CPython with fusil is almost done.
I'd really appreciate some help categorizing the found issues by relevance/severity/importance or any other name for impact.
Do you have the chops to help with that? And do you have time and interest? Please get in touch if so! And please boost if you can :)
A plot, some tables, links to the report and some discussion are available in this thread:
https://discuss.python.org/t/feedback-on-the-recent-fusil-fuzzing-campaign-of-cpython/91737
Guess who just released #LibAFL 0.15.3?
That's right, you all did! (thank you☺️)
Highlights:
- better forkserver
- scriptable Lua mutations
- SIMD performance in stable rust
- CmpLog and RISC-V for LibAFL_Unicorn
- TMin for LibAFL_QEMU
- Updated Sugar for easy fuzzing
https://labs.infoguard.ch/posts/attacking_edr_part4_fuzzing_defender_scanning_and_emulation_engine/
Great to see snapshot #fuzzing successfully applied to another AV product!
Breaking the Sound Barrier Part I: Fuzzing CoreAudio with Mach Messages
Explores fuzzing macOS CoreAudio's Mach IPC to uncover sandbox escape vulnerabilities
https://googleprojectzero.blogspot.com/2025/05/breaking-sound-barrier-part-i-fuzzing.html
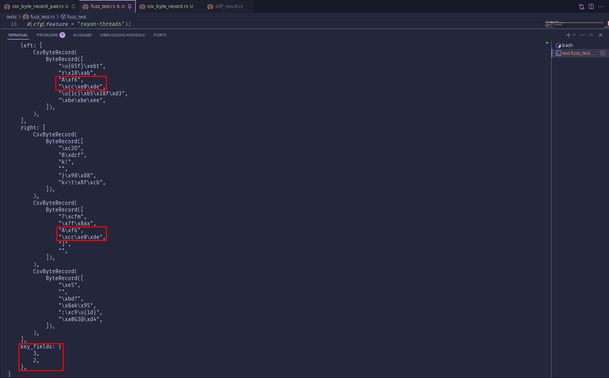
#Fuzzing along in #CSVDiff :awesome:
In the second screenshot I've highlighted some interesting parts:
Key field indices are 2 and 3, so when diffing the records, where key fields are highlighted, they'll be compared as `Modify`, because:
- key fields are equal between left and right record
- other fields are unequal between left and right record
The other two records on the right have no corresponding left record - so those are `Add`ed records
Breaking the Sound Barrier Part I: Fuzzing CoreAudio with Mach Messages
https://googleprojectzero.blogspot.com/2025/05/breaking-sound-barrier-part-i-fuzzing.html
#HackerNews #BreakingTheSoundBarrier #Fuzzing #CoreAudio #MachMessages #CyberSecurity #ProjectZero