WRT #libfuzzer deprecation: the official alternative uses out-of-process fuzzing, which means the fuzzer doesn't run in the same process as the target.
This is what the original #AFL fuzzer does, as well.
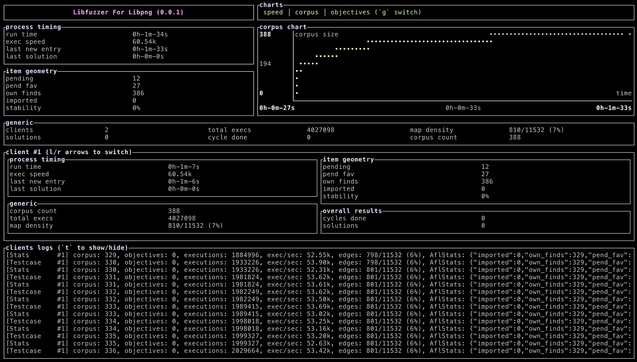
It turns out that this doesn't scale well, thanks to IPC overhead and context switches for _every single _ testcase (of which you can reach millions per second of).*
We spent years creating good in-process fuzzing with #LibAFL, trying to match the success of libfuzzer, and it's sad to see the OG in-process fuzzer get depreciated in favour of an (IMHO) technically inferior alternative.
This may be a good engineering choice if you don't care about CPU cost and have an almost infinite amount of CPUs to spare.
The amount of companies worldwide that has a virtually infinite amount of CPU cores to spare for #fuzzing is low.
There are multiple ways to bring fuzzing to the masses, but this is not the one I would pick.
*the one reason where out-of-process fuzzing is favorable is for crashing targets. Instead of slowly restoring your state, you can simply respawn the target. However, most fuzzing campaigns are over when crashes are found.