APT24's Pivot to Multi-Vector Attacks | Google Cloud Blog
LinkAPT24 攻擊手法轉變:多向量入侵的進化與臺灣目標
https://security.googleblog.com/2025/11/threat-intelligence-apt24-pivot-to-multi.html
📌 Summary:
本文由 Google Threat Intelligence Group (GTIG) 分析來自中國境內長期活躍的 APT24 威脅組織,揭露其三年多的持續網絡間諜活動。APT24 主要透過自製的高度混淆惡意程式 BADAUDIO 進行初期下載,並演進出多元化傳遞方式,尤其針對臺灣的組織展開供應鏈攻擊及針對性魚叉式釣魚。BADAUDIO 採用 AES 加密與先進流程扁平化混淆技術,透過 DLL 側載與注入方式在目標系統內建立持續控制。APT24 從早期廣泛的網站策略性入侵,逐步轉向供應鏈攻擊,鎖定臺灣地區一數百家企業,並結合雲端儲存平臺進行隱蔽分發。Google 針對受害網站與企業發出通報,並將相關網域、檔案加入 Safe Browsing 黑名單,強化使用者保護。此案例反映中國境內威脅組織持續提升攻擊技巧與韌性,展現出高度適應性和多層次滲透能力,提醒資安防禦必須針對多種攻擊管道同步佈署監控與防範。
🎯 Key Points:
→ ★ BADAUDIO 惡意程式
- 自製 C++ 一階下載器,利用 AES 加密傳輸與解密載荷(如多次見到的 Cobalt Strike Beacon)
- 採用控制流程扁平化混淆技術,阻礙逆向工程與行為分析
- 一般以 DLL Search Order Hijacking (MITRE ATT&CK T1574.001) 方式注入執行,搭配 VBS、BAT 等輔助檔建立持續性
- 收集主機簡易資訊(主機名、使用者、系統架構),將其加密後於 Cookie 傳送,伺服器以此辨識被駭系統
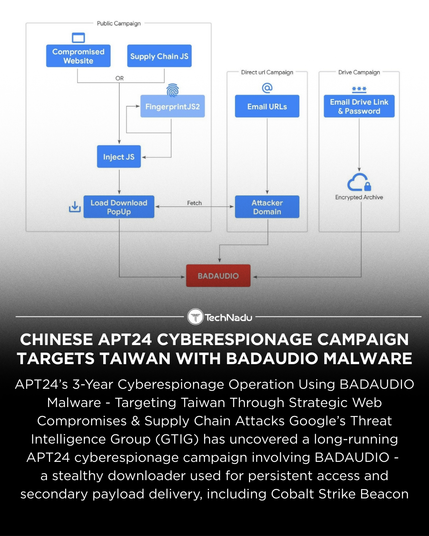
→ ★ 傳遞管道演變
① 2022 年開始以策略性網站入侵注入惡意 JavaScript,運用 FingerprintJS 收集訪客指紋
② 僅針對特定 Windows 使用者顯示偽造的下載提醒誘使安裝 BADAUDIO
③ 2024 年起持續鎖定臺灣地區,重複入侵一間區域數位行銷公司供應鏈,影響涵蓋逾 1,000 個網站
④ 供應鏈惡意程式碼偽裝成常用 JavaScript 函式庫,並採用高混淆手法隱藏在供應商的 JSON 檔案中
⑤ 2025 年針對特定域名進行定製化的載入邏輯,短暫取消限制而廣泛感染,顯示攻擊者調配攻擊影響範圍的策略運用
→ ★ 魚叉式釣魚與雲端資源濫用
- 多個策略配合雲端硬碟(Google Drive、OneDrive)散佈加密壓縮檔,利用知名平臺增加信任度
- 魚叉郵件中植入像素追蹤確認目標開信狀況,精準鎖定有效標的並強化攻擊效率
- Google 採取防護動作攔截相關郵件,減緩攻擊傳播
→ ★ 防禦與因應
- GTIG 即時通報受害企業並提供技術細節協助修補
- 威脅指標(IOC)納入 Google Safe Browsing,提升整體網路使用安全
- 研究強調中國境內威脅組織持續使用隱蔽性策略以規避偵測,資安防禦需要同步強化多層防護與監控
🔖 Keywords:
#APT24 #BADAUDIO #供應鏈攻擊 #魚叉式釣魚 #網路間諜