For hobbyist Cobalt Strike Beacon collectors, note that the recently announced 4.11 update introduces a number of changes to frustrate Beacon configuration extraction, namely through the new `transform-obfuscate` field.
When set, this field can apply multiple layers of encoding, encryption and compression (with some recent Beacons observed with a 32 byte XOR key, configurable upto 2048 bytes!).
While still reasonably trivial to decode manually, standard automated workflows (say, through the SentinelOne parser) will now fail, not least because of changes to the well-known field markers.
Beacons with these characteristics have thus far been observed with watermarks indicative of licensed instances, though I imagine it is only a matter of time before the 4.11 capabilities become accessible to all manner of miscreants.
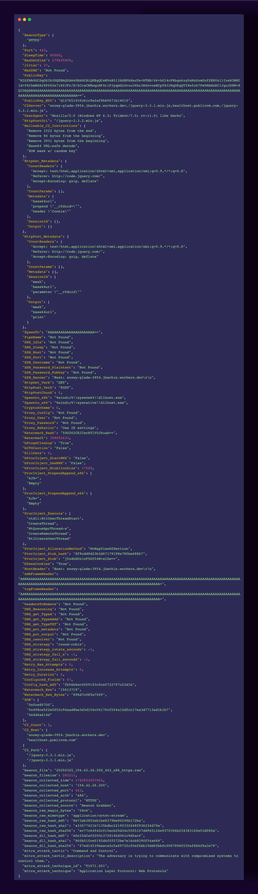
A sample configuration, via a staged Beacon on 104.42.26[.]200 is attached, including the three distinct XOR keys used to decode it.
https://www.cobaltstrike.com/blog/cobalt-strike-411-shh-beacon-is-sleeping
#cobaltstrike #malwareanalysis #forensics #blueteam