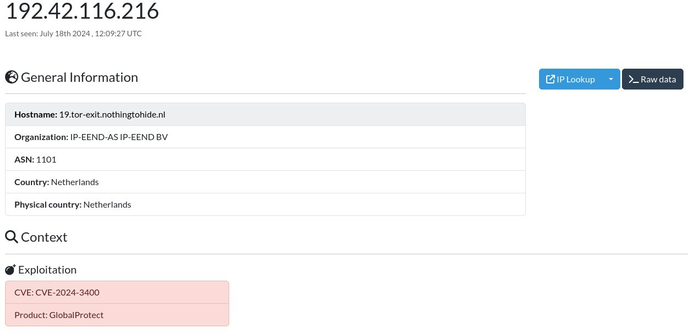
Palo Alto Networks and Unit 42 are actively tracking and sharing information about a critical vulnerability, CVE-2024-3400, which affects their PAN-OS software. This vulnerability allows an unauthenticated attacker to execute arbitrary code with root privileges on the firewall. It has a CVSS score of 10.0, indicating a high severity. The vulnerability is specific to PAN-OS 10.2, 11.0, and 11.1 versions when a GlobalProtect gateway and device telemetry are enabled. It does not impact cloud firewalls, Panorama appliances, or Prisma Access.
Palo Alto Networks has identified malicious exploitation of this vulnerability under the name Operation MidnightEclipse. They believe the initial exploitation is limited to a single threat actor but warn that additional actors may attempt to exploit it in the future. The company is providing interim guidance to mitigate the vulnerability, including recommendations for customers with a Threat Prevention subscription to block attacks by enabling Threat ID 95187. For those who cannot apply this mitigation immediately, Palo Alto Networks suggests temporarily disabling device telemetry until the device is upgraded to a fixed PAN-OS version.
The vulnerability is set to be fixed in an upcoming release of PAN-OS 10.2, 11.0, 11.1, and all later versions, with an estimated release date of April 14, 2024. Palo Alto Networks encourages customers to monitor their networks for abnormal activity and investigate any unexpected network activity as a best practice. They also thank Volexity for discovering this issue and their ongoing collaboration and partnership.
https://unit42.paloaltonetworks.com/cve-2024-3400/
https://www.volexity.com/blog/2024/04/12/zero-day-exploitation-of-unauthenticated-remote-code-execution-vulnerability-in-globalprotect-cve-2024-3400/
#cybersecurity #paloaltonetworks #unit42 #panos #vulnerability #firewall #globalprotect #cve #midnighteclipse #threat #volexity
![A popup notification from GlobalProtect saying "Host checks are completed, and your computer is in compliance with [company] standards." Interactable parts of the popup include a "More Notifications" link, an "OK" button, and a "X" to close.](https://files.mastodon.social/media_attachments/files/114/189/839/791/988/744/small/3bdd49aa0562511c.png)