🚨 𝗝𝗦𝗚𝘂𝗟𝗱𝗿: 𝗠𝘂𝗹𝘁𝗶-𝗦𝘁𝗮𝗴𝗲 𝗟𝗼𝗮𝗱𝗲𝗿 𝗗𝗲𝗹𝗶𝘃𝗲𝗿𝗶𝗻𝗴 𝗣𝗵𝗮𝗻𝘁𝗼𝗺𝗦𝘁𝗲𝗮𝗹𝗲𝗿
TL;DR: We identified #JSGuLdr, a multi-stage JavaScript-to-PowerShell loader used to deliver #PhantomStealer. A JScript file triggers PowerShell through an Explorer COM call, pulls the second stage from %APPDATA%\Registreri62, then uses Net.WebClient to fetch an encrypted payload from Google Drive into %APPDATA%\Autorise131[.]Tel. The payload is decoded in memory and loaded, with PhantomStealer injected into msiexec.exe.
⚠️ The chain combines obfuscation, cloud-hosted payloads, COM-based execution, and fileless in-memory loading, making it difficult to detect with automated or static detection solutions.
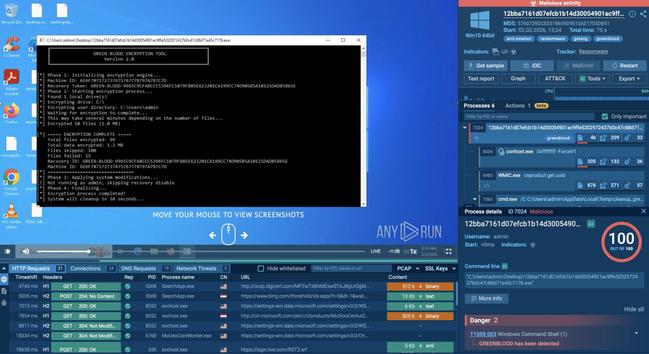
Execution chain: wscript.exe ➡️ explorer.exe (svchost.exe) ➡️ explorer.exe (COM) ➡️ powershell.exe ➡️ msiexec.exe
👨💻 See analysis session: https://app.any.run/tasks/7b295f6f-5f16-4a44-a02b-5d59fd4b1e8f/?utm_source=mastodon&utm_medium=post&utm_campaign=jsguldr&utm_term=201125&utm_content=liktoservice
Stage 1️⃣: The sample is an obfuscated JScript script signed with a fake Authenticode certificate to bypass trust checks. It builds an encrypted PowerShell string and writes it to %APPDATA%\Registreri62, forming the second stage.
Through Shell.Application and Explorer COM interaction, the script launches powershell.exe under explorer.exe, masking the execution chain as normal user activity.
🎯 TTPs: Obfuscation (T1027), Signed binary proxy execution (T1553.006), COM interaction (T1559.001), Proxy execution via explorer.exe (T1218)
Stage 2️⃣: The PowerShell code decodes and runs %APPDATA%\Registreri62, reconstructing hidden commands (iex) and loading a new payload from Google Drive. The file is saved as an encrypted container for the third stage.
🎯 TTPs: Encrypted payload download (T1105), Cloud storage abuse (T1105), Local file staging (T1074.001)
Stage 3️⃣: Autorise131[.]Tel acts as an on-disk container for an in-memory payload.
The same PowerShell process decodes it, extracts bytes, and executes the result through Invoke-Expression, running PhantomStealer filelessly in memory.
The payload is injected into msiexec.exe, enabling PhantomStealer to steal data.
🎯 TTPs: Fileless execution (T1059.001), Reflective .NET module loading (T1620), Process injection (T1055), Proxy execution via msiexec.exe (T1218.007)
🔍 Track similar activity and pivot from IOCs using this TI Lookup search query: https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=jsguldr&utm_content=linktoti&utm_term=201125#%7B%2522query%2522:%2522commandLine:%255C%2522windowssystem32%255C%2522%2520and%2520imagePath:%255C%2522explorer.exe%255C%2522%2522,%2522dateRange%2522:180%7D
#IOCs:
URL: hxxps://drive[.]google[.]com/uc?export=download&id=1gUB_fKBej5Va_l3ZSEXk_7r5Q4EeJuwd
Files: %APPDATA%\Registreri62, %APPDATA%\Autorise131[.]Tel
CMD: powershell.exe "$Citize=$env:appdata+'\Registreri62';$Guazuma=gc $Citize;$Aristape=$Guazuma[4460..4462] -join ''"
🚀 Gain fast detection and full visibility with #ANYRUN. Sign up: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=jsguldr&utm_term=201125&utm_content=register#register
#cybersecurity #infosec