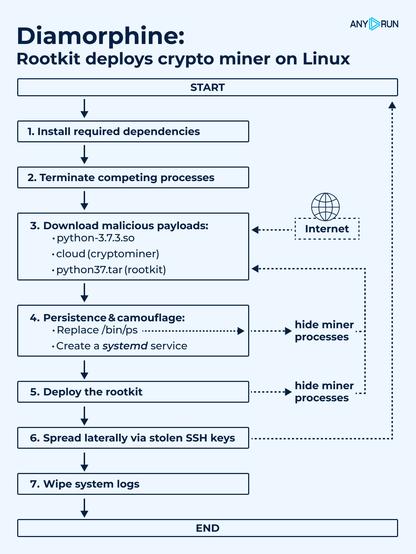
🚨 Hunting #SheByte PhaaS Platform: The LabHost Successor
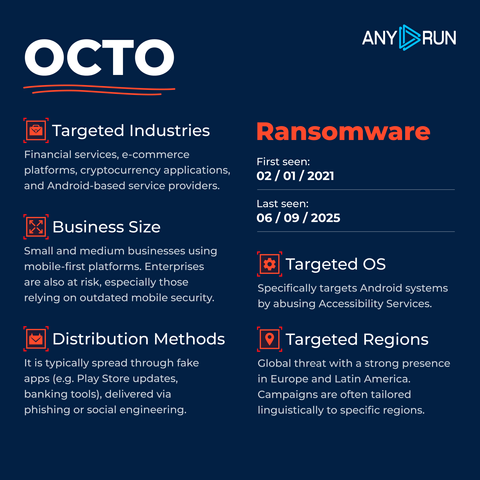
🎯 This #PhaaS targets major banks in Canada and USA, including Interac, delivery services, telecom, toll roads. It also extends to Coinbase, popular email providers like Yahoo, Gmail, and Outlook, and impersonates brands such as Bell, Apple, and Amazon.
Following the #LabHost takedown in early 2024, SheByte operators are working to fill the gap by promoting their platform via Telegram and releasing major updates:
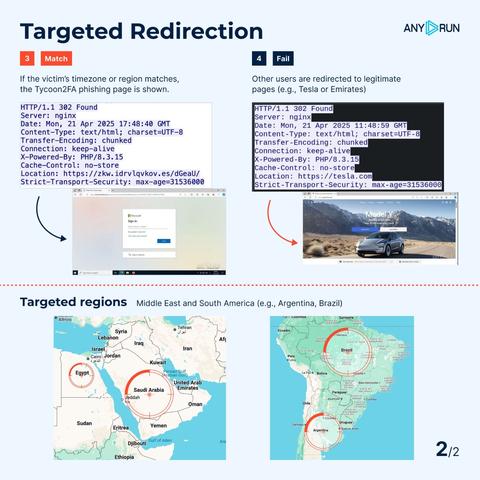
🔹 Geofiltering: prevents access to the phishing page from outside the targeted regions.
🔹 Connection Type Filtering: restricts VPN, hosting, mobile.
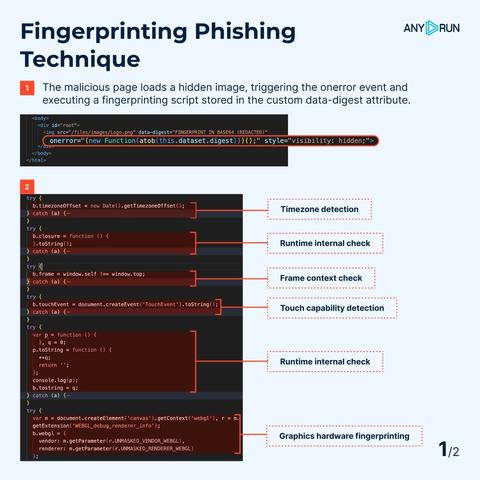
🔹 Fingerprint Detection: detects bots and sandboxes.
🔹 Enhanced Control of Page Flow: enables real-time control over the victim’s interaction flow.
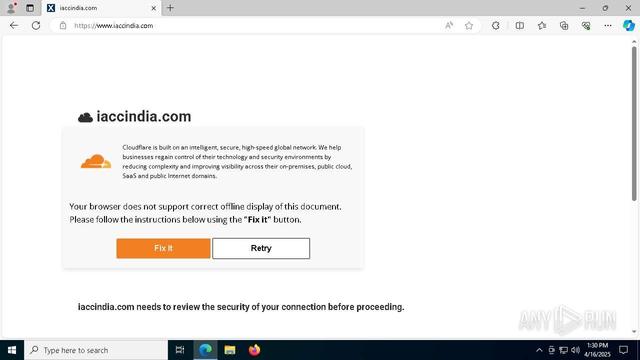
🔹 V2 Page Builder: phishing page builder that mimics legitimate sites, adds custom data-stealing forms, and requires no coding skills.
🔗 Execution chain:
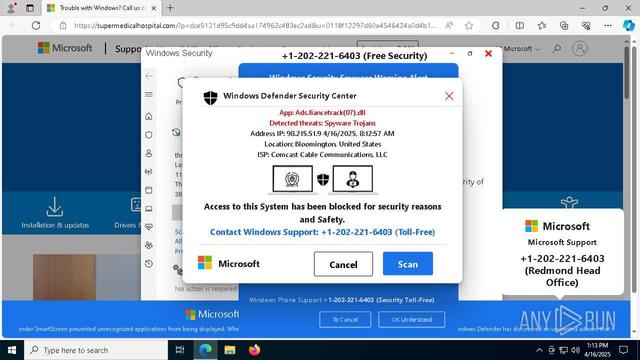
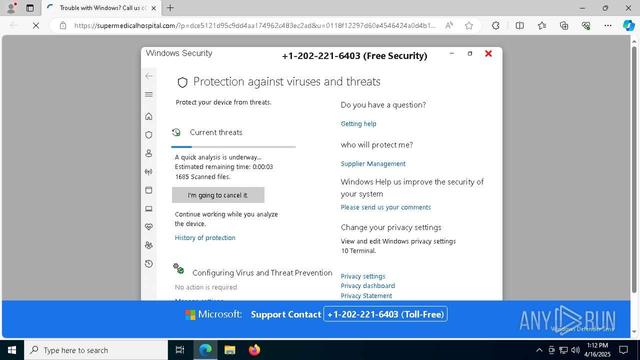
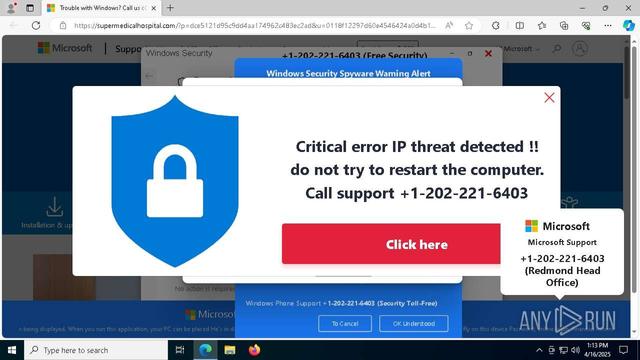
Phishing link ➡️ Fake bank login page ➡️ Credential harvesting ➡️ OTP interception ➡️ Security question capture ➡️ Redirect to legitimate bank site
👨💻 With #ANYRUN Sandbox, analysts can explore the phishing kit functionality available through the phishkit's admin panel: https://app.any.run/tasks/56ddc9be-3d32-405e-a53b-33b90640602e/?utm_source=mastodon&utm_medium=post&utm_campaign=shebyte&utm_content=linktoservice&utm_term=300425
Explore captured and detonated phishing site samples, most likely created using the SheByte phishing builder:
https://app.any.run/tasks/2b23cac6-fe32-4ac8-8f60-1a4758eaf711/?utm_source=mastodon&utm_medium=post&utm_campaign=shebyte&utm_content=linktoservice&utm_term=300425
https://app.any.run/tasks/6aacde46-d7e8-47a1-b2bf-606137c46bd8/?utm_source=mastodon&utm_medium=post&utm_campaign=shebyte&utm_content=linktoservice&utm_term=300425
https://app.any.run/tasks/d39f8b11-b228-4a52-9c4e-3a07fb745f26/?utm_source=mastodon&utm_medium=post&utm_campaign=shebyte&utm_content=linktoservice&utm_term=300425
🔍 These #phishkits often include data collection forms. Victims are tricked into entering sensitive information, which is sent directly to the attacker. This behavior can be used as a hunting pivot:
🔹 /file/db_connect<digits?>.php + request body parameters: name=
🔹 /t3chboiguru<digits?>.php + request body parameters: usr= psd=
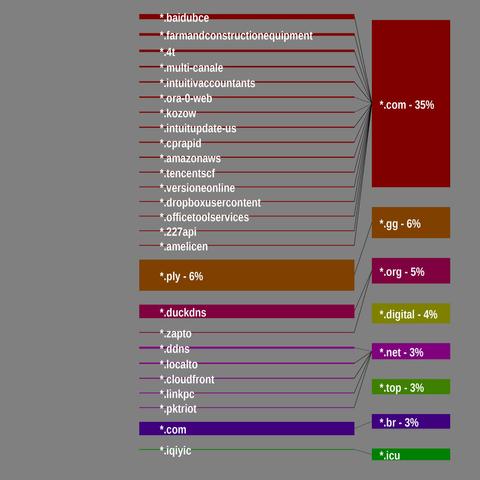
📌 Indicators and patterns for hunting SheByte-related infrastructure:
CSS file hashes:
🔹 SHA256: 58d0a27afc6ed22f356c907579f15f41f120c913c118837dba9c1b8da13a5a4f
🔹SHA256: bc054fd38e88a7c9c1db08bd40dfe7ad366fa23efdce184e372d2adb431c91d2
Reverse DNS reused across multiple phishing-related domains:
🔹 my1[.]bode-panda[.]shop
Favicon of FIRST Bank loaded from a non-legitimate domain:
🔹 SHA256: 6e18a721d5559f569e5a6585bb6430c1965788e4607ea6704601872de8168811
🔹 Legitimate domain: bankatfirst[.]com
A URL request chain with a low number of HTTP requests in the session:
🔹 /personal.html
🔹 /otp.html
🔹 /c.html
#IOCs:
172[.]93[.]121[.]9
162.241[.]71.139
172.93[.]120.134
santosjjax[.]com
ghreo[.]net
cractil[.]net
sitygma[.]net
👨💻 SheByte Admin Dashboards:
www[.]lillliiilllliiiiilliilllllllliiii[.]site
jonathanserhan[.]shebyte[.]io
Analyze and investigate the latest #malware and phishing threats with #ANYRUN 🚀